In a digitally transformed landscape fraught with ever-evolving cyber threats, the acronyms EDR (Endpoint Detection and Response), XDR (Extended Detection and Response), MDR (Managed Detection and Response), and NDR (Network Detection and Response) have become critical fixtures in the cybersecurity lexicon. These innovative technologies stand as the vanguards against malicious actors, ensuring the integrity and resilience of your digital infrastructure. This blog serves as a comprehensive guide to the world of EDR, XDR, MDR, and NDR, offering a deep dive into their definitions, significance, and the pivotal roles they play in fortifying your cybersecurity posture.
What is Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) is a robust cybersecurity solution designed to protect individual devices (endpoints) within a network. EDR works by continuously monitoring and analyzing endpoint activity, allowing it to detect and respond to security threats in real-time.
Unlike traditional antivirus software that relies on signature-based detection, EDR leverages advanced techniques such as behavioral analysis, machine learning, and threat intelligence to identify malicious activities and potential vulnerabilities.
Features and Capabilities of Endpoint Detection and Response (EDR)
- Real-time Monitoring: EDR solutions provide real-time visibility into endpoint activities, allowing security teams to monitor all processes, file changes, and network connections. This visibility is crucial for early threat detection.
- Threat Detection: EDR tools use a wide range of detection methods, including heuristics, anomaly detection, and signature-based scans. These techniques help identify known and unknown threats.
- Incident Response: EDR enables rapid incident response by allowing security teams to isolate compromised endpoints, block malicious processes, and remediate threats without impacting network operations.
- Threat Hunting: EDR solutions also support proactive threat hunting. Security analysts can search for hidden threats and potential vulnerabilities by querying endpoint data.
How Endpoint Detection and Response (EDR) Works
Endpoint Detection and Response (EDR) is a vital component of modern cybersecurity, primarily focused on safeguarding endpoints such as desktops, laptops, servers, and mobile devices. EDR systems are designed to detect and respond to security incidents at the endpoint level, offering a granular view of potential threats and vulnerabilities. Here’s a step-by-step breakdown of how EDR works:
- Data Collection: EDR solutions continuously collect vast amounts of data from endpoints, including system logs, application logs, network traffic data, and file system information. This comprehensive data gathering serves as the foundation for threat detection.
- Data Analysis: Once data is collected, EDR systems employ advanced analytics, machine learning, and behavioral analysis to scrutinize this data. The primary goal is to identify unusual patterns, anomalies, and indicators of compromise.
- Threat Detection: By analyzing the collected data, EDR solutions can detect a wide range of threats, including malware, advanced persistent threats, zero-day vulnerabilities, and suspicious user activities. It correlates data across multiple endpoints to identify threats that may be invisible on a single device.
- Alert Generation: When EDR systems detect a potential threat or anomaly, they generate alerts in real-time. These alerts are prioritized based on the severity and potential impact of the threat, helping security teams focus on the most critical issues.
- Threat Response: EDR goes beyond detection by facilitating automated or manual threat response. It offers a range of response actions, such as isolating an infected device, killing malicious processes, and quarantining affected files.
- Threat Investigation: EDR tools provide security analysts with extensive information about the detected threat. Analysts can investigate the incident, understand its origin, impact, and scope, and take appropriate measures for remediation.
- Remediation and Prevention: EDR systems assist in eliminating threats and vulnerabilities. They offer the ability to remove malicious code, patch vulnerabilities, and implement proactive measures to prevent future incidents.
- Continuous Monitoring: EDR solutions provide ongoing monitoring and reporting, allowing organizations to track security incidents, measure the effectiveness of their responses, and fine-tune security policies.
It’s essential to note that EDR systems work collaboratively with other security technologies, such as firewalls, intrusion detection systems (IDS), and security information and event management (SIEM) solutions. This synergy ensures comprehensive protection and a rapid response to emerging threats, making EDR an indispensable component in a layered security strategy.
