Mirroring, replication, and clustering are essential data management techniques that play a vital role in ensuring data availability, integrity, and resilience. Businesses require reliable and scalable data management solutions to meet the increasing demands of data-driven operations, ensuring continuous access and protection against failures.
In this blog, we describe how mirroring, replication, and clustering contribute to robust data management strategies, enabling businesses to safeguard their critical data, achieve high availability, and meet the evolving needs of modern data environments. We also provide a comparative analysis of these three techniques, empowering IT administrators to make informed decisions and choose the most suitable approach for their projects.
What is Mirroring?
Mirroring is a data replication technique that involves creating an exact copy of data from one device to another in real-time. It ensures that the replicated data remains synchronized with the source data, providing data redundancy and high availability. Mirroring is commonly used in storage systems and databases to enhance data protection, disaster recovery, and overall system reliability.
How Mirroring Works
Mirroring works by continuously copying data changes from a source device to a target device. The process involves the following key aspects:
- Real-time Data Replication: Mirroring operates in real-time, capturing data modifications as they occur on the source device and immediately applying them to the target device. This ensures that the replicated data is up to date and consistent with the source.
- Source and Target Devices: Mirroring involves two devices: the source device, which holds the original data, and the target device, where the mirrored copy resides. The target device is typically located in a separate physical or logical location to provide data redundancy and protection against localized failures.
- Synchronization and Consistency: Mirroring ensures that the data on the source and target devices remain synchronized. Changes made on the source device are replicated to the target device, ensuring both copies have consistent and identical data. This synchronization process can be achieved through various methods, including block-level or file-level replication.
Types of Mirroring
Mirroring can be implemented using different approaches, including:
- Software-based Mirroring: Software-based mirroring utilizes software applications or operating system features to replicate data between devices. This approach provides flexibility and can be implemented on various storage systems.
- Hardware-based Mirroring: Hardware-based mirroring involves specialized hardware components, such as RAID controllers or storage arrays, which handle the replication process. This approach offloads the mirroring operations from the host system, enhancing performance and scalability.
- Synchronous and Asynchronous Mirroring: Synchronous mirroring ensures that data is replicated in real-time, with each write operation confirmed on both the source and target devices before proceeding. Asynchronous mirroring introduces a delay in the replication process, allowing for greater distance between the source and target devices, but with a potential risk of data loss in case of a failure.
Advantages of Mirroring
Implementing mirroring provides several advantages, including:
- High Availability and Data Redundancy: Mirroring enables continuous access to data even in the event of a device failure. If the source device becomes unavailable, the mirrored copy can seamlessly take over, minimizing downtime and ensuring uninterrupted operations.
- Improved Data Protection and Disaster Recovery: Mirroring creates a redundant copy of data, protecting against data loss due to hardware failures, natural disasters, or human errors. In the event of a disaster or data corruption, the mirrored copy can be readily accessed to restore critical data.
- Reduced Downtime and Business Continuity: With mirrored data, businesses can achieve faster recovery times and minimal downtime. The ability to quickly switch to the mirrored copy allows for uninterrupted operations and ensures business continuity.
Common Applications of Mirroring
Mirroring finds applications in various scenarios, including:
- Database Mirroring: Mirroring is commonly used in database systems to provide high availability and data redundancy. It ensures that critical databases remain accessible even if the primary database server experiences issues.
- Disk Mirroring: Disk mirroring, also known as RAID 1, involves mirroring data across multiple disks in a storage system. It improves data reliability and protects against disk failures.
- Storage Area Network (SAN) Mirroring: SAN mirroring involves replicating data between geographically separated storage arrays in a SAN environment. It enhances data protection and disaster recovery capabilities.
What is Replication?
Replication is a data synchronization process that involves creating and maintaining multiple copies of data across different devices or systems. It ensures that data remains consistent and up to date across all replicated copies, allowing for improved data availability, distribution, and disaster recovery.
How Replication Works
Replication typically involves the following key components and steps:
- Source and Target Systems: Replication involves a source system, which holds the original data, and one or more target systems, where the replicated copies reside. The source system is responsible for initiating and propagating data changes to the target systems.
- Data Capture: Replication captures data changes made on the source system, including inserts, updates, and deletes. It records these modifications in a transaction log or similar mechanism.
