
Image Source: www.microsoft.com
The ARM Layer of Azure Stack Cloud
We have the Azure portal and the templates being able to work with PowerShell and the way the overall topology of Azure is managed in Azure Stack. The Azure Resource Manager (ARM) is an instance that runs in Azure Stack. This is the end point that you interact with as both a tenant and administrator of an Azure-Stack-instance – This is key to the overall delivery.
The PR Layer
Underneath the ARM layer is an architectural layer as a partition request broker. We have a number of abbreviations listed underneath that. All of them refer to essentially a resource provider. It is a widely known API that interacts back-and-forth with the ARM.
Azure Cloud’s Infrastructure Control Layer
Then underneath that, we have, essentially the changes that start to occur, because the architecture, nothing like the massive data center, it is going to be 4-servers to start with. So, we have to take the software that runs in that data center in some form and deliver the stability of Azure and bring it onto a four node configuration to begin.
This essentially represents the core pieces where the variance starts to occur from an Azure standpoint. This is all essential detail. This is an infrastructure that Microsoft Azure Cloud is providing and it is not externally-disclosed to you through a set of APIs. You are not going to see that when you go-off to deploy workloads as a tenet or administer for the whole server-solution.
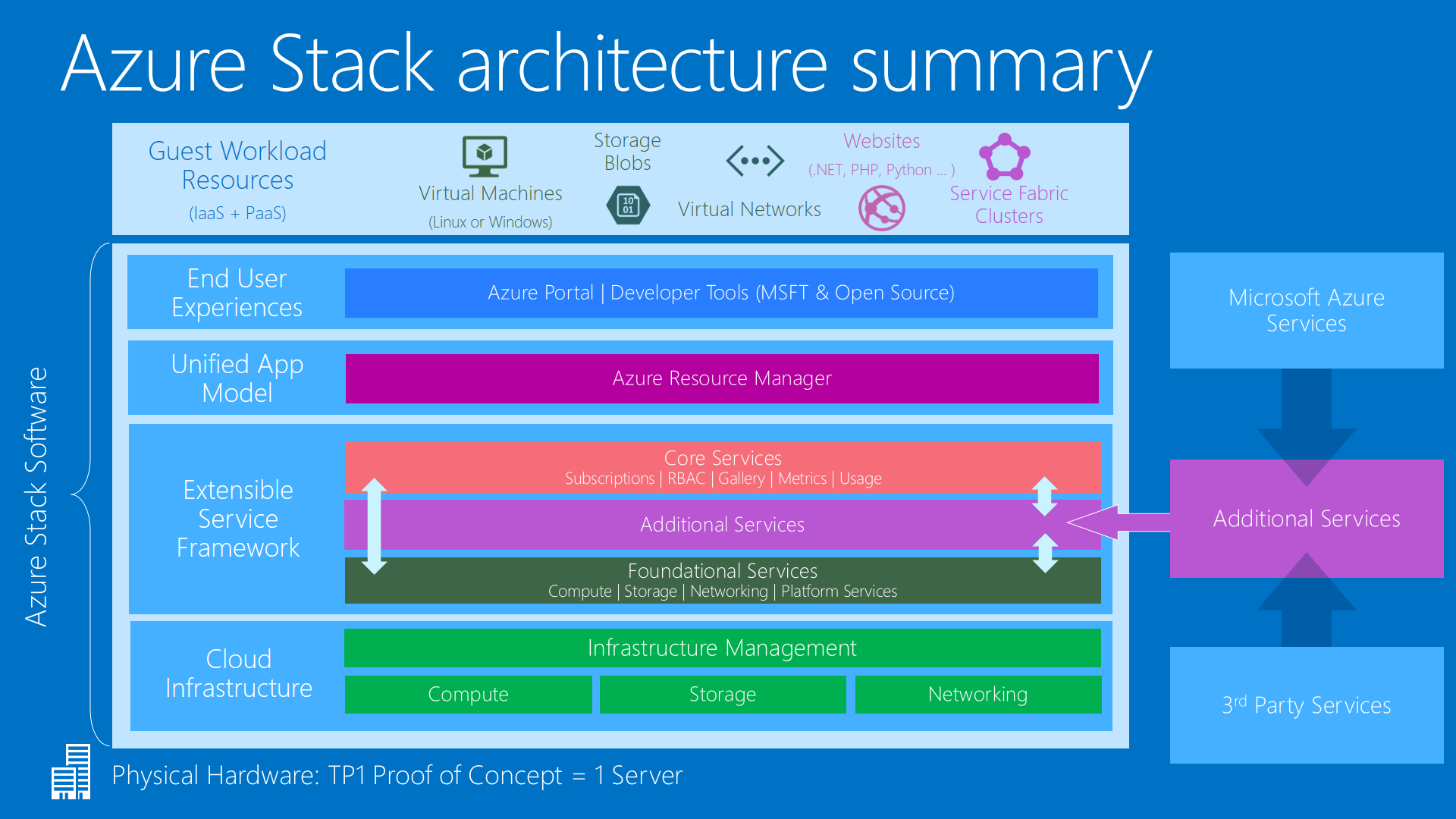
Image Source: www.cio.com










