Ransomware attacks cost businesses millions yearly. The cyber-threat continues to grow sophisticated and dangerous with the passage of time. In this blog post, we take a closer look at ransomware, and share why as a data owner you should be wary of and prepared for ransomware attacks.
Who ransomware attacks target?

In a word, everyone. Everyone who owns data, that they hold valuable, is now a potential target for ransomware attacks. This includes small organizations, mid-tier, and large businesses.
WannaCry, the ransomware that brought the cyber-threat into limelight again, started from a single user and spread to infect hospitals, businesses, and over 200,000 vulnerable targets. Clearly showing that cyber-criminals are simply financially motivated and do not act in accordance to some ethical code. They will target anyone to earn an “extra buck”, even if it puts lives in danger.
Post COVID-19 ransomware targets: Everyone working from home & Healthcare

Now that a major part of the global workforce has moved to remote work (or work from home), ransomware attackers have shifted gears too.
With everyone sharing sensitive business data over the wire, ransomware hackers are now looking to cripple said channels and exploit known vulnerabilities. Now, more than ever, it is imperative that data owners are prepared to fend off ransomware infections should they find themselves facing one.
Additionally, now that healthcare has become ever more important, cyber-criminals have increased their efforts into targeting hospitals and critical health systems.
Earlier April 2020, Interpol warned against the possible damage online extortionists can do stating that they had seen significant increase in attempted ransomware attacks against key organizations in the COVID-19 response (source: ZDnet).
How ransomware attacks?

One of the most common and known ways for ransomware attacks are phishing emails.
Phishing emails are cleverly written socially engineered emails that “persuade” the recipient to click on a link or download an attachment. If successful, the link or download accesses sensitive information and grants access to ransomware.
While common, phishing emails are not the only way ransomware attacks. Other means of ransomware infection include exploiting known vulnerabilities and purposefully malicious designed web content.
For instance, WannaCry infection spread after exploiting a known vulnerability in Windows.
One of the most common and known ways for ransomware attacks are phishing emails.
Phishing emails are cleverly written socially engineered emails that “persuade” the recipient to click on a link or download an attachment. If successful, the link or download accesses sensitive information and grants access to ransomware.
While common, phishing emails are not the only way ransomware attacks. Other means of ransomware infection include exploiting known vulnerabilities and purposefully malicious designed web content.
For instance, WannaCry infection spread after exploiting a known vulnerability in Windows.
How ransomware spreads?
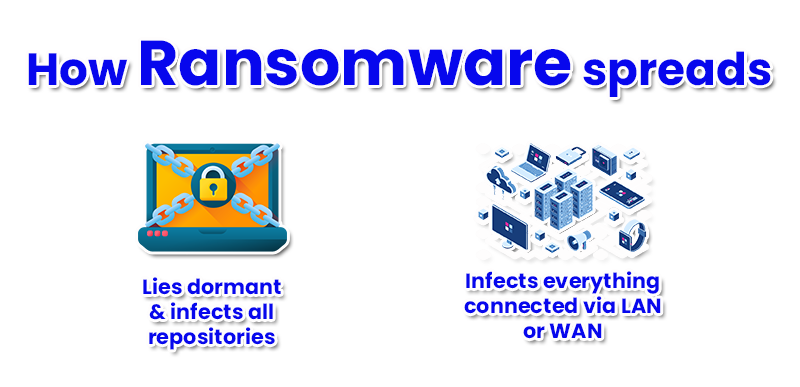
Ransomware spreads by copying itself to all connected systems and servers in the network but it doesn’t stop there.
Most ransomware attacks are designed to work in two stages. At stage one, the ransomware lies dormant and records user activity to find mapped drives, and frequently used storage repositories (local, offsite and/or cloud); and copies itself to said repositories. In stage two, the ransomware becomes active encrypting all locations simultaneously.
In other words, one mistakenly downloaded attachment or accessed website can lead to the infection of all target storage repositories and hundreds of thousands of systems; as was the case with WannaCry and Petya.
How much ransomware attacks cost?
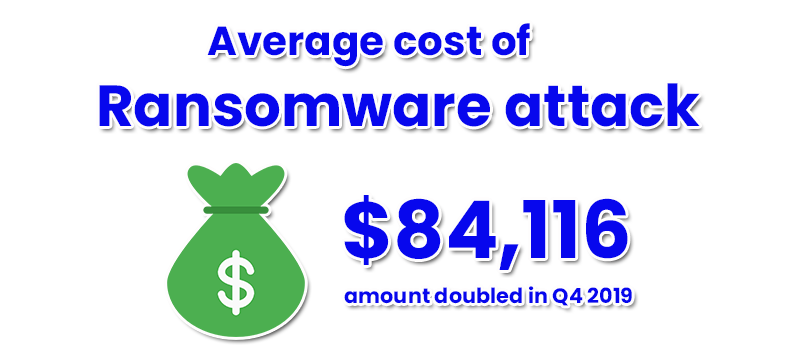
In the last quarter of 2019, the average cost of ransomware attack doubled from $41,198 to $84,116 (source: Coveware).
However, the cost of ransomware varies depending on the volume of compromised data and the industry (healthcare, finance, IT, government department, etc.). For instance, cyber-criminals are more likely to put more value to healthcare data at this time than any other industry. Similarly, successful ransomware attacks on cities have led to millions in losses.
The typical cost of ransomware includes the ransom payment, the cost of downtime, and the maintenance cost it takes to get operations back up and running.
How long does it take to recover from a successful ransomware attack?
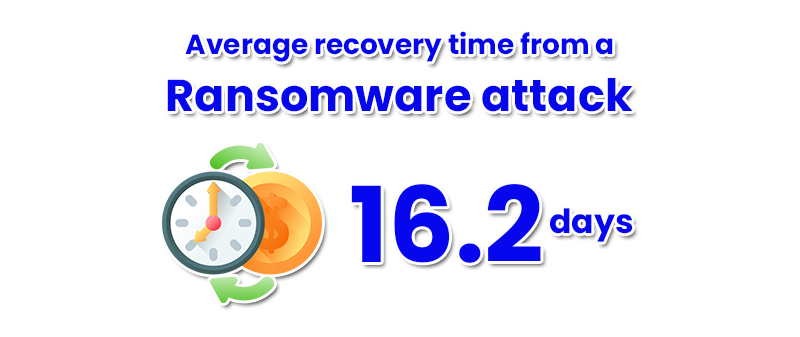
On average, a ransomware attack incident lasts 16.2 days (source: Coveware). Recovery from a ransomware attack depends on the means employed to do so.
(Not Recommended) If you pay the ransom
Note: The US department of treasury advises against paying ransom or any consultation facilitating ransomware payments. (Learn more)
If you decide to pay the ransom, which is not recommended by security experts, there are two possibilities:
- You’ll get the decryptor and get your data back
- The hacker will disappear with the money & you will lose your data regardless
According to Coveware, 98% who paid got decryptors and were able to recover 97% of their encrypted data whereas 3% of the data was lost.
Disclaimer: StoneFly highly discourages organizations to pay ransom as it encourages cyber-criminals and funds their future efforts.
If you don’t pay the ransom
If you decide not to pay the ransom, the outcome depends on how prepared your infrastructure was prior to the ransomware attack.
If you had ransomware protection setup beforehand then it’s a simple matter of recovering your data from the backups.
On the other hand, if you weren’t prepared, then it can take several days to weeks or months depending on how sophisticated the ransomware is. Even then, the likelihood of data recovery is questionable. In this case, recovery times vary on a case by case basis.
How to prepare for ransomware attacks?

