Why is there a Need for Data Protection and Disaster Recovery Using the Cloud?
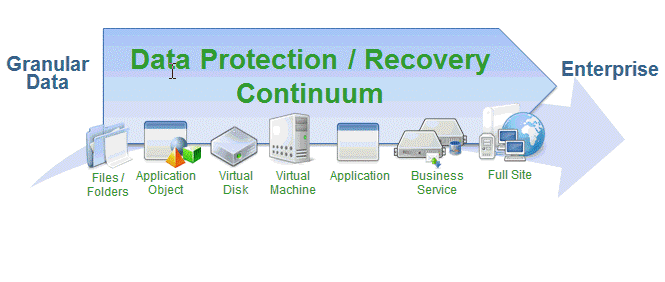
Disaster Recovery is the process of restoring a failed service, application or the operations of an entire datacenter to full operational status following a disaster. This includes human-caused or natural disasters. Having a disaster recovery setup in place is essential for ensuring business continuity.
Data Protection
Data Protection is also known as backup and restore. It is the process of protecting data from loss, corruption or accidental deletion. The conventional methods of data storage are becoming obsolete with innovations in technology every day.
The conventional solutions of data protection and disaster recovery have been looked at as setting up a very own datacenter. However, there are various problems related to storage challenges of setting up a very own datacenter.
IT Storage Challenges
- Increased Capital: Setting up your+ very own datacenter for data protection and disaster recovery will require a lot of initial costs to set up.
- Various Storage Options: Organizations around the world require various different options for data storage. Setting up a very own datacenter would require a lot of hassle to choose the right storage.
- Need for Experts: Experts would be required to run the datacenter. It will add to the costs of the organization.
- Lack of Flexibility: Once the datacenter has been made, more space cannot be added and the organization will be stuck with only a certain amount of storage.
What Matters Most in Data Protection and Disaster Recovery?
The primary storage you deploy in your corporate datacenters and other locations can make a huge difference to the success of your data protection and disaster recovery efforts. Below are some of the attributes you need to look into before choosing appropriate solutions for data protection and disaster recovery.
Core Necessities
The storage solution must include replication, cloning and snapshots. These modern technologies lay the foundations of a good disaster recovery and data protection plan.
Scalability and Flexibility
Organizations need to think ahead in terms of data protection and disaster recovery – by keeping in mind a landscape of data protection and disaster recovery which is open and scalable in the cloud.
Data Efficiency
Storage capacities and WAN bandwidth needs to be saved through essential efficiency features like deduplication, compression and other such features.
Ecosystem Integration
Your storage solution should integrate with all disaster recovery and data protection elements including other data, hardware, hypervisors, protection software, etc.
Automation
All disaster recovery and data protection functions must be easily automated to enable DevOPs and private cloud, save time and reduce errors.
Control
Visibility of all storage functions, the disaster recovery and data protection aspects can eliminate unwelcome surprises.
Businesses have prioritized data backup and disaster recovery with the turn of the century. Business continuity demands disaster recovery in the cloud. The partnership between the likes of StoneFly, Microsoft Azure and Amazon AWS provide the customers with secure off-site backup and replication. The StoneFly Cloud Connect to Microsoft Azure Storage provides intact cloud storage to users.
Cloud storage provides many other benefits to users like file-versioning, which allows for multiple variants of an object to be stored within the provided space. This form of storage helps to preserve space, retrieve and restore various versions of the data. Cloud storage can hence help in quick disaster recovery by remaking the entire production environment in a matter of minutes.
![backup[1]](https://staging.stonefly.com/wp-content/uploads/2018/02/backup1.jpg)









