The rapid growth of data has changed the way we live, learn, work and do business. But with this change comes more risk for businesses and enterprises. This post will cover one of the most popular backup strategies called 3-2-1 Backup Rule.
This blog post will discuss what is the 3-2-1 backup rule, why you should use it, and some best practices on implementing this strategy.
What is the 3-2-1 Backup Rule?
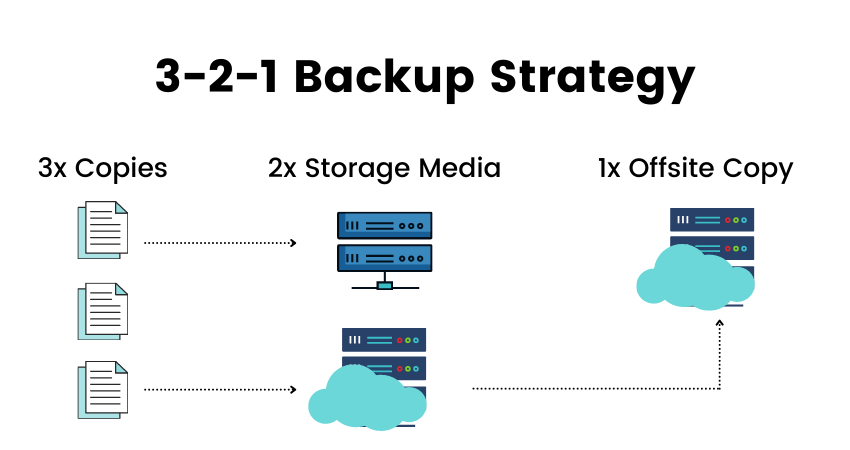
The 3-2-1 Backup Rule is a simple strategy for backing up data that calls out the need to maintain at least three copies of your data, on two different types of storage (e.g., a NAS appliance, tape array, and cloud storage), With one copy stored off-site.
If properly executed, this will afford maximum protection against threats like ransomware, malicious deletion, human error, and natural disasters. It will also provide a robust set of recovery capabilities in the event that data loss occurs.
Three Copies of Data
Having one original and two other copies of data significantly decreases the chances of losing data if any of the storage device fails. Before implementing the 3-2-1 backup policy, it is important to understand that each copy of your data should be stored on a separate hardware platform. For example, if one copy is saved to a NAS appliance, then a second copy should be stored on a tape library and the third copy kept off-site.
Storing backups in two separate hardware platforms affords maximum protection from hardware failure, because each device is less prone to issues. In addition, keeping copies on separate devices minimizes exposure in the event of a ransomware incident.
Two Types of Storage
Copies of data should be stored on two separate types of storage. This includes traditional disk-based storage as well as a secondary non-volatile or offline copy, such as a tape library or cloud backup service.
One Offsite Backup Copy
Keeping a copy of your data in the cloud is an effective way to ensure that one is available off-site. In addition, as more and more businesses are relying on the cloud for IT services, it is important to have an up-to-date copy of production data readily available in the event of a disaster. Maintaining an off-site copy provides peace of mind for IT administrators knowing that they can quickly access backup data if needed.
Why should I implement the 3-2-1 Backup Rule?
You can never be too safe when it comes to protecting your business’s valuable data. The 3-2-1 Backup strategy works toward complementing traditional disaster recovery (BDR) and business continuity planning strategies through its protection against multiple types of threats, instead of just one specific kind.
It is particularly effective because viruses and malware are not the only dangers businesses face in today’s interconnected world. Data can be maliciously encrypted or become corrupted without warning due to a system crash, ransomware attack, network failure, human error, acts of nature such as floods and fires, etc. If you have a robust 3-2-1 strategy in place, you will be better prepared for any eventuality.
How to prepare for the 3-2-1 backup strategy?
Implementing the 3-2-1 Backup Rule requires multiple backup jobs, different types of storage media, and an infrastructure that can support continuous data protection.
Different Types of Storage Media
Being prepared for the 3-2-1 strategy means having access to different types of storage media so you can store multiple copies of your data on different platforms.
There are many ways to get the necessary hardware depending on your budget and IT infrastructure, including purchasing new hardware or utilizing existing storage that is already in place.
Calculate Recovery Time Objectives (RTOs) and Recovery Points Objectives (RPOs)
Recovery Time Objectives (RTOs) define how quick you need to recover your data whereas Recovery Point Objectives (RPOs) specify how much data can your business/organization afford to lose.
By calculating RTOs and RPOs, you’ll be able to determine specifics such as:
- How often should your backup jobs be scheduled: hourly, daily, or weekly.
- How many terabytes (TBs) of data you need to recover to restore critical business operations (disaster recovery).
- Do you need features such as continuous data protection (real-time replication) with automated failover and failback.
Plan Ahead and Assess Resource Consumption Accordingly
3-2-1 backup strategy requires running data protection jobs on a regular basis in order to maintain multiple offline copies of the original production data. As a result, the storage and performance requirements increase proportionally.
For example, if you’re running replication jobs in real-time (synchronous replication) and storing copies of your data in a private cloud or a clustered node, then the performance and bandwidth consumption will be higher.
In comparison, if you’re running daily backup jobs and storing backups on-premises and later replicating to offsite cloud volumes, the resource consumption will be much lower.
Make and Test Backup and Recovery Plan(s)
A comprehensive recovery plan should be created for all potential scenarios. This can include developing failover plans in the event of a ransomware attack, hiring data forensics experts if critical files are lost due to malicious deletion or corruption, etc.
Properly testing your recovery plan is equally as important as creating it. It is critical to periodically test all of your backup processes and strategy, by running through different types of data loss events to ensure that you are able to restore business operations quickly.
It goes without saying that your backup and recovery plans should be made and tested in accordance to your Recovery Time and Recovery Point Objectives (RTPOs).
How can I implement the 3-2-1 backup rule?
In order to maximize protection against data loss, it is important that businesses have a comprehensive plan in place to meet these three requirements. This includes setting up a proper storage infrastructure with offsite copies of data and building out a solid recovery plan.
Hybrid Storage Infrastructure
Setting up a properly configured storage infrastructure is critical in maintaining three separate copies of your business’s most valuable data. Ensuring that the hardware architecture supports deduplication and compression technologies further reduces amount of space required. These elements are just a few of important capabilities an effective storage infrastructure needs to have in place.
Furthermore, integrated cloud connect is a useful feature to have especially if you’re looking to store backup copies in offsite air-gapped repositories.
Be Sure to Add Air-Gapping
While you can never be too cautious when it comes to data protection, implementing an air-gapped backup copy and storing it offsite makes for a more comprehensive ransomware-proof plan.
Air-gapping can be implemented in a number of ways, including:
- Configure air-gapped repositories in public/private clouds and integrating them with your hybrid storage infrastructure.
- Leverage purpose-built air-gapped nodes with automated network and power management.
- Reclaim and repurpose unused storage space to set up virtual air-gapped repositories.
- Manually offload and copy backup copies in tape arrays. (Not recommended as the process is prone to human error and risks business continuity)
Conclusion
The 3-2-1 backup rule is a simple yet effective way to protect your critical data from threats like ransomware, malicious deletion, human error and natural disasters.
With the increasing adoption of the hybrid workspace and interconnected critical business IT systems, the possibility of data loss and downtime has grown proportionally as ransomware attacks have honed in vulnerable networks. As a result, making the 3-2-1 backup strategy a must-have for all businesses and organizations that rely on their digital assets for day-to-day operations.
Need help setting up 3-2-1 backup for your business/organization? We can help! Contact StoneFly sales to discuss your projects today.