Benefits of Endpoint Detection and Response (EDR)
Endpoint Detection and Response (EDR) offers several technical benefits to enhance an organization’s security posture:
- Real-time Monitoring: EDR solutions continuously monitor endpoint devices, collecting data on processes, file activities, network connections, and system changes in real-time. This level of monitoring provides visibility into endpoint activities that can help identify potential threats as they happen.
- Behavioral Analysis: EDR employs behavioral analysis to establish baselines of normal activity for each endpoint. When deviations from these baselines occur, EDR can trigger alerts, as these anomalies may indicate malicious activity or security breaches.
- Threat Detection: EDR solutions use various detection techniques, including signature-based detection, heuristics, machine learning, and threat intelligence feeds, to identify known and unknown threats. This combination of methods ensures a high detection rate for various types of malware and cyber threats.
- Investigation Capabilities: EDR offers detailed forensic capabilities for in-depth security investigations. Security analysts can analyze historical data, track the progression of a threat, and understand the tactics, techniques, and procedures (TTPs) used by attackers.
- Threat Hunting: EDR solutions allow proactive threat hunting. Security teams can create custom queries to search for signs of suspicious activity or potential security breaches. This capability enables organizations to take a proactive stance in identifying and mitigating threats.
- Automated Response: EDR can be configured to respond automatically to detected threats. Automated responses may include isolating an infected endpoint, blocking malicious processes, or executing predefined remediation actions. This automation helps contain threats and reduces response time.
- Scalability: EDR solutions can scale to accommodate organizations of various sizes, from small businesses to large enterprises. This scalability ensures that the solution can handle a growing number of endpoints and a higher volume of security events.
- Integration with SIEM: EDR can integrate with Security Information and Event Management (SIEM) systems, enhancing an organization’s overall security architecture. This integration enables the centralized management and correlation of endpoint data with other security events.
- Data Encryption and Privacy: EDR solutions often include data encryption and privacy features, securing the data collected from endpoints and ensuring it is not accessible to unauthorized users.
- Compliance Support: EDR aids in meeting regulatory compliance requirements by providing detailed monitoring and reporting capabilities. These features assist organizations in demonstrating adherence to data protection and security standards.
How StoneFly Integrates Endpoint Detection and Response (EDR)
StoneFly’s Veeam-integrated DR365V appliance comes with built-in EDR features, adding an extra layer of security to your endpoints.
- Inline Entropy Analysis for Malware Detection: The DR365V backup and DR appliance comes equipped with an “Inline entropy analysis” feature, enabling real-time analysis of data during backups. This ensures that no malicious content goes unnoticed during data transfer, bolstering your endpoint security.
- File System Activity Analysis: The “File system activity analysis” feature in DR365V is a game-changer. It encompasses text content analysis, encryption scrutiny, detection of suspicious files, and the ability to detect the deletion of a large number of existing files. This multifaceted approach to file system activity helps identify and prevent potential security threats.
How EDR Enhances Threat Detection and Response
EDR (Endpoint Detection and Response) is instrumental in enhancing threat detection and response capabilities. In the context of the DR365V appliance, EDR continuously monitors endpoint activities in real-time, enabling comprehensive threat detection.
- Anomaly Detection: EDR establishes a baseline for normal endpoint behavior. Any deviations from this baseline are flagged as potential threats. For instance, if a user accesses a sensitive file they’ve never interacted with before, EDR identifies this as suspicious.
- Automated Response: EDR empowers your security team with automated response capabilities. When a threat is identified, it can isolate the affected endpoint from the network, preventing lateral movement and data exfiltration. Real-time alerts are triggered, enabling swift action.
- Threat Intelligence: EDR’s threat intelligence is enriched by integration with threat databases, allowing it to recognize known malware, suspicious IP addresses, and other threats through cross-referencing with updated threat intelligence feeds.
