Hyper-converged infrastructure addresses user storage requirements effectively. Scalability, simplified management and performance needs are commendably met. However, even well-built hyper-converged infrastructures cannot ensure data backup and recovery.
If the hardware fails or a power failure occurs, then there’s a high chance of data loss. Evidently, data loss is unacceptable for organizations as it leads to financial losses and brand prestige damage. In order to effectively leverage IT infrastructures and protect their mission critical workloads, enterprises should integrate Veeam backup and replication.
Veeam delivers high availability for enterprise-level workloads effortlessly. StoneFly offers a number of Veeam solutions to empower enterprise data protection strategies, which include but are not limited to: Veeam Cloud Connect to Azure, Veeam Gateway to Azure, Veeam Backup and Replication for Nutanix and more.
You can learn more about StoneFly’s Veeam offers and innovative cloud products here: Click here to learn more.
Verily, data loss is disastrous for businesses but what causes data loss? Let’s look into some of the major factors that result in data loss and in turn financial losses.
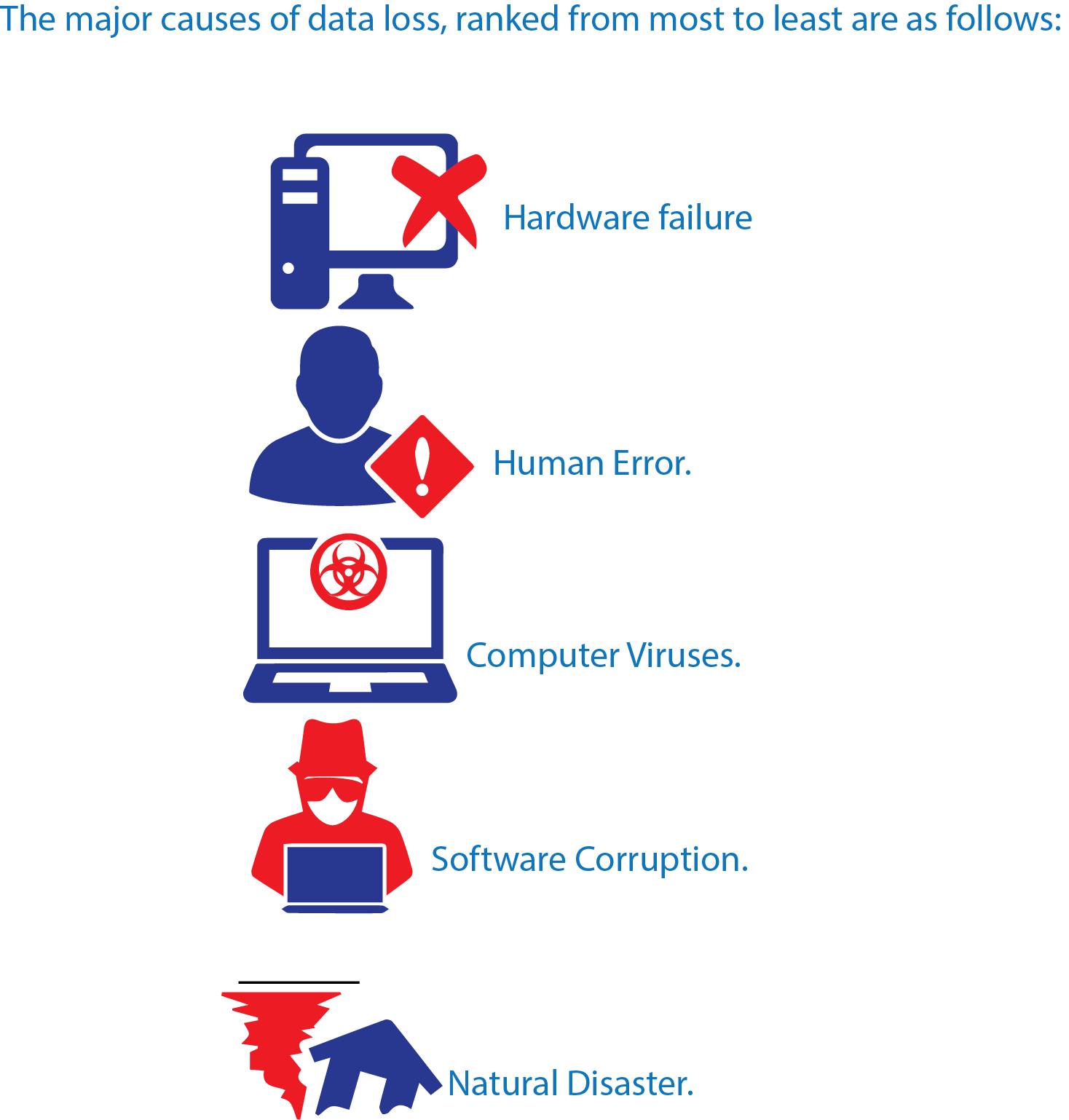
What are the major causes of data loss?
Different surveys and reports, such as the research by Ponemon Institute, point in one direction when it comes to the major cause of data loss: Hardware failure. Other reasons ranked from most to least are as follows:
- Hardware Failure.
