Ransomware attacks are on the rise, and ransomware recovery is a topic of concern for many business owners. If ransomware encrypts your data, how do you recover it? In this blog post we’ll answer this question and more.
How Ransomware Attacks Your IT Systems
Before we dive into ransomware recovery, it’s important to understand how ransomware attacks business IT systems.
Ransomware is a type of malware that encrypts data and makes the data unusable without proper decryption keys. Once ransomware has encrypted your files, you won’t be able to access them unless you pay for the key or restore from backups (more on this later).
In addition to encrypting your important files, a more recent trend involves ransomware stealing valuable data and threatening to make public as part of a double extortion attack.
There are a number of ways a ransomware attack gains access to and infects your storage devices; which can be classified in three main types:
- Exploiting Human Error
- Target Vulnerabilities of Your IT System(s)
- Attacking Service Providers (Supply Chain Attacks)
Exploiting Human Error
Sophisticated ransomware attacks employ social engineering to fool your employs and IT staff into making a mistake which leads to releasing a ransomware attack on the business network. As human error continues to be the leading cause of downtime and successful ransomware attacks, evidently ransomware groups are getting exceedingly good at it.
The most common way to deliver malware by exploiting human error is via phishing emails.
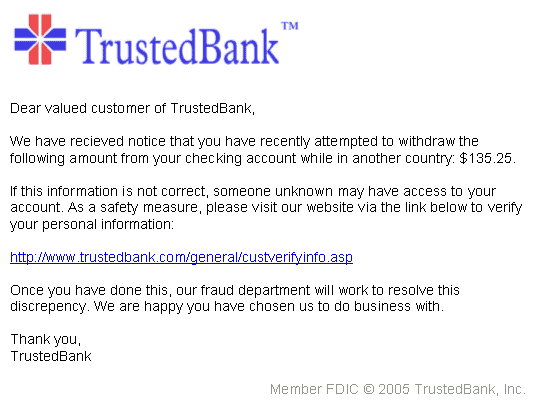
(source: Wikipedia)
The above image shows an example of a phishing email from a fictional bank. Phishing emails are designed to trick the recipient into visiting a website, downloading an attachment or clicking on a link which then downloads the ransomware leading to encrypted files, an infection of the entire infrastructure, and downtime.
A recent example of a phishing email is the Dridex malware campaign. Dridex sends employee termination letters with a password-protect Excel worksheet attachment supposed to contain detailed information as to why they’re being fired. Once downloaded and the password is entered, the Excel file shows a blurry image of a “Personnel Action Form” asking the recipient to “Enable Content” to see it clearly. When the recipient does so, it displays a pop-up with the message “”Merry X-Mas Dear Employees!”” while the malicious code is executed on the backend, encrypting files and stealing critical data.
Targeting Vulnerabilities in Your IT System(s)
In 2021, the second most common method of delivering ransomware was directly attacking computers and server(s) by targeting known vulnerabilities in open source and popular operating systems, applications, and virtual environments.
A few ransomware attack examples that targeted vulnerabilities of popular operating systems, virtual environments, and open source applications:
- Log4Shell: a RCE exploit vulnerability in the Log4j logging service developed by Apache and widely used by web applications and software using Java language.
- eChoraix ransomware (also known as QNAPCrypt) targets network attached storage devices by creating a user in the administrative group which allows it to encrypt data stored in the NAS appliances.
- Conti ransomware, known for their high-profile attacks on Ireland’s Health Service Executive (HSE) and Department of Health (DoH), the City of Tulsa, and Advantech, commonly breaches a company’s network by using BazarLoader or Trickbot malware infections, which provides remote access to the cyber criminals.
- Babuk ransomware exploits the ProxyShell vulnerability of Microsoft Exchange servers to infect it with a dll or .net executable. The w3wp.exe IIS worker process executes the malicious code to run a PowerShell command that bypasses endpoint protection and invokes a web request fetching a payloader called “tortilla.exe”.
Ransomware Attacks on Service Providers (Supply Chain Attack)
Comparatively less common but no less devastating are supply chain attacks. Supply chain attacks, also called third-party attacks or value-chain attacks, target your confidential data by attacking service provider(s).
Two prominent examples of supply chain attacks that have wreaked havoc and disrupted government and corporate operations worldwide:
- Kaseya VSA, a popular IT management and cloud solution, was attacked by REvil ransomware, which affected thousands of businesses, servers, and workstations including managed service providers (MSPs) and government legislation.
- A ransomware attack on SolarWinds affected several US government departments including department of treasury, department of state, department of homeland security, and service providers such as Microsoft and CISCO. A malware named “SunSpot” was injected into the SolarWinds network which then created the “Sunburst” backdoor in their development environment. The Sunburst backdoor was then spread to SolarWind customers using automatic updates for the SolarWind Orion platform. Once executed, the infected devices would routinely connect to a remote control and command server.