- Data Transformation: The captured data changes are transformed into a format suitable for replication and transmission. This may involve converting data formats, compressing data, or applying specific rules or filters.
- Data Transmission: The transformed data changes are transmitted from the source system to the target systems over a network. This can be done using various replication methods, such as log-based replication, snapshot replication, or merge replication.
- Data Application: Upon receiving the replicated data changes, the target systems apply them to their respective copies of the data. This ensures that all replicated copies remain consistent and synchronized with the source data.
Types of Replication
There are different types of replication methods, each offering specific features and benefits:
- Snapshot Replication: Snapshot replication involves creating periodic snapshots of the entire source dataset and distributing them to the target systems. It provides a point-in-time copy of the data and is suitable for scenarios where near real-time data synchronization is not required.
- Transactional Replication: Transactional replication focuses on capturing and replicating individual data transactions, such as inserts, updates, and deletes. It ensures that the target systems receive and apply the exact same data modifications as they occur on the source system, maintaining data consistency and accuracy.
- Merge Replication: Merge replication allows multiple systems to independently modify data and later reconcile the changes. It is useful in scenarios where multiple sources need to merge their changes into a central system, such as branch offices replicating data to a central database.
Advantages of Replication
Implementing replication offers several advantages, including:
- Improved Data Availability: Replication ensures that data is available on multiple systems, reducing the risk of data loss or unavailability in case of system failures or network interruptions.
- Enhanced Scalability and Performance: By distributing data across multiple systems, replication can improve system performance by distributing read and write operations, reducing bottlenecks, and enhancing scalability.
- Data Distribution and Localization: Replication allows data to be distributed to different locations or systems, enabling localized access and reducing network latency for users or applications in specific regions.
- Disaster Recovery and Business Continuity: Replication plays a crucial role in disaster recovery strategies by providing redundant copies of data. In the event of a system failure or disaster, the replicated data can be used for recovery and ensuring business continuity.
Common Applications of Replication
Replication is employed in various scenarios, including:
- Database Replication: Database replication ensures that multiple database copies remain synchronized, providing high availability, load balancing, and data distribution for applications.
- Content Delivery Networks (CDNs): CDNs use replication to distribute website content across geographically dispersed servers, improving website performance and reducing latency for end-users.
- File and File System Replication: Replicating files and file systems enables data sharing, backup, and disaster recovery across different systems or locations.
By implementing replication, organizations can achieve data redundancy, availability, and synchronization, enhancing their overall data management and protection capabilities.
What is Clustering?
Clustering is a method used to create a group of interconnected servers or computing resources that work together as a single system. It enables high availability, fault tolerance, and scalability by distributing workloads across multiple nodes within the cluster.
Benefits of Clustering
Clustering offers several benefits for businesses:
- High Availability: Clustering ensures continuous availability of applications and services even if individual nodes or servers fail. If one node becomes unavailable, the workload is automatically shifted to another node within the cluster, minimizing downtime.
- Fault Tolerance: By distributing workloads across multiple nodes, clustering provides fault tolerance. If one node experiences hardware or software issues, the workload is automatically redirected to other nodes, ensuring uninterrupted operation.
- Scalability: Clustering allows organizations to scale their computing resources by adding more nodes to the cluster. This enables efficient handling of increased workloads and improved performance as demand grows.
- Load Balancing: Clustering evenly distributes incoming requests and workloads across multiple nodes, preventing any single node from becoming overloaded. This ensures optimal resource utilization and improved response times.
Types of Clustering
There are different types of clustering methods commonly used:
- High Availability (HA) Clustering: HA clustering focuses on providing continuous availability by monitoring the health and status of each node. If a node fails, the workload is automatically shifted to another available node, ensuring uninterrupted operation.
- Load Balancing Clustering: Load balancing clustering evenly distributes workloads across multiple nodes to optimize resource utilization and enhance performance. It ensures that no single node is overwhelmed with excessive requests or tasks.
- Failover Clustering: Failover clustering is designed to provide automatic failover in case of node failures. If a node becomes unresponsive or fails, the workload is automatically transferred to another node, maintaining service availability.