- Human Error.
- Software Corruption.
- Computer viruses.
- Natural Disaster
Hardware Failure – Hardware failures include an element failure or an entire appliance failure. Failures like HDD failure, power supply failure, etc. are classified as hardware failures.
Human Error – Human error, the type of error that can only be reduced by proper training but never completely removed, is the second largest cause of data loss. This includes accidental deletion or malicious deletion of data as well.
Software Corruption – Software corruption, despite the industry’s continuous practice to ensure a corruption-free solution, is the third largest reason why businesses experience data loss. Businesses may experience software corruption if their IT teams do not timely update a software. Sometimes a patch or an update can result in software corruption and sometimes it’s a bug or a disruption in the network that leads to it.
Computer viruses – Computer viruses are as old as computers themselves and are a bigger threat than they ever were before. Recently, ransomware have come into the spotlight for successfully attacking and halting the operations of organizations as they locked away their data. In some cases, while Federal agencies strictly forbid it, ransom payment recovered data; however, organizations affected by Wipers like Petya still lost their data.
You can read more about Ransomware here: (Read more about Ransomware and protecting your data from it)
You can also explore Petya in this article: (Protecting yourself from the Global Ransomware Outbreak)
Natural Disaster – As devastating as natural disasters are, they do not amount to much of the data lost globally. This does not mean that businesses in disaster-prone areas do not need to plan ahead for a disaster and procure means of data recovery and disaster recovery. However, this does imply that businesses not in disaster-prone areas cannot assume that there data is completely safe from data loss.
In light of these data loss causes, it is very important for enterprises to setup a reliable backup strategy. The question here is what constitutes a reliable backup strategy?
What constitutes a reliable backup strategy?
A reliable backup strategy ensures seamless recovery of all enterprise data, whenever necessary, using enterprise-level services that are highly available and easily deployable. It is important to setup a backup schedule that ensures minimum RTPOs (Reduced Time and Point Objectives) in accordance to the organization’s requirements.
Manual backup processes take up a lot of time and are prone to errors; therefore, business IT environments should focus on automating the backup process. This can be done easily with the enterprise-level appliance offered by StoneFly that delivers Veeam backup and replication.
StoneFly also offers Veeam for Nutanix environments. IT environments working with on-premises Nutanix environments can setup backup and replication on-premises and they can opt to setup enterprise-level backup in Microsoft Azure cloud.
If we are to summarize the ingredients of a reliable backup strategy, they would look something like this:
- High availability.
- Regular data integrity checks.
- Reduced RTPOs.
- Simplified setup and deployment.
- Elastic payment schedules.
- Geo-redundant copies.
- Enterprise-level data services (Snapshot, geo-replication etc.)
- Data Security using advanced encryption technology (like AES-256).
- Automated backup jobs.
What StoneFly offers to ensure Data Recovery and High Availability for Enterprise Workloads?
StoneFly offers a number of solutions for businesses to easily setup and deploy reliable backup solutions for their enterprise workloads. StoneFly offers
- Backup appliances for businesses looking to setup on-premises enterprises setup.
- Cloud backup for businesses that do not wish to deal with the hardware and carbon footprint.
- Veeam backup and replication for businesses that have their IT environments setup and are to ensure data recovery and high availability. (Solutions include Veeam ready appliances and Veeam cloud connect to Azure, AWS and other public clouds)
- Veeam backup and disaster recovery for Nutanix. (On-premises environments and in the cloud)
StoneFly is partnered with Veeam, Microsoft Azure cloud, Amazon Web Services (AWS). These partnerships enable StoneFly to come up with innovative, customized and purpose-built solutions for enterprise workloads.
StoneFly’s backup solutions are easily deployable and solutions like Veeam cloud connect to Microsoft Azure can be deployed in less than 30 minutes. With StoneFly’s partnership with Microsoft Azure cloud, businesses can setup 6 Geo-redundant copies in a cloud. StoneFly’s products are equipped with innovative backup technologies like snapshot, geo-replication, optional RAID and more to ensure high availability and efficient data recovery of enterprise workloads.
To make sure that enterprise data is well protected, StoneFly uses advanced encryption technology (AES-256 bit encryption) at rest and SSL/TLS tunneling to protect data in transit. StoneFly’s backup technology when paired with Veeam can further reduce RTPOs to less than 15 minutes.
Apart from the range of backup and disaster recovery appliances and solutions, StoneFly also delivers a number of storage solutions:
- Network Attached Storage (NAS) appliances – on-premises and in the cloud.
- Storage Area Network (SAN) appliances – on-premises and in the cloud.
- Hyper-converged appliances – on-premises and in the cloud.
- Gateway appliances.
- WAN accelerator/Optimizer.
- Cloud Business Center (CBC™)
If data loss is a problem, let us solve it for you. Contact us and we’ll listen to your challenges and come up with a purpose-built backup and disaster recovery solution.
![a7530513820951b61405bb14deeea9f3[1]](https://staging.stonefly.com/wp-content/uploads/2018/05/a7530513820951b61405bb14deeea9f31.png)