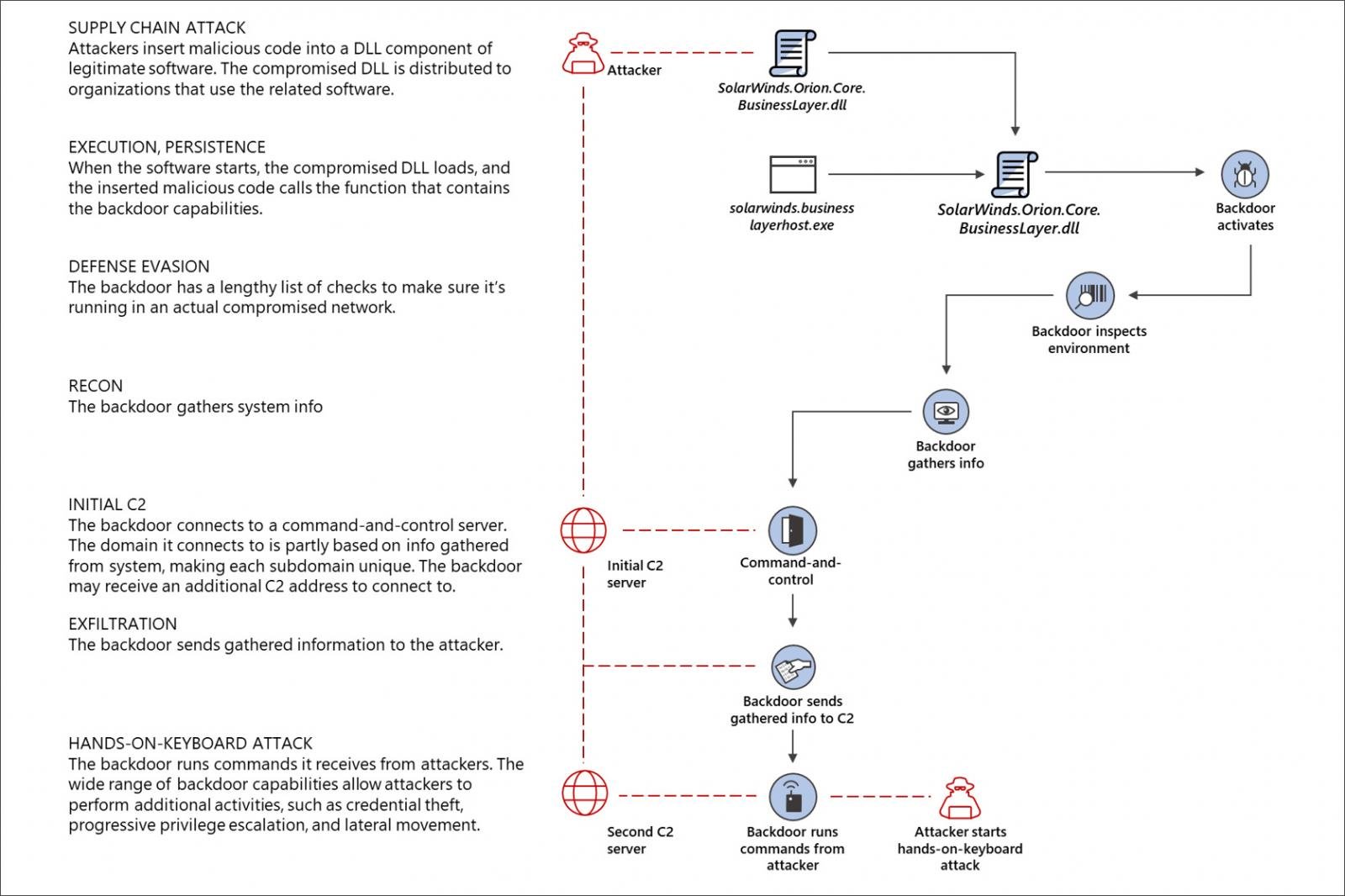
SolarWinds Supply Chain Attack (source: Microsoft)
Can ransomware infect recovery partitions?
Whether ransomware can infect your recovery partitions, or not, depends on a number of factors such as the data protection measures you’ve configured, where your backup data is stored, if you have a recovery plan, what measures you’ve setup to prevent ransomware from gaining access to your sensitive data, and more.
To make it easier, here are four questions you need to ask yourself (and/or your IT staff):
- Do you use immutable backups?
- Is your backup data (or a copy of it) retained in an offline and air-gapped repository?
