Backup files can be used to create replication copies. If you do a local backup into a backup repository you can use that to build replicas restore points at the Disaster Recovery location. First, you do backup and then a replica based on those backup files.
What if Customers don’t have a Disaster Recovery site?
Customers can use the StoneFly Cloud Connect and StoneFly can act as their DR location. StoneFly provides a cloud gateway that allows customers to send data up using a single SSL data encrypted communication to get their virtual machine up into the StoneFly private cloud, Microsoft Azure Cloud or Amazon AWS Cloud.
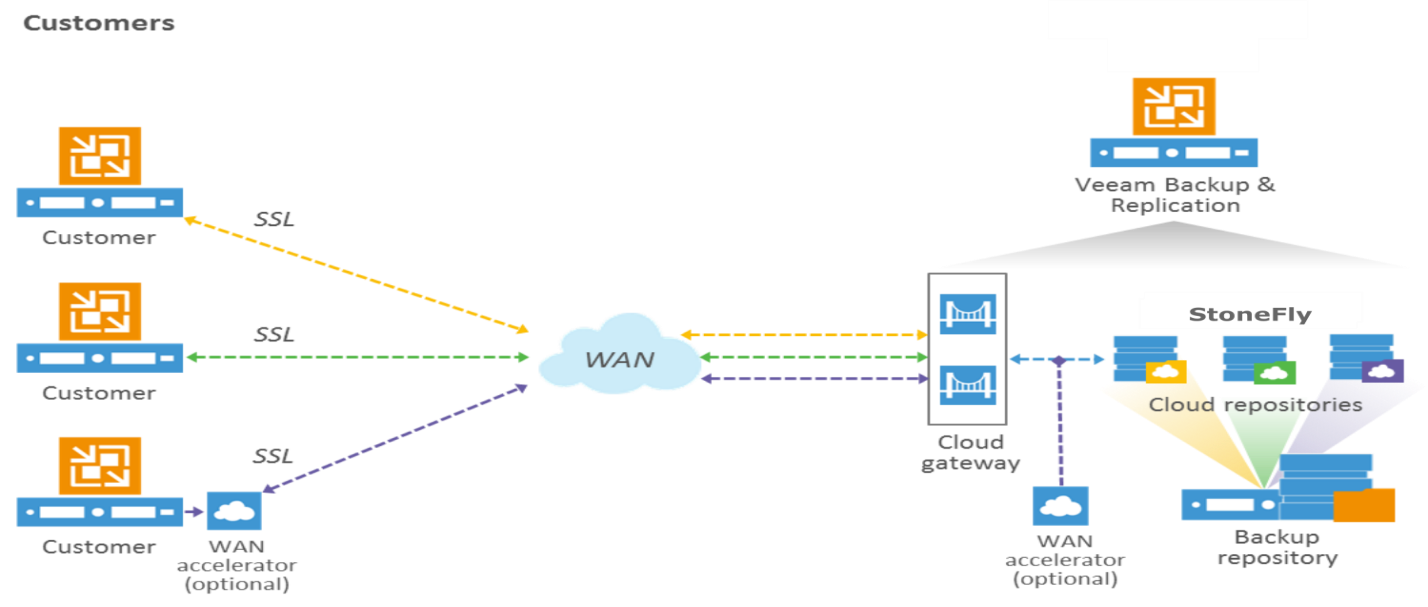
Customers can also do the multi-step process and it will send data up to the cloud. Customers will do a local backup into a backup repository then they will send it to StoneFly cloud repository using Cloud connect and then it will be used to create replicas restore points.
StoneFly has the Veeam backup server with a Cloud Connect license installed in it. This license allows StoneFly to act as Cloud connect service provider. It allows StoneFly to deploy their components which include the cloud host. Customers are also able to deploy regular VM components such as proxies. This allows users to log in and then run their failover plans in the event that their site is not available. StoneFly can deploy a cloud repository to hold customers backup files and also can deploy WAN accelerators and define hardware plans.
How much space does the customer need for the Data Storage?
This is a common question which comes to customers mind that how much space they need for the data storage. It should be at least as much as their current VM size plus snapshot space. One of the good things about data replication jobs are that customers are able to keep multiple replicas restores points. The size of the disk will remain the same but they are going to need some space for the data storage snapshots.
StoneFly will provide the extra space than what customers do have in the production.
Each customer is assigned with a hardware plan in StoneFly environment. In it there is a space for network extension appliance. It allows users to configure the networking for their StoneFly environment.
Sure backups allow users to create a virtual lab. Virtual lab is an isolated bubble that runs in an environment. Inside that bubble customers are able to power on VMs and the VMs are able to communicate with each other. But they are not going to conflict with their production counter parts. Customers can run some checks like the ping, heartbeat, check whether the applications are responding in the way they want it and after all that Clients will generate the response to the admin that we want to use these replicas










