Examples of Applying the Azure Stack Region
Microsoft Azure is not going to define those for you but, examples might be, you have two different lines of business, they are going to invest in hardware, but they want to be able to manage essentially who gets access to that hardware and who is going to deploy workload. But you maybe as an administrator really don’t want to run multiple instances of Azure Stack. So they will take one set of hardware and place that in one region, and take a second set of hardware that is purchased by some of the line of business and place that in a second region and run that under single instance of the ARM.
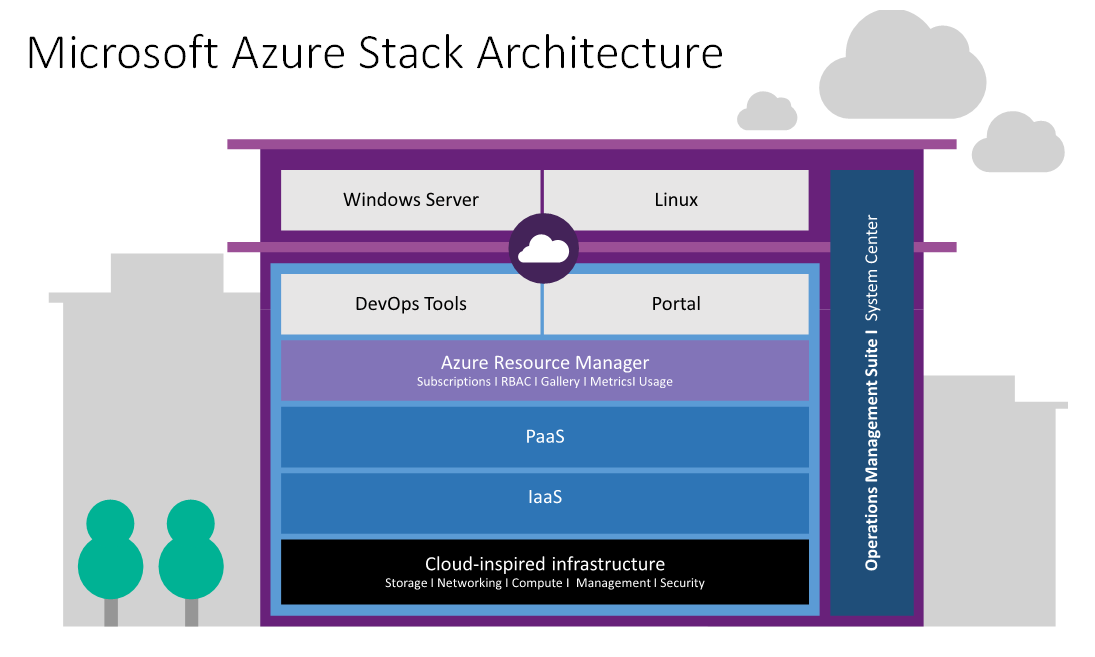
Other Attributes of the Azure Stack Region
You can create plans and offers that essentially users are restricted to, or tenants are restricted to a particular region when they go to do deployments. So you have got that control and alignment with essentially what is an abstract concept to Microsoft Azure Cloud, really isn’t meaningful to Microsoft as a provider of Azure Stack, but you as a customer you can do that alignment.
Other things that are classic examples, are that you have two regions and you are going to place them in two different data centers. You have got an application that is pushing data between them from a data replication stand point for disaster recovery, and you can physically separate those regions by hundreds of feet. If they are different buildings, tens of kilometers if that is what you require for your business. Those are very quick examples of what that is.