While the risk of data and financial loss is great if you’re unprepared, however, if you’re prepared then the disaster can be avoided.
Here are some tips to help you prepare your organization to resist ransomware attacks:
- Backup everything: Get a reliable backup & DR solution to setup a way to recover in the event of a successful ransomware attack.
- Anti-ransomware: Make anti-ransomware programs a necessary component of your file storage systems, desktops, and other equipment.
- Firewall: Configuring a secure firewall to secure your data networks is also a recommended practice.
The best way to ensure ransomware protection is to use a complete backup and DR solution that combines backup software, storage OS, virtualization, and target storage in a turnkey appliance. And that’s exactly what StoneFly DR365V does, learn more: https://staging.stonefly.com/backup/dr365-for-veeam
Conclusion
A successful ransomware attack can cost you your critical data, your reputation, and if it lasts long enough, even your business.
As the global workforce shifts to work from home, the threat of ransomware has only become greater. This is the time to plan ahead and prepare so that when confronted with a ransomware attack, you have the means to resist it and recover from it; if necessary.
Relevant Resources
- Cyber-criminals are exploiting COVID-19 to launch ransomware attacks, read more: Coronavirus & Ransomware Infection: What’s the Connection?
- Our SSO NAS is the most secure file storage system in the market, read: What makes StoneFly SSO NAS Appliances Ransomware-Proof?
- We can help healthcare organizations become ransomware-proof, read how: How healthtech can be made ransomware-proof with DR365
Connect with us on our social media
To learn more about ransomware and how to protect your infrastructure, connect with us on our social media channels:
Twitter: https://www.twitter.com/stoneflyinc
Facebook: https://www.facebook.com/stoneflyinc
Linkedin: https://www.linkedin.com/company/c/stonefly-networks/
Youtube: https://www.youtube.com/stoneflyinc
![ransomware_attack_worried_businessman_by_andrey_popov_gettyimages-1199291222_cso_2400x1600-100840844-large[1]](https://staging.stonefly.com/wp-content/uploads/2020/10/ransomware_attack_worried_businessman_by_andrey_popov_gettyimages-1199291222_cso_2400x1600-100840844-large1.jpg)









