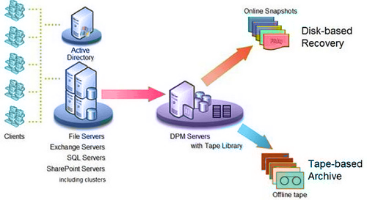
As the volume of mission-critical data is increasing, so is the urgency to protect it. Numerous data copies are created to provide data protection from inadvertent deletion, modification and unplanned downtime. Disk to disk data copies are time and space intensive leading to a rise in storage costs. Storage Snapshot is proving its prevalence effective in the data storage field, as it offers data protection along with data mining and data cloning. Most of the vendors who deliver storage hardware and related software are offering snapshot technology support, as it offers advanced data protection, which is essential for mission critical businesses.
What is snapshot?
It’s a logical point in time image of another volume called a base volume. A snapshot is the physical copy of the data but, you can create it much more quickly than the physical copy. It requires less disk space. Basically a snapshot provides an instant important time image of that volume. Snapshots enhance data protection by providing multiple archived copies for quick and recent restoration, facilitating the backup process to the snapshot volume.
A storage snapshot is a back-up copy, which is created at a particular point in time. The snapshots are available in the instant basis to the other applications, involved in the data analysis, data protection and data replication. The data related copy, will be consistently available to the application. The snapshot; however, will be available as a backup copy to perform other functions on the data.
How Snapshot works? – Techniques and Details:
Different vendors provide different implementation techniques for snapshot technology. Each technique, which snapshots use, has its own benefits. Below section will be explaining the popular techniques used in storage snapshot technology.
Copy-on-write:
A storage snapshot is created by the use of the pre-designated space allocated to it. When the snapshot is created at first, the meta-data related to the original data is stored and is backed up as a copy. There is no physical copy of the snapshot which is created. When the writes to the original volume are being lodged, the snapshot carefully tracks down the changing blocks taking place due to writes, on the original volume. The original data is then overwritten and will fetch the name of “copy-on-write” technique.
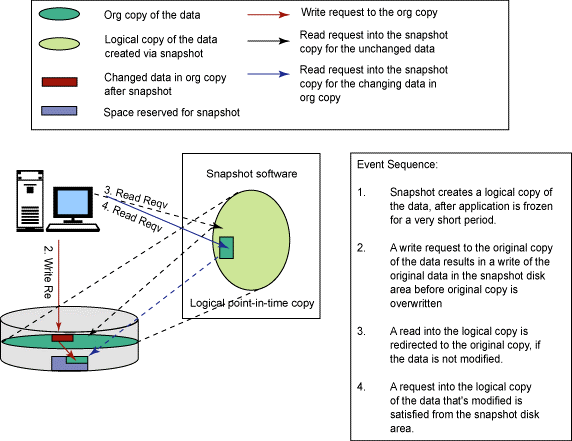
Duty of copy-on-write
Its duty is to move the original data block to the snapshot storage, prior to the write onto the block. This makes the data remain consistent in the time based snapshot. When the user requests for “read- requests” to the snapshot of unchanged data, the request is reflected to the original volume. It must be noted that the data blocks are copied only once, into the snapshot, on first write instance basis.
Drawbacks in copy-on-write:
The main drawback in this copy-on-write technique of snapshot is that there will be an impact of performance for sure on the original data volume, as write requests to data blocks can only be carried out, when the original data is being “copied” to the snapshot. If in case the data remains unchanged, then the read requests will be diverted to the original volume. Copy- on- write technique is space efficient as, the storage space required to create a snapshot is minimal to hold only the data which is changing and the data will only be valid, when the original copy is available.
Redirect-on-Write:
It is a clone to the Copy-on-write technique related to storage snapshot. Redirect-on-write doesn’t deal in double writing and offers storage space and performance with efficient snapshots. In this technique, new writes are reflected to another location which is separately allocated for snapshots. The main advantage in redirecting the write is that one write takes place at a time, which is different to copy-on-write; where two writes can occur at a time, where one is for writing data on original copy onto the storage and the other one is for the changed data copy.