- Do you use data encryption at rest, in transit, and for active data sets?
- Does your backup solution follow the 3-2-1, 3-2-1-1-1, or 4-3-2 backup strategy?
If the answer to these questions is a ‘yes’, then there’s slim to no chance that ransomware can infect your recovery partition.
Alternatively, if the answer is ‘no’, then your sensitive data is vulnerable and it’s likely that a ransomware attack will not only infect your production environment but also your backups and recovery partitions; making data recovery difficult and data loss inevitable.
How to recover ransomware encrypted files?
The ability to recover ransomware encrypted files depends on the type of ransomware attack, and whether or not there’s a decryption key available.
The “No More Ransomware” project is known to host a number of decryption tools for several infamous and active ransomware. If your important files have been encrypted, it’s a good idea to check their list. There’s a chance you might be able to restore files and recover from a ransomware without having to pay the ransom.
Data recovery also greatly depends on the data protection setup beforehand. For example, if you have offline backups , then it’s likely that they’ll remain unaffected by ransomware and you can restore encrypted files after removing ransomware.
Similarly, immutable backups, air-gapping, delta-based snapshots, and encryption also enhance the ability to recover ransomware encrypted files.
Note: Before attempting to restore data, it’s important to use tools that effectively remove ransomware from the affected environment(s).
How long does it take to recover from ransomware?
Ransomware recovery can take from a few days, to weeks, to even months. Once again, it depends on the pre-emptive data security measures setup beforehand.
For instance, if you have an unaffected backup copy of your critical data, then disaster recovery shouldn’t take long. Conversely, if your backups are compromised, then it will take longer and you will end up losing data depending on your last recovery point. In the worst case, if you did not have adequate backup set up, then you may be looking at major data loss and consequent financial losses.
To accelerate recovery from ransomware, it’s important to have a ransomware protection plan and regularly test it by simulating “cyber-incidents”. Furthermore, the time it takes to restore business operations depend on how frequently your critical data is backed up. This implies that the frequent the backups, snapshots, and replicas, the shorter the recovery point will be.
How to stop ransomware from encrypting your data
There are a number of ransomware prevention and data security measures you can implement to stop ransomware from affecting your data. However, cyber-criminals are coming up with more sophisticated means of infecting your critical systems with each ransomware attack. It’s necessary to anticipate and plan for the possibility of a ransomware infection.
This goes without saying that while no ransomware prevention measure is a 100% effective, it is important regardless.
The best solution to ransomware is to devise and implement a comprehensive ransomware protection plan that covers:
- Ransomware prevention measures such as firewalls, anti-ransomware, multi-factor authentication, etc.
- Backup and disaster recovery solutions that facilitate ransomware recovery and ensure business continuity with features such as air-gapping, immutability, encryption, and snapshots.
- Ransomware recovery measures that reduce downtime and facilitate quick recovery with features such as direct VM spin up, granular file-level restore, full VM recovery, direct restore to cloud, etc.
Note: Backup and disaster recovery solutions do not stop ransomware from encrypting your data. They are a means to prevent data loss, reduce downtime, ensure business continuity, and restore business operations as quickly as possible.
What to do if ransomware encrypts your data
If a ransomware attack bypasses your data security measures, here’s what your response should look like:
- Isolate the ransomware infection
- Inform relevant authorities
- Try to remove the ransomware
- Start ransomware recovery or start anew
Isolate the ransomware infection
Detection and isolation is a critical aspect of reducing the damage dealt by ransomware. In order to isolate ransomware infection, disconnect the encrypted computer(s), server(s), and virtual environment(s) from the network, shared storage, external storage, and cloud environment(s).
The quicker you disconnect your infected devices from your network, the less damage a ransomware attack can do, and the easier ransomware recovery will be.
Inform relevant authorities about the ransomware attack
While the ransom note makes it sound like paying the ransom is the only option you have, it’s not recommended. After confirming a ransomware attack, it’s important to inform the relevant authorities so they can help.
If you’re a business in the USA, you need to contact your local FBI office and file a compliant with IC3.
Not only will this help you but also help authorities understand the threat to prevent more ransomware infections.
Try to remove the ransomware (System restore might not help)
Involve cyber-security experts to your in-house IT personnel with effective removal of the ransomware.
If you’re a small business with limited to no budget, check for a decryption tool online, the “No Ransom Project” is one good example that can help.
While a system restore may sound like a fix, it’s likely that it will not work and that’s because most ransomware are programmed to bypass such measures. It’s important to note that a system restore does not take into account your files when it creates a snapshot. Unlike a backup, even if you successfully perform a system restore, you will still lose important data.