What is Extended Detection and Response (XDR)
Extended Detection and Response, is a comprehensive cybersecurity approach that goes beyond traditional security measures. It collects and analyzes data from multiple sources, such as endpoints, networks, and cloud environments, to detect and respond to security threats.
XDR provides a more holistic view of potential security issues, making it easier to identify and stop cyberattacks in their early stages. It’s like having a security team that watches over your entire digital environment, not just individual parts, to keep your data safe.
Key Components of Extended Detection and Response (XDR) Solutions
- Data Collection: XDR solutions collect data from a wide range of sources, including endpoint security tools, firewalls, intrusion detection systems, cloud platforms, and network traffic. This holistic data gathering ensures a comprehensive view of the organization’s security landscape.
- Analytics and Detection: XDR leverages advanced analytics, machine learning, and threat intelligence to detect suspicious activities, anomalies, and potential threats. By analyzing behavioral patterns, it identifies deviations from normal operations that could indicate cyberattacks or vulnerabilities.
- Automated Response: XDR incorporates automated response capabilities that allow predefined actions when threats are detected. These actions may include isolating compromised devices, blocking malicious network traffic, or launching countermeasures to mitigate threats.
How Extended Detection and Response (XDR) Works
- Data Ingestion and Collection: XDR begins by collecting data from multiple sources across an organization’s entire IT environment. This data includes logs from endpoints, network traffic, cloud services, email systems, and more. The data is continuously ingested and stored for analysis.
- Data Normalization and Enrichment: After data ingestion, XDR normalizes and enriches the information. This process standardizes data formats and augments raw data with additional context, such as threat intelligence feeds, known indicators of compromise (IoCs), and baseline user behavior.
- Data Analysis and Correlation: Advanced analytics and machine learning algorithms are employed to analyze the normalized data. XDR systems correlate events and activities across different sources. This correlation enables the identification of patterns and anomalies that may indicate a security threat.
- Threat Detection: XDR is designed to identify both known and unknown threats. It uses predefined threat indicators, behavior-based analysis, anomaly detection, and machine learning models to detect suspicious activities. These activities may include unusual login behavior, data exfiltration, or malware propagation.
- Real-time Alerting: When a potential threat is detected, XDR generates real-time alerts. These alerts are sent to security analysts or incident response teams for further investigation. They include details about the detected event, its severity, and the potential impact.
- Alert Investigation and Analysis: Security analysts play a crucial role in XDR. They investigate alerts to determine their validity and potential impact on the organization. During this phase, analysts may pivot through data to understand the full scope of an incident.
- Incident Response: Once a confirmed security incident is identified, XDR provides support for incident response. This includes containment, eradication, and recovery efforts. Response actions may involve isolating affected systems, patching vulnerabilities, and changing compromised credentials.
- Threat Intelligence Integration: XDR solutions integrate with threat intelligence feeds and databases. This ensures that the system is up to date with the latest threat indicators, tactics, techniques, and procedures used by threat actors. Threat intelligence helps in early threat detection and informed decision-making.
- Automated Remediation: Some XDR solutions offer automated remediation capabilities. For known threats, they can automatically apply remediation actions, such as blocking malicious domains, quarantining infected devices, or rolling back changes made by attackers.
- User and Entity Behavior Analytics (UEBA): XDR systems incorporate UEBA to detect unusual user and entity behaviors. By establishing baselines of normal activity, they can identify deviations that may suggest insider threats, account compromise, or unauthorized access.
- Machine Learning and AI: Advanced XDR solutions leverage machine learning and artificial intelligence to enhance threat detection. These technologies can adapt to evolving threats, reduce false positives, and identify subtle anomalies that traditional methods might miss.
- Reporting and Forensics: XDR provides reporting and forensic capabilities. Security teams can analyze historical data, reconstruct incidents, and produce reports for compliance, incident analysis, and legal purposes.
