
CJIS policy is developed by the Advisory policy Board which is representation from the association of several organizations that has people representing different states and this policy is enforced by the FBI CJIS division and CJIS assistance agencies in the state.
This Board is made up of representation from Federal government state agencies and Local agencies. Each state has the systems officer and he is the one responsible for ensuring all law in the state and then there is security politician security officer which is responsible for the technical requirements.
First CJIS Contract for the Cloud Storage
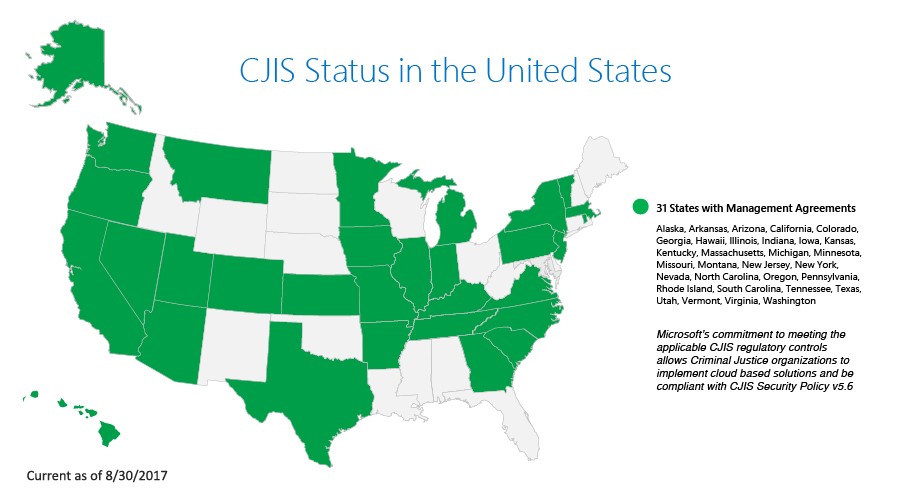
In an effort to support California Law enforcement agencies with the FBI’s requirements for secure cloud storage of (CJIS), Amazon Web services (AWS) signed the Criminal justice Information Service Security Addendum with state department to run CJIS workloads in the AWS cloud. This agreement secures the criminal justice data within the cloud Storage. After signing this agreement all the Law enforcement and government agencies will use cloud services for storing, transmitting and processing CJI data. StoneFly provides the Cloud Connect to Amazon AWS Cloud. This is the first Contract of AWS with California State and after that multiple contracts have been made with other states too. Currently these are the states for the CJIS and Cloud Storage agreements
Criminal Justice Information Services stores and maintains the FBI’s vast amount of crime information data and services. It is kind of a home for the most important data sources of law enforcement across the U.S., including the National Crime Information center which is a 24-hour crime information clearinghouse that informs police officers for the warrants and criminal histories.
The following Information is identifiable as Criminal justice information:
- Biometric Identification Information
- Background Check Information
- Registry and Host information available to criminal intelligence analysts
- House National Finger Prints Information
- Audio and Videos of the Crime committed
- Audio and Video Recording of Personal Identifiable information (PII)
CJI also has the the automated finger print identification system and the automated finger print identification system.
Why CJIS is important?
With the Help of Law enforcement-based data sharing there is no risk of data leakage but the point which should be kept in mind is that this pool of information is shared with all the available officers. Several authorities have experienced a Ransomware attacks but fortunately they were all unsuccessful attempts.
Criminals have interest in Law enforcement Data, In case they get access in police database, they can alter criminal records, gather personal information, distracting police and gaining the complete knowledge based advantage over the criminal enterprises.
Cloud storage requirement for CJIS Compliance
For CJIS compliance data security is the top priority. The data center where the data needs to be stored should be secured and encrypted both in storage and transmission. CJI should never be data-mined or read by the cloud provider. CJI should also be separated physically and logically from other data to prevent unauthorized Access.
Another requirement from the cloud storage provider is that they should retain 99.9% of uptime because of the importance of the information and services.









