Backups are a critical component of a data protection plan. In the face of disasters, having multiple copies of data can be the difference between recovery and failure. That’s why the 3-2-1 rule is so popular: it says that you should have three copies of data, on two different media, with one copy stored offsite. However, with the increasing threat of ransomware in today’s IT landscape, the 3-2-1 rule is no longer enough to ensure that your data is protected. The addition of immutability and monitoring is critical to keeping your data safe from malicious attacks. In this blog, we’ll explore how you can upgrade the 3-2-1 rule with immutability and monitoring to keep your data safe from ransomware and other threats.
The 3-2-1 Rule for Backups
The 3-2-1 rule is a widely adopted backup strategy that states that to ensure recoverability in the face of disaster, you need to have 3 copies of data, on 2 different medias, with 1 copy offsite. This rule is a good starting point for businesses looking to protect their data. By having three different copies, businesses can recover from a range of disasters, whether it’s a hardware failure, natural disaster or data corruption.
Why the 3-2-1 backup rule needs to be updated
However, with the continued threat of ransomware in today’s IT landscape, the 3-2-1 rule needs to be updated to meet the challenges that businesses face. Ransomware is a type of malware that encrypts files on a computer, making them inaccessible until a ransom is paid.
With a 94% increase in ransomware attacks in the health sector, it is imperative that businesses take extra steps to protect their backups from malicious attacks.
Importance of immutability in ransomware protection
One way to upgrade the 3-2-1 rule is to add immutability as an added element to the strategy.
Immutability refers to the inability to change or modify data. By having a copy of data that is offline and/or immutable, businesses can ensure that at least one copy is locked from being changed or deleted. This is crucial in protecting data from malicious attacks, such as ransomware.
Additionally, having a monitoring tool in place that ensures immutability is enabled and has not been modified adds an extra layer of protection to the data.
Protecting Backups from Malicious Attacks
Adding an immutable storage option
The 3-2-1 rule for backups is an established strategy that ensures recoverability in the event of a disaster. However, with the threat of ransomware attacks increasing in today’s IT landscape, it is necessary to evolve this rule to keep data safe from malicious attacks.
One of the key elements of this evolution is to add an immutable storage option to the mix. This option prohibits backups from being altered or deleted, ensuring that at least one copy of data is protected from unauthorized changes.
There are three ways IT managers can add immutability to a backup environment:
- Add a purpose-built immutable backup appliance, such as the StoneFly DR365V Veeam-ready backup and DR appliance or the StoneFly Veeam-Immutable Veeam Air-Gapped (VIVA) air-gapped and immutable appliances.
- Repurpose unused/idle storage space and set up immutable file and immutable S3 object lockdown using storage virtualization engines such as StoneFly’s SCVM.
- Integrate immutable cloud, file and object, storage volumes with services such as StoneFly Veeam cloud connect which includes the complete package from Veeam licenses, and management gateway to immutable repositories in Azure, AWS, and StoneFly private cloud.
Monitoring backups with visibility tools
While adding an immutable storage option provides a level of protection for backups, there is always the risk that someone with unauthorized access can enter the environment and disable or change the immutability period.
To mitigate this risk, it is important to have visibility into the data center and the backups themselves. Monitoring tools such as the Veeam ONE, can help provide this visibility and ensure that backups are protected from malicious activity.
Benefits of monitoring data protection operations
Monitoring the data protection operations and its components provides a number of benefits. Firstly, it ensures that the backups meet SLAs and that issues are proactively resolved. Secondly, it provides a deeper understanding of how resources are being used. Finally, it provides a detailed report that can be provided to key stakeholders, demonstrating how and where data is protected.
With the new Immutable Workloads report introduced in Veeam ONE v12, you can get even more visibility into the immutability of your backups, helping to prevent data loss due to malware activity or unauthorized changes.
Veeam ONE v12 and Immutable Workloads Report
Veeam ONE v12 is a powerful monitoring and reporting solution for virtual, physical, and cloud-based workloads. With its new version 12, Veeam ONE provides enhanced visibility into the infrastructure and data protection operations.
Immutable Workloads Report Overview
One of the key features in Veeam ONE v12 is the Immutable Workloads Report. This report provides information on the data protection status of immutably protected backups.
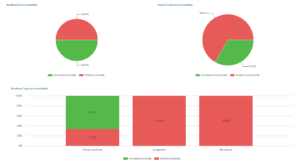
(Source: Veeam)
The report displays a summary of all immutable backups and allows users to drill down into the details of each backup to see its composition, immutability status, and more.
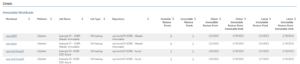
(Source: Veeam)
In addition to the Immutable Workloads Report, Veeam ONE v12 includes several other enhanced reports that relate to immutability. These reports provide detailed information on the status of immutably protected backups, such as the number of backup files, their size, and the backup chain structure.
With these reports, users can quickly assess the health of their immutable backups and ensure that they are adequately protected from malicious attacks.
The Importance of Monitoring Immutability
One of the key benefits of monitoring immutability is the ability to gather detailed reports that can be used for analysis and decision making. These reports help to provide a complete picture of the status of the backup process, including any issues or anomalies that may arise. This information can be used to make informed decisions about the management of backups and to improve the overall ransomware protection strategy.
Demonstrating data protection to key stakeholders
Monitoring immutability is also important for demonstrating the effectiveness of the data protection strategy to key stakeholders.
With detailed reporting, it is possible to show that the backups are not only being stored securely but are also immune to tampering or accidental deletion. This provides a level of confidence and peace of mind to stakeholders and ensures that the data protection process is being managed effectively.
Alarms for immutability management
In addition to detailed reporting, Veeam ONE v12 also provides the ability to set alarms that can alert administrators when certain conditions are met.
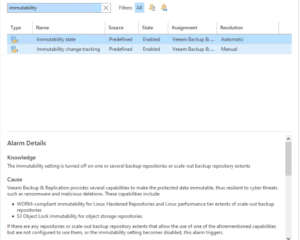
(Source: Veeam)
For example, an alarm can be set to trigger if a backup is deleted or altered, allowing administrators to respond quickly to potential security threats. This level of monitoring and management helps to ensure that the backups remain secure and available when they are needed, providing peace of mind and ensuring that the data is protected at all times.
Conclusion
In conclusion, data protection is an integral part of any organization’s security and operations strategy. The 3-2-1 rule for backups has been a tried-and-true method for ensuring data protection, but with the advent of new technologies and the increasing threat of malicious attacks, it is necessary to update the rule to include immutability and monitoring.
Veeam ONE v12 offers a suite of enhanced reporting features, including the Immutable Workloads Report, that provide valuable insights into data protection operations and the state of backups. These reports, combined with visibility tools, alarms, and immutable storage options, can provide detailed analysis and decision-making capabilities, as well as demonstrate data protection to key stakeholders.
For those organizations looking to fully realize the benefits of Veeam ONE v12 and monitor their backups, StoneFly DR365V is a Veeam-ready backup and disaster recovery appliance, with air-gapping and immutability, that supports all of Veeam’s native features, including Veeam ONE v12. This appliance offers a cost-effective, turnkey solution for data protection, providing peace of mind and ensuring that organizations are always prepared for any eventuality.
Experience the unparalleled data protection solution of StoneFly DR365V for yourself. Contact us today to schedule a demo and see the full potential of this Veeam-ready backup and disaster recovery appliance.