- Threat Hunting: Some XDR solutions offer threat-hunting features. Security teams can proactively search for hidden threats, suspicious activities, and vulnerabilities that may not trigger automated alerts.
- Endpoint Detection and Response (EDR) Integration: XDR often includes EDR functionalities. This allows for detailed visibility and response capabilities at the endpoint level, adding an extra layer of protection.
Benefits of Extended Detection and Response (XDR)
- Comprehensive Threat Visibility: XDR provides a centralized platform for monitoring and analyzing security events across multiple sources, including endpoints, networks, cloud environments, and more. This comprehensive visibility allows security teams to identify threats early, even those that span different parts of the infrastructure.
- Enhanced Detection Capabilities: XDR leverages advanced analytics and threat intelligence to detect both known and unknown threats. It uses techniques like behavioral analysis, anomaly detection, and machine learning to identify suspicious activities and potential security incidents.
- Faster Incident Response: With centralized monitoring and automated workflows, XDR streamlines incident response. It can correlate data from various sources to provide security teams with a holistic view of an attack, enabling quicker and more effective responses.
- Reduced False Positives: By using advanced analytics and contextual information, XDR helps reduce false positives, which often plague security teams. This ensures that the alerts generated are more likely to be genuine threats, reducing alert fatigue.
- Simplified Investigation: XDR offers the ability to trace the progression of an attack across different parts of the infrastructure. This makes it easier for investigators to understand the attack’s tactics, techniques, and procedures (TTPs) and determine the extent of the compromise.
- Scalability: As organizations grow and their digital environments expand, XDR scales to accommodate the increased volume of data and security events. It can handle the complexity of modern infrastructures, including hybrid and multi-cloud environments.
- Integration with Existing Tools: XDR solutions are designed to integrate with other security tools and platforms, allowing organizations to maximize their existing investments and create a more cohesive security strategy.
- Compliance and Reporting: XDR solutions often include features for compliance monitoring and reporting, simplifying the process of meeting regulatory requirements and providing evidence of adherence to security policies.
What is Managed Detection and Response (MDR)
Managed Detection and Response (MDR) is a comprehensive cybersecurity service that provides organizations with 24/7 monitoring, detection, and response to security threats and incidents. MDR services are typically offered by third-party providers and are designed to enhance an organization’s security posture by proactively identifying and mitigating cyber threats in real-time.
These services combine advanced technology, threat intelligence, and expert security analysts to ensure the continuous protection of an organization’s digital assets.
MDR goes beyond traditional security measures, aiming to minimize the impact of security incidents and reduce the time between threat detection and response.
Key Characteristics of Managed Detection and Response (MDR)
- Continuous Monitoring: MDR solutions provide 24/7 real-time monitoring of an organization’s network, endpoints, and security infrastructure, using advanced tools and technologies to detect suspicious activities and potential threats.
- Threat Detection and Analysis: MDR services employ a combination of signature-based and behavior-based threat detection methods to identify known and emerging threats. They analyze network traffic, logs, and endpoints for indicators of compromise (IoCs) and unusual activities.
- Incident Response: MDR includes incident response capabilities, allowing security analysts to react promptly to confirmed threats. This involves investigating incidents, isolating affected systems, and containing threats to prevent further damage.
- Threat Intelligence Integration: MDR providers integrate threat intelligence feeds and databases into their systems to enhance their ability to identify and respond to new and evolving threats effectively.
- Log Analysis: MDR services extensively analyze logs from various sources, including firewalls, intrusion detection systems (IDS), and endpoints, to identify patterns and anomalies that may indicate malicious activities.
- Behavioral Analytics: MDR solutions use behavioral analytics to establish a baseline of normal user and system behavior. Deviations from this baseline can indicate potential security issues.
- Endpoint Detection and Response (EDR): Many MDR offerings include EDR features, allowing organizations to monitor and respond to threats on individual endpoints, including desktops, laptops, and servers.