- Shared-Nothing Clustering: Shared-nothing clustering involves distributing data and processing across multiple nodes without the need for shared storage or a central database. Each node operates independently, enhancing scalability and performance.
Key Components of a Cluster
A cluster typically consists of the following components:
- Nodes or Servers: Nodes are the individual servers or computing resources within the cluster. These nodes work together to provide the desired functionality and services.
- Cluster Manager: The cluster manager oversees the overall operation of the cluster, monitoring the status of nodes, managing failover, load balancing, and other cluster-related activities.
- Heartbeat Mechanism: The heartbeat mechanism is a communication method used by nodes to monitor the status of each other. It enables nodes to detect failures and trigger appropriate actions.
- Shared Storage: In some clustering configurations, shared storage is used to ensure data consistency and availability across multiple nodes. Shared storage allows any node to access and work with the same data.
Applications of Clustering
Clustering is widely used in various domains, including:
- Web Servers and Applications: Clustering is employed to enhance the availability, scalability, and performance of web servers and applications by distributing workloads across multiple nodes.
- Database Systems: Clustering database systems allows for high availability, load balancing, and fault tolerance, ensuring uninterrupted access to critical data.
- High-Performance Computing (HPC): Clustering is extensively used in HPC environments to leverage the combined power of multiple nodes for computationally intensive tasks.
- Virtualization: Clustering is used in virtualization platforms to ensure high availability and efficient resource utilization across a cluster of virtual machines.
Comparing Mirroring vs Replication vs Clustering
Mirroring, replication, and clustering are all techniques used to ensure data availability, fault tolerance, and high performance. However, they differ in their approach and application. Let’s compare these three methods:
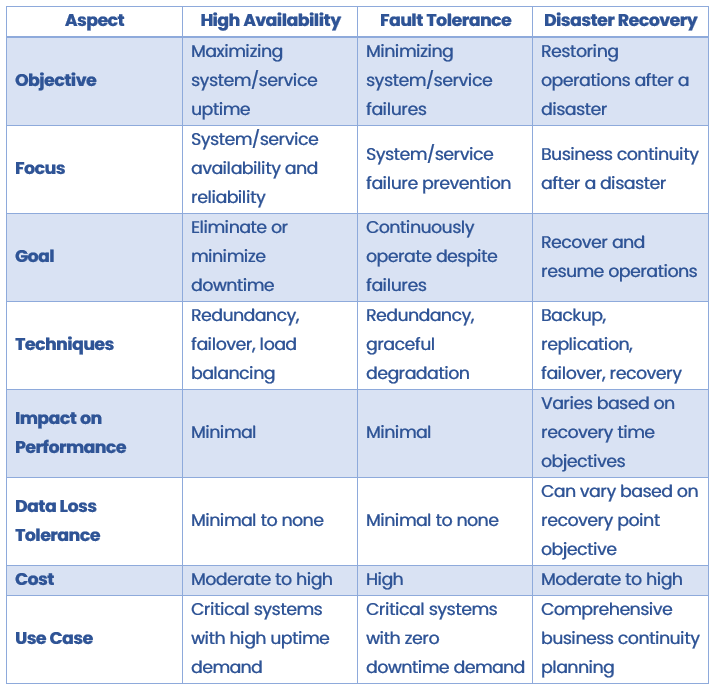
Table Legend:
- Data Redundancy: Indicates whether the method creates redundant copies of data.
- Data Consistency: Specifies the level of consistency between the primary and replicated data.
- Failover Capability: Describes the method’s ability to handle failures and switch to a backup system.
- Scalability: Indicates the method’s ability to handle increased workloads or accommodate growing data needs.
- Read Operations: Specifies whether the method allows read operations on replicated or mirrored data.
- Write Operations: Indicates whether the method supports write operations on replicated or mirrored data.
Summary
In conclusion, mirroring, replication, and clustering are distinct data protection and availability techniques. Mirroring ensures real-time synchronization and immediate failover, replication enables data distribution and scalability, while clustering enhances performance and fault tolerance.
Each approach has its strengths and considerations, allowing organizations to choose based on their specific requirements. By understanding these differences, you can make informed decisions to safeguard your data and optimize infrastructure.
Ready to protect your data with mirroring, replication, or clustering? Get in touch!