In a world of
What is data encryption?
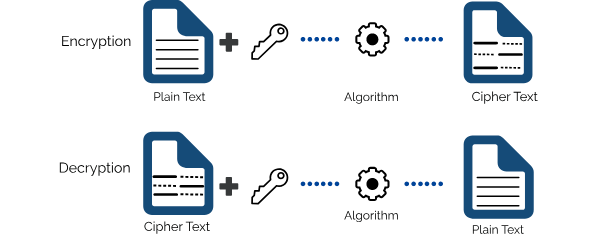
In order to save private data from malicious attacks or hacks, data encryption is used. This method is not new. In the past, kings used to send battle tactics to their soldiers using a coded language, readable only to his people. data encryption these days works with the same concept but the structure is different. Now we use electronic devices to generate unique data encryption algorithms to scramble our data. It is the method by which a plaintext or any type of data is encoded. The encoded data can only be decoded by the person who has the decryption key. This method keeps the data protected. The encrypted data is commonly referred to as the cipher text, while unencrypted data is called plain text.
What is storage encryption?
Storage encryption means the use of encryption/decryption for backed-up and archived data, both in transit and on storage media. All products of StoneFly deliver encryption to facilitate data security.
Types of data encryption:
When it comes to data encryption there are two major types: asymmetric encryption, also known as public-key encryption, and symmetric encryption.
Symmetric-key data encryption:
This type of data encryption uses the identical keys or the codes for the computers involved in the message transmission. Each secret key’s data packet is self-encrypted. The symmetric encryption will be according to the Data Encryption Standard (DES), which uses a 56-bit key, although it is not considered to be attack-proof. The Advanced Encryption Standard (AES) is considered more reliable because it uses a 128-bit, a 192-bit or a 256-bit key.

Asymmetric-key data encryption:
The asymmetric key encryption is also known to be the public key encryption uses private and public keys. The public key is shared with all the computers which want to connect with the user’s computer. Although the private matching key remains private to the user’s computers and it decrypts the message and makes it readable according to the public key encryption system. The keys are paired together but they are not identical. One key that is the public key can be shared with everyone and the other key is the private key that is kept in private. For example the IT administrator who will encrypt the data will possess the two keys that locks the data. The public key will be available for anyone. The private key is kept private. The message which will be encrypted by the public key will be decrypted only by using the private key, while the message encrypted using the private key can be decrypted by using the public key. The process is called public key cryptography.

Why and when is data encryption used?
Encryption is essential to ensure the security of sensitive information being transferred. It is the method that provides data security and end-to-end protection of data that is transmitted across the networks. It is used by organizations to ensure the data security of their data Organizations also use encryption to protect stored data on computers, servers and mobile devices like phones or tablets.
How data encryption works ?
Encrypted data is formed by using an encryption algorithm and an encryption key. This process then generates the Cipher text (encrypted data) which can be viewed in the original form if it is decrypted with the correct encryption key.
Among the types of encryption, Symmetric key encryption is more mainstream; it uses Advanced Encryption Standard (AES) for encryption. If this data is transmitted, the sender has to provide the received with the decryption key. The asymmetric cryptography uses the two different links which are linked with each other. The public key can be shared with everyone whereas, the private key will be kept secret. This attribute provides a method of assuring not only
Encrypting Data “In Transit” vs. Data “At Rest”
Data transmission handles two basic types of data: the data at rest and data in transit.
In other words, when data is being transmitted it’s in transit and when it has reached its destination or prior to the data transmission process, it’s at rest.
Encrypting Data at Rest:
Data at rest can be encrypted through:
- Full Disk Encryption (FDE):
This the primary way to protect data at rest. When you save a file on disk or hard drive or a file-level storage, the data will be automatically encrypted. There are many options for disk encryption, like folder encryption, volume encryption, etc.
- File encryption:
File encryption encrypts data at rest on a file to file basis. Unlike FDE, File encryption is not an automated encryption process.

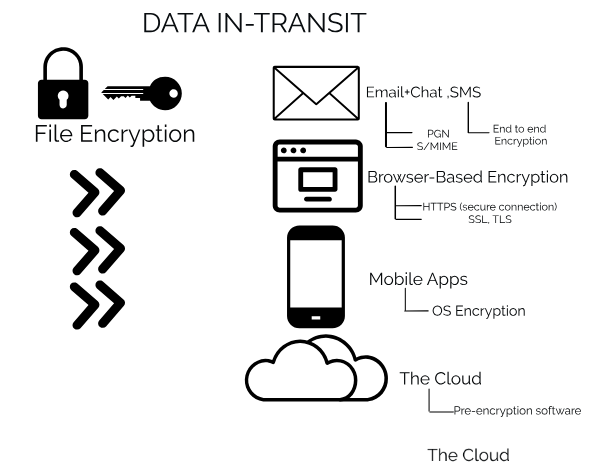
Encrypting Data in transit:
When data is in transit it can be encrypted through these processes:
- End-to-end (E2E) encryption:
It makes the data or messages only visible to the senders and receivers. E2E controls the liabilities on the communication chain and the message is encrypted during the delivery at both ends.
- Encrypted web connections:
The HTTPS, encrypted web connections use a Secure Sockets Layer (SSL) or transport layer security (TLS) protocols. These are secure internet connections which allow better and protected communications on the web.
- Encrypted email servers:
S/MIME (Secure/Multipurpose Internet Mail Extensions) public key encryption gives an edge to email servers to send and receive encrypted messages not simple texts.
- Pre-encrypting data:
There are software that can pre-encrypt the data before it is transmitted. The pre-encrypting data is inaccessible to the cloud service provider or any hacker.
Encryption is a secret key but it is complex. If you use Advanced Encryption Standard (AES) then, the key is lengthy and complex. It is difficult to handle the encryption and decryption of data.
Benefits of data encryption:
The primary function of data encryption is to protect data which is stored on-premises Network Attached Storage (NAS) or Storage Area Network (SAN), or transmitted through internet or any other computer. data encryption has the following key elements of security:
These key elements of data encryption leads to some amazing benefits:
- Protect Data:
The data is protected through data encryption. Suppose that the file is encrypted with 256-bit AES it will take a lifetime to crack the code.
- Security available on multiple devices:
Accessibility and device independency is a crucial part of most enterprise environments. Encryption removes the risk of data breach and unauthorized access. It ensures that the data remains secure regardless of the device on which it is stored and accessed.
- Secure Transmission:
During transmission the data is secured through encryption. Encryption techniques like E2E will ensure data remains protected.
- Integrity:
Integrity ensures that the contents of the message or data are not changed since it was sent.
- Confidentiality:
Data encryption prevents unauthorized access to data, maintaining confidentiality. This can be done by monitoring the flow of decryption keys.
- Data Integrity:
The lack of protection measures result in data leakage or a data breach; this in turn results in reputation damage and sometimes substantial financial repercussions.
Data encryption technology prevents data breaches and deliver enhanced data integrity.
- Ensure Compliance:
Most compliance regulations observe strict policies pertaining to data security. Data encryption technology plays a vital role in delivering data protection and enabling organizations to remain compliant.