- Cloud-Based Security: MDR services often leverage cloud-based security tools and analytics for scalability and agility in handling the vast amount of data generated by modern networks.
- Threat Hunting: MDR providers employ threat-hunting techniques to proactively search for hidden threats and vulnerabilities within an organization’s environment, even if no alarms have been triggered.
- Forensic Analysis: In-depth forensic analysis is conducted to understand the scope and impact of security incidents, helping organizations learn from past events to better protect themselves in the future.
- Reporting and Documentation: MDR services provide detailed reports on detected threats, incident response actions, and recommendations for security improvements. These reports assist organizations in maintaining compliance and refining their security strategies.
- Integration with SIEM: MDR solutions often integrate with Security Information and Event Management (SIEM) systems, allowing for comprehensive log management, correlation, and alerting.
How Managed Detection and Response (MDR) Works
- Data Collection and Aggregation: MDR begins by collecting data from various sources within an organization’s IT environment. These sources include network logs, security event logs, endpoint data, cloud platforms, and more. The collected data is then aggregated into a centralized platform, forming a comprehensive view of the organization’s digital landscape.
- Data Analysis and Correlation: Once the data is aggregated, MDR employs advanced analytics and correlation techniques to identify patterns and anomalies. Security analysts leverage SIEM (Security Information and Event Management) systems and behavior analytics to detect unusual activities that may indicate a security threat.
- Threat Detection and Alerting: MDR systems continuously monitor network traffic, system logs, and user behavior. They use predefined threat indicators, behavioral analysis, and anomaly detection to identify potential security incidents. When a threat is detected, the system generates alerts in real-time.
- Alert Triage: Security analysts play a critical role in MDR. They receive the alerts generated by the system and perform alert triage. During this phase, analysts assess the alerts to determine their severity, validity, and potential impact on the organization. This process separates true threats from false positives.
- Incident Investigation: Once a genuine security incident is identified, MDR analysts initiate an in-depth investigation. This includes tracing the origin and scope of the incident, understanding the attack vector, and assessing the potential damage. The investigation may involve forensics, log analysis, and threat attribution.
- Response Planning: After understanding the incident’s nature and extent, MDR analysts develop an incident response plan. This plan outlines the steps to mitigate the threat, recover affected systems, and prevent future incidents. The response plan may involve isolating compromised devices, applying patches, or resetting compromised credentials.
- Continuous Monitoring: MDR does not stop at incident response; it also provides continuous monitoring. This ensures that organizations are safeguarded against persistent threats. The MDR team remains vigilant, continually observing the network for any signs of renewed attacks or emerging threats.
- Threat Intelligence: MDR services incorporate threat intelligence feeds from various sources, such as government agencies and cybersecurity organizations. This threat intelligence assists in identifying the latest threat indicators and trends, enabling proactive threat detection.
- Behavioral Analysis: MDR employs behavioral analysis to identify suspicious user and entity behaviors. By establishing baselines of normal activity, the system can detect deviations that may signify unauthorized access, insider threats, or compromised accounts.
- Machine Learning and AI: Advanced MDR solutions leverage machine learning and artificial intelligence to improve threat detection. These technologies can detect evolving attack tactics and adapt to new threats based on historical data.
- Security Awareness Training: MDR often includes user training and awareness programs. Educating employees about cybersecurity best practices and how to recognize and report potential threats is a proactive measure to enhance security.
- Compliance and Reporting: MDR services assist organizations in adhering to regulatory compliance requirements. They generate reports and provide the necessary documentation to demonstrate compliance to auditors and authorities.
- Vulnerability Assessment: MDR may include vulnerability scanning and assessments. This helps organizations identify weak points in their infrastructure and take steps to remediate them before they can be exploited by attackers.
- Threat Hunting: Some MDR providers also engage in proactive threat hunting. They search for hidden threats and vulnerabilities that may not trigger alerts but still pose risks to the organization.
