What is the SOC Framework?
With businesses outsourcing basic functions like data storage, access and data backup to Cloud Service Providers (CSPs) and other service organizations the American Institute of Certified Public Accountants (AICPA) has developed a Service Organization Controls (SOC) framework.
The framework serves as a standard for controls that safeguard the confidentiality and privacy of information stored and processed by a CSP (like Microsoft Azure cloud, Amazon Web Services etc.). This aligns with the International Standard on Assurance Engagements (ISAE): the reporting standards for international organizations.
You can learn more about the SOC standard here.
While the audit reports contain a comprehensive description and analysis of Azure cloud’s services, this article will shed light on the Azure environment setup to secure cloud backups; using information extracted from the SOC 2 report, type 2 (01-04-2017 to 31-03-2018).
Let’s first identify some variables associated with data backups before we talk about the Azure environment.
How Microsoft identifies and uses data?
Data flowing through Microsoft Azure cloud can be distributed into two basic types: data that customers upload to the Azure cloud storage and the data that’s generated on the customer’s behalf to enable the usage of cloud services.
Microsoft only uses customer data in order to support the provisioning of their services subscribed to, by the customers in accordance with the Service License Agreements (SLAs). The customer data are broadly classified into the following data types:
- Customer data: This is data, information, or content that Azure’s customers (including their end-users) store or process within Azure through the use of Azure cloud services. This customer data may include images, text, code or software provided by the customer or on the customer’s behalf.
- End-user Identifiable Information (EII): This is information about end users of services hosted in Azure cloud that may be visible to Microsoft. For instance end-user Internet Protocol (IP) addresses.
- Access Control Data: This is data used to manage access to other types of data or functions within Azure.
- Account Data (Administrator Data): This is information about administrators including contact information that is needed to provide the agreed upon service.
- Account Data (Payment Information): This is information about payment instruments; this type of data is not stored in the Azure platform.
- Organization Identifiable Information (OII): This is system metadata (configuration, usage, events) when tied to organizations, that own the account or subscription, can be seen as sensitive if used outside of the Azure production environment. This is particularly meaningful to services used by Office 365 and similar SaaS (Software as a Service) services, so is called out as a separate sub-category for more secure handling.
- System Metadata: This is configuration, usage and event data, that does not have customer data or any other category of data described above.

Who owns the applications and data deployed in Microsoft Azure Cloud?
According to the SOC 2 type 2 report, Microsoft does not inspect, approve, or monitor applications that customers deploy to Azure cloud. More ever, Microsoft does not know what kind of data customers choose to store in Microsoft Azure storage. Microsoft does not claim data ownership over the content information entered into Azure cloud.
Azure’s agreement states: “Customers are solely responsible for the content of all Customer Data. Customers will secure and maintain all rights in Customer Data necessary for Azure to provide the Online Services to them without violating the rights of any third party or otherwise obligating Microsoft to them or to any third party. Microsoft does not and will not assume any obligations with respect to Customer Data or to their use of the product other than as expressly set forth in the Agreement or as required by applicable law.”
One of the mainstream doubts about the cloud is “who owns the data when it’s deployed in the cloud based service?” These extracts from the SOC 2 report and Azure’s agreement are meant to clear up those doubts.
What is the Microsoft Azure cloud environment?
Azure is a cloud platform based on machine virtualization; it is developed and managed by the Azure team. This means that customer code – whether it’s deployed in a PaaS (Platform as a Service) worker role or an IaaS (Infrastructure as a Service) Virtual machine – executes in a windows server hyper-v virtual machine. Every physical node in Azure has one or more virtual machines, also called instances, that are scheduled on physical CPU cores, are assigned dedicated RAM, and have controlled access to local disk and network I/O.
A hypervisor runs directly over the hardware; it divides a node into each node into a variable number of Guest VMs (Virtual Machines). Each node also has one special Root VM, which runs the Host OS, as illustrated in the figure below. Fibre Agents (FAs) on Root VMs are used to manage Guest Agents (Gas) within Guest VMs. Isolation of the Root VM from the Guest VMs and the Guest VMs from one another is a key concept in Azure cloud security architecture.
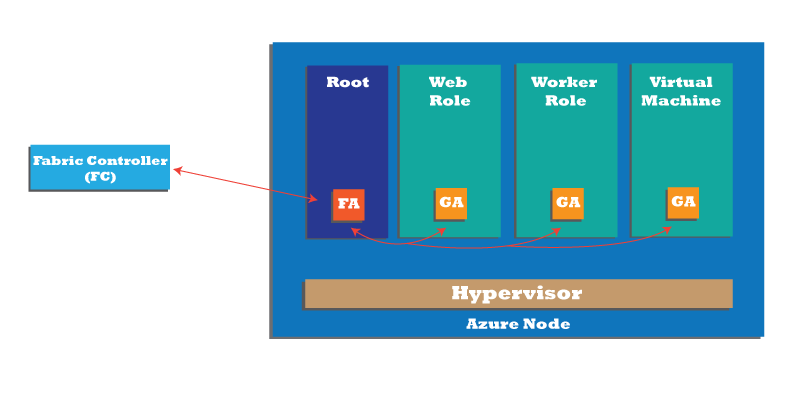
What Microsoft does to secure Customer applications and data in the Azure