If you’re like most business owners, security is a top priority. You likely have a firewall and anti-virus software in place to protect your systems, but what about your backups? Are they secure?
In this blog post, we’ll show you how to add air-gapping and immutability to your Veeam backup appliance, which will help keep your data safe and secure.
Why add air-gapping and immutability to your backup and DR infrastructure
Hackers program ransomware to infect your production, all network-connected shared storage devices, and backup and disaster recovery (DR) infrastructure. This implies that no only do you need backup and DR to protect your storage systems, but you also need to make sure that your backup and DR is ransomware-proof as well.
Typically, through infiltration methods such as phishing emails, exploiting known vulnerabilities, etc. ransomware infects a system/server and spreads through the network. If your backup and DR solution is accessible via the production network, then it’s not as safe as you’d expect it to be.
While backup and DR is critical, backups alone are not enough – you need to add air-gapping and immutability to your data protection solution to make sure your business can recover from ransomware attacks.
For more on this, read Backups aren’t Enough – Here’s Why Air-Gapping and Immutability are Necessary
Why do you need air-gapping and immutability for Veeam
Veeam provides a complete portfolio to automate backup, replication, and restore. A reliable Veeam backup appliance orchestrates all of Veeam’s capabilities without consuming any of your production resources. However, while Veeam provides a comprehensive set of features, the way you store Veeam’s backups, snapshots, and replicas determines how effective a Veeam backup appliance is.
If your Veeam backup appliance is accessible via the production network, then even with Veeam’s enterprise software, your environment is vulnerable to ransomware attacks.
How to add air-gapping and immutability to your Veeam Backup and DR Environment(s)
Depending on your preference and the vendor, you can integrate air-gapping and immutability with your existing environment(s) in a number of ways.
StoneFly provides physical, virtual, and cloud-based solutions compatible with most popular servers, hypervisors, and clouds, and customizable for any scale including SMBs, SMEs, and large enterprises.
Physical Air-Gapped and Immutable Storage Nodes for Veeam

The DR365VIVA are purpose-built automated air-gapped and immutable storage nodes for Veeam backup appliances. The air-gapped nodes connect seamlessly to your Veeam backup hardware and automate ransomware protection for your sensitive information, backups, snapshots, and replicas.
The preinstalled StoneFly storage virtualization engine (SCVM) enables storage administrators to set policies which automate data transfers and define retention periods for the target storage. Retain critical backups for a month or months, and even years.
In addition to the immutable and secure target storage for your Veeam backup appliance, the DR365VIVA also facilitate shorter Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) with features such as direct Virtual Machine (VM) spin up, granular file-level recovery, and more.
The complete set of ransomware protection features of DR365VIVA make it suitable for organizations, big and small, looking to meet cyber-insurance requirements.
Virtual Air-gapped and Immutable Storage for Veeam Backup Hardware
Limited on budget, rack space, or not interested in physical air-gapped nodes? Then look no further than StoneFly’s patented storage virtualization engine that is compatible with most mainstream hypervisors and provides the complete air-gapped and immutable storage experience as the hardware.
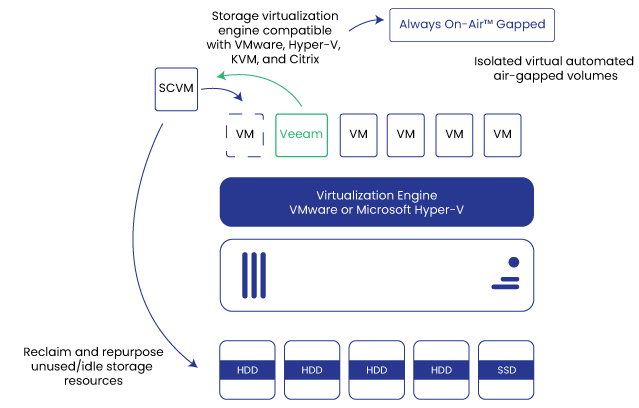
Similar to the physical air-gapped nodes, the virtual air-gapped nodes are isolated by default and support immutable storage features such as S3 object storage, and file lockdown, with policy-based data transfers and retention.
Cloud-Based Air-Gapped and Immutable Storage for Veeam
As an Azure marketplace partner, StoneFly’s patented storage virtualization engine can also be bought directly from Azure marketplace and deployed as an Azure VM which provides the premium air-gapped, immutable storage, and encryption capabilities of a fully provisioned physical or virtual appliance.
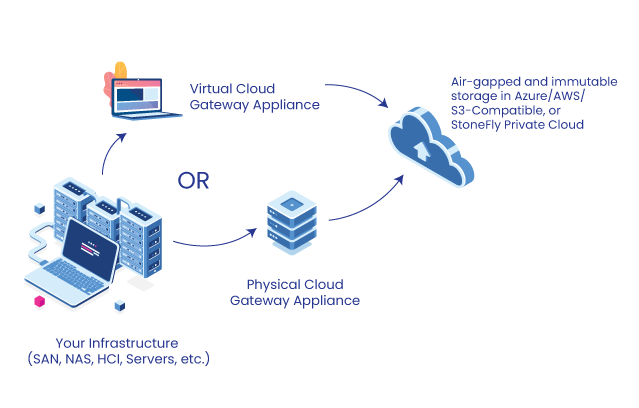
Physical, Virtual or Cloud: Which air-gapped and immutable storage is best for your Veeam backup appliance
Regardless of which type of deployment option you choose for your air-gapped and immutable storage, it’s important to note that the intent remains the same: ensure ransomware protection for your Veeam backups.
Each deployment option has its own pros and cons. Here’s a brief overview to help you decide the best one for your Veeam backup hardware:
| Physical | Virtual | Cloud |
| Higher upfront costs: hardware + license but better ROIs in the long run | License cost + cost depending on available storage resources | Little to no upfront costs but higher TCO and lower ROIs in the long run |
| Ability to scale, and the time it takes to scale dependent on hardware availability, and shipping times respectively. | Ability to scale dependent on available storage resources. Time to scale is non-disruptive and takes only a few clicks. | Scale quickly, without limits, and with a few clicks. |
| High performance with no bottlenecks – recommended for zero-tier mission-critical workloads. | Great performance as source and target are hosted on the same storage stack. | Performance dependent on available bandwidth, network speed, data volume, and latency. |
| Support 3-2-1 backup strategy | Support 3-2-1 backup strategy | Support 3-2-1 backup strategy |
| Easy-of-management with policy-based automation | Easy-of-management with policy-based automation | Easy-of-management with policy-based automation |
Conclusion
Veeam provides a comprehensive set of backup, replication, and restore features. However, if you store Veeam backup data in readily accessed network-connected volumes, then your infrastructure is vulnerable to ransomware attacks. Which is why it’s necessary for Veeam backup appliance owners to integrate air-gapped and immutable storage volumes with their existing environments.
Need help integrating air-gapped and immutability with your Veeam backup hardware? Talk to our pre-sales engineers today.