Benefits of Managed Detection and Response (MDR)
The benefits of Managed Detection and Response (MDR) are crucial for organizations seeking robust cybersecurity protection and effective threat management. Here are the key advantages:
- Proactive Threat Detection: MDR services offer proactive threat detection capabilities that continuously monitor and analyze an organization’s network, endpoints, and security infrastructure to identify potential threats before they escalate.
- Enhanced Security Posture: MDR strengthens an organization’s security posture by offering 24/7 monitoring, incident detection, and rapid incident response, reducing the likelihood of successful cyberattacks.
- Comprehensive Threat Coverage: MDR solutions provide extensive threat coverage, detecting a wide range of threats, including known and emerging threats, insider threats, zero-day vulnerabilities, and advanced persistent threats (APTs).
- Timely Incident Response: MDR services enable timely incident response by providing detailed insights into security incidents and helping organizations take immediate action to contain and remediate threats, minimizing damage.
- Advanced Analytics: MDR leverages advanced threat intelligence, behavioral analytics, and machine learning algorithms to detect and analyze complex threats that traditional security tools may miss.
- Scalability: MDR solutions are scalable and can adapt to the growing needs of organizations, accommodating increased data and network traffic as the business expands.
- Reduced False Positives: By utilizing a combination of signature-based and behavior-based detection methods, MDR helps reduce false positives, ensuring security teams focus on real threats.
- Managed Security Expertise: MDR services often come with dedicated security experts who monitor and analyze your security infrastructure, providing valuable insights and recommendations.
- Threat Hunting: MDR services actively search for hidden threats and vulnerabilities through threat hunting, identifying security weaknesses before they are exploited by cybercriminals.
- Integrated Incident Response: MDR services provide incident response capabilities as an integral part of the offering, streamlining the process of reacting to and mitigating security incidents.
- Compliance Support: MDR services can help organizations maintain compliance with industry-specific regulations by providing detailed reporting and documentation of security incidents.
- Forensic Analysis: Detailed forensic analysis is conducted to understand the root causes of security incidents and prevent similar incidents in the future.
- Improved Incident Reporting: MDR services offer comprehensive incident reports that include in-depth analysis, actionable recommendations, and documentation for post-incident reviews.
- Cost-Effectiveness: Outsourcing MDR services can be cost-effective compared to building an in-house 24/7 security operation center (SOC) and hiring and training security experts.
- Enhanced Threat Intelligence: MDR solutions integrate threat intelligence feeds and databases to better detect, respond to, and mitigate new and evolving threats.
- Proactive Security Strategy: By monitoring network behavior and anomalies, MDR helps organizations proactively identify and address vulnerabilities and security gaps in their infrastructure.
- Rapid Adaption to New Threats: MDR providers quickly adapt to new and emerging threats, keeping your organization protected against the latest cybersecurity risks.
- Integration with Existing Tools: Many MDR services can seamlessly integrate with an organization’s existing security tools and systems, providing a cohesive security ecosystem.
What is Network Detection and Response (NDR)
Network Detection and Response (NDR) is a cybersecurity approach focused on monitoring network traffic to identify and respond to potential security threats and anomalies. NDR solutions employ advanced analytics and real-time monitoring to detect and investigate suspicious activities and security breaches within an organization’s network.
Key Components and Characteristics of Network Detection and Response (NDR)
- Packet Capture and Analysis: NDR systems capture network packets and analyze their contents to detect unusual or malicious patterns. Deep packet inspection provides detailed insights into network traffic, aiding in the identification of threats.
- Behavioral Analysis: NDR relies on behavioral analytics to establish a baseline of normal network behavior. Deviations from this baseline trigger alerts, as they may indicate security incidents.
- Anomaly Detection: NDR solutions continuously monitor network traffic for anomalies such as unusual data transfers, irregular login attempts, or atypical data flows that might signal a security breach.