With the technique of redirect-on-write, the original copy will have point in time data, which will be the snapshot and the changed data will be diverted to the snapshot storage. If a snapshot gets deleted, then the snapshot storage will be re-diverted back into the original volume. If multiple snapshots are created, then complexity factor will rise as access to original data, tracking of the data in snapshots and original volume and reconciliation upon snapshot deletion becomes complex. As the snapshot relies on the original copy of the data, the original set can get quickly fragmented.
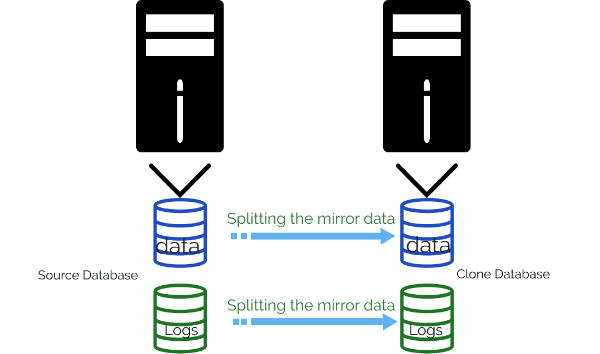
Split-Mirror:
In this snapshot technology, a physical clone of the storage entity is created, it can be a file-system or a volume, or LUN-Logical unit number for storage. The whole contents of the storage volume are copied onto a separate volume that can reside on a different storage space. As the data copy takes place, the split mirror snapshots cannot be created instantaneously. However, a clone can be made available by splitting a pre-existing mirror of the volume into two.
Drawback:
The drawback of split-mirror snapshots is to the original volume, as it has one fewer synchronized mirror. In addition to it, there will be a need for extra storage space as the original volume has one less synchronized mirrors. This snapshot method requires equivalent storage space like the original data and so it has a performance overhead of writing simultaneously to the mirrored copy.
Log structure file architecture:
In this snapshot technology, log files are used to track the writes to the original volume. When the need to restore the data arises, then the transactions noted in the log tracks are run in the reverse direction. Each of the write requests is logged to the original volume, which is much like a relational database.
Copy-on-Write with background copy:
Copy-on-write with a background copy is offered by some vendors, where a full copy of the snapshot data is created. In addition to it, a background process also copies a data from the original location to the snapshot storage space. This approach will offer dual benefits reaped from copy on write and split mirror methods. An instant snapshot is created by copy on write and then a background copy process is offered to perform as a block-level copy of the data. It stems up from original volume which is the ‘Source Volume’ to the snapshot storage (‘Target Volume’). These volumes will be in sequence to create an extra mirror of the original volume.
Continuous data protection:
This snapshot technology is also known as CDP and is a popular technique of storage snapshot technology; it’s offered by most vendors. Continuous data protection is offered with a continuous backup, if any change occurs in data then it is captured (backed up) and is stored in a separate location. An electronic journal of complete storage snapshots will also be available with CDP. This snapshot technology is different as it creates one snapshot, at every instance, each time data modification occurs.
Snapshot and Storage Stack:
The term storage snapshot refers to the hardware and software components that provide physical storage media to the applications, running on the host operating system. Snapshot solutions can be implemented to each individual layer in the storage stack.
What does Snapshot technology provide?
Snapshot technology empowers disaster recovery services to deliver efficient data protection. Snapshots provide:
- Data protection: It keeps data safe and multiple copies are used to prevent data loss.
- Data recoverability: Through snapshots the data is saved and in case of any downtime the data can be recovered quickly; thus ensuring data continuity.
- Enhanced applications availability.
- Backup management to large volumes of data.
- Low cost of ownership by eliminating backup gaps.
- Zero impact backup with minimal or zero application downtime, as it takes up frequent backups.
- Reduced data recovery time as it creates backup of large volumes of data in an efficient way, facilitating instant recovery.
StoneFly’s snapshot technology provides instant disk based point in time data copies that consume minimal storage space. Snapshot is another method to back up the system. It requires less storage space for each snapshot. It also increases the restoration speed.
![Snapshot-featured-image[1]](https://staging.stonefly.com/wp-content/uploads/2018/05/Snapshot-featured-image1.png)