In the worst case, if you have the backups, you may have to consider a complete wipe, and then reinstalling your operating systems and virtual environment(s).
Start recovery or Start anew (Don’t pay the ransom)
After completely removing the ransomware from your production and all infected devices, you can begin the process of ransomware recovery.
Depending on whether or not you had backups, you may be able to minimize data loss and recover quickly. Or you’ll have to have to reinstall your environment(s) and start afresh.
Either way, even if the ransom note makes it sound like paying the ransom is a viable option, it’s not. Cybersecurity experts and government authorities strongly suggest not to pay the ransom as it only fuels the cyber-criminal industry incentivizing criminals to continue to steal.
Furthermore, while there’s a chance that you might be able to recover your data, there’s no guarantee that they won’t do it again or that they will completely remove the malware which gives them remote access to your network.
How would backup and recovery mitigate the risk of ransomware attacks?
Ransomware infiltrates your network and encrypts your important files and sensitive data preventing access and disrupting work. Backup and recovery enables you to bypass the encryption by restoring data – after you have completely removed the malware.
The primary goal of a ransomware attack is to hold your data for ransom. Backup ensures that you’re able to regain access to it without having to do that which solves the major risk involved with ransomware attacks.
However, there’s more to it than that. Ransomware targets not just your production but also your backup servers attempting to encrypt your backups in addition to the original copy. This implies that while backup and recovery does help mitigate the risk of ransomware attacks, it is rendered useless if it doesn’t have the right data security features.
For example, as ransomware uses the network to infect all connected devices and shared storage, it’s important to use features such as air-gapping which isolate your backups. Similarly, using immutable backups also adds to ransomware protection as the data stored in these volumes cannot be edited, deleted, or overwritten.
It is also important to bear in mind that backup and disaster recovery are not a preventive measure. They do not stop ransomware from attacking your network. They provide the means to recover from a ransomware, restore data, and reduce downtime.
How StoneFly Provides the Best Ransomware Recovery Services
StoneFly storage, hyperconverged, and backup and disaster recovery (DR) solutions come with built-in ransomware protection features such as air-gapping, immutability, S3 object lockdown, file lockdown, Write-Once Read-Many (WORM) volumes, encryption, anti-ransomware, dormant malware detection and removal, and more.
In addition to the purpose-built turnkey hardware that provide the complete data center experience, StoneFly also provides physical, virtual, and cloud-based solutions for customers not looking to replace their data center completely rather compliment them with reliable data protection.
Fully turnkey backup and DR appliances that provide the complete data center experience:
- StoneFly DR365V: Turnkey Veeam-ready fully integrated solution that combines hyperconvergence, backup & DR, cloud connect, and secure SAN, NAS, and S3 target repositories in a highly scalable, and hyper-available system.
- StoneFly DR365U: Turnkey universal backup and DR with hyperconvergence, your choice of backup software, cloud connect, and SAN, NAS, and S3 target storage in a highly scalable and available system.
- StoneFly miniBackup: Affordable backup and DR appliance with terabytes of on-prem storage, optional cloud connect, and optional support for external storage with round robin backups.
Physical appliances that you can add to your existing environment include:
- StoneFly DR365 Veeam-Immutable Veeam Air-Gapped (VIVA) nodes: Purpose-built fully automated immutable and air-gapped backup and disaster recovery node with integrated policy-based network and power management.
- StoneFly BG365 Backup Gateway: All-in-one virtualized backup and disaster recovery gateway compatible with mainstream backup software, Windows/Linux servers, public clouds, and virtual environments.
Virtual appliance that enable you to repurpose unused storage resources and provision highly secure air-gapped and immutable on-prem target storage repositories:
- StoneFly SCVM™ – Software Defined Storage (SDS) solution compatible with VMware, Hyper-V, KVM, and Citrix (formerly XenServer) and able to provision virtual SAN, NAS, and S3 object with air-gapping, immutability, and more.
Cloud storage that supports data security features:
- StoneFly cloud storage is available on Azure marketplace and comes with built-in data security features such as air-gapping, file lockdown, S3 object lockdown, encryption, snapshots, and more.
- StoneFly private cloud can be customized to suit your performance and budget requirements and provides data protection features such as air-gapped backups, file lockdown, S3 object lockdown, encryption, snapshots, failover clusters, and more.
Conclusion
With ransomware attacks growing more sophisticated by the minute, ransomware recovery has become a necessity for every organization that relies on their digital assets for day-to-day operations.
With the right backup and recovery solutions, you can protect your sensitive information and critical assets from data loss and ensure business continuity.
How to pick the right ransomware recovery solution for your business? We can help. Talk to our experts, share your projects, and build a ransomware protection solution your business can rely on!