- Threat Intelligence Integration: NDR platforms integrate with threat intelligence feeds to stay updated on known threats, malicious IP addresses, and indicators of compromise (IoCs). This data is used to identify and respond to threats.
- Machine Learning and AI: Machine learning algorithms analyze network traffic patterns and behavior to detect known and unknown threats. Over time, the system becomes more effective at recognizing new attack vectors.
- Real-time Alerts: NDR systems generate real-time alerts when they detect suspicious activity. These alerts are prioritized based on the severity of the threat, enabling rapid response.
How Network Detection and Response (NDR) Works
NDR works by continuously monitoring network traffic and applying various detection techniques:
- Traffic Monitoring: NDR solutions passively monitor network traffic, capturing and analyzing packets and flows across the network.
- Behavioral Profiling: Initially, the system establishes a baseline of normal network behavior. This involves understanding typical data flows, bandwidth utilization, and user behavior.
- Anomaly Detection: Deviations from the established baseline are flagged as potential security incidents. These anomalies are thoroughly investigated to determine if they pose a threat.
- Threat Identification: NDR systems utilize threat intelligence feeds to cross-reference network activity against known threats and indicators of compromise. This aids in identifying malicious traffic.
- Alert Generation: When a potential threat is detected, NDR generates real-time alerts. These alerts include details about the incident, its severity, and any associated IoCs.
- Response and Mitigation: After an alert is generated, the security team investigates the incident, often leveraging NDR’s integrated forensic tools. They then take appropriate action to mitigate the threat and prevent further damage.
Benefits of Network Detection and Response (NDR)
- Early Threat Detection: NDR operates in real-time, swiftly identifying emerging threats within your network. This proactive approach reduces the time window for attackers to exploit vulnerabilities, helping you thwart potential security breaches before they can cause harm.
- Reduced Dwell Time: Dwell time, the duration an attacker remains undetected within a network, is a critical security metric. NDR significantly reduces dwell time by promptly recognizing and responding to threats. By shortening the timeframe of compromise, you limit the potential damage caused by malicious actors.
- Incident Investigation and Forensic Analysis: NDR is a valuable tool for incident investigation and forensic analysis. It captures extensive network data, enabling security teams to conduct in-depth examinations of incidents. This capability is essential for understanding the scope and impact of a breach, as well as for compliance reporting and legal purposes.
- Comprehensive Threat Visibility: NDR provides an all-encompassing view of network activities. It monitors both external and internal traffic, offering visibility into interactions within your network. This holistic perspective ensures that even threats originating from compromised internal devices or insiders with malicious intent can be detected and addressed.
- Adaptation to New Threats: NDR solutions leverage machine learning and artificial intelligence to adapt to evolving threats. These technologies enable the system to recognize new attack techniques and behaviors. By continuously learning from incoming data, NDR remains effective in detecting threats even as cybercriminals develop more sophisticated tactics.
- Improved Network Security Posture: NDR plays a pivotal role in enhancing an organization’s network security posture. Its ability to identify and respond to threats promptly bolsters network defenses, safeguarding critical assets and sensitive data. This proactive security approach is essential in the face of ever-changing and increasingly sophisticated threats.
- Scalable Protection: NDR solutions can scale to suit your organization’s needs. Whether you have a small network or a vast, complex infrastructure, NDR can adapt to monitor and protect your entire environment effectively.
- Compliance and Reporting: NDR assists in compliance with regulatory requirements and reporting. It provides the necessary data and visibility to demonstrate your organization’s commitment to security standards, making audits and compliance assessments smoother and more comprehensive.
- Minimized False Positives: Advanced analytics and machine learning algorithms enable NDR to differentiate between legitimate and suspicious network activities. This results in fewer false positives, ensuring that security teams focus on genuine threats rather than spending time investigating harmless events.
- Efficient Resource Allocation: By prioritizing and categorizing alerts, NDR allows security teams to allocate resources efficiently. Critical threats are addressed promptly, while less urgent issues can be managed in a structured manner, optimizing incident response processes.
- Situational Awareness: NDR enhances situational awareness by providing security professionals with a clear view of network activity. This empowers them to make informed decisions, respond to threats effectively, and improve network defense strategies.
- User and Entity Behavior Analytics (UEBA): NDR often includes UEBA capabilities, enabling the detection of unusual user and entity behaviors. By analyzing user activities, NDR can identify compromised accounts and insider threats, contributing to enhanced security.
Comparing EDR vs MDR vs XDR vs NDR
In the realm of cybersecurity, understanding the distinctions and applications of Endpoint Detection and Response (EDR), Managed Detection and Response (MDR), Extended Detection and Response (XDR), and Network Detection and Response (NDR) is crucial.
Each solution plays a distinct role in safeguarding an organization against cyber threats. Below, we’ll provide a comparative overview of these security technologies:
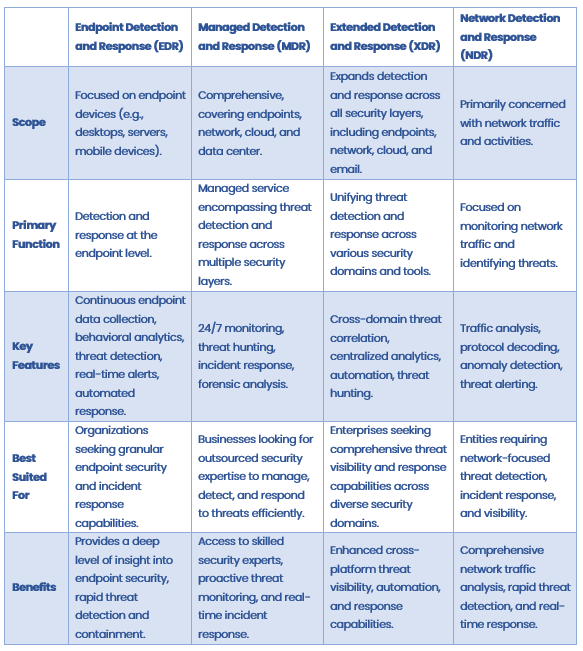
Comparing EDR, MDR, XDR, and NDR: Which Is Right for You?
The choice between EDR, MDR, XDR, and NDR largely depends on your organization’s specific security needs and objectives. Here are some key takeaways to consider:
- EDR is ideal for organizations seeking to fortify endpoint security, providing in-depth insights into the security of individual devices, swift threat detection, and containment.
- MDR is suitable for businesses looking to outsource security operations to experienced professionals. MDR combines expert threat detection, real-time monitoring, and efficient incident response across multiple security domains.
- XDR is best for enterprises that require unified security across various layers, including endpoints, networks, cloud, and email. It offers comprehensive threat visibility and automation.
- NDR is essential for entities focused on monitoring and protecting network traffic. NDR excels at rapid threat detection, real-time response, and network visibility.
In many cases, organizations may employ a combination of these solutions to achieve a layered security approach that effectively safeguards against evolving cyber threats and attacks. The right choice for your organization depends on your unique security landscape, goals, and available resources.
Conclusion
Endpoint Detection and Response (EDR) ensures comprehensive protection at the endpoint level, while Managed Detection and Response (MDR) extends threat management across multiple security layers. Extended Detection and Response (XDR) unifies threat detection and response across various domains, and Network Detection and Response (NDR) excels in monitoring network traffic.
The key to effective cybersecurity lies in choosing the right solution that aligns with your organization’s specific needs and objectives. Whether it’s granular endpoint security, outsourced security expertise, cross-platform threat visibility, or network-focused defense, the synergy of these technologies fortifies the cyber defense posture. As cyber threats continue to evolve, adopting the appropriate security measures is paramount for protecting the enterprise digital realm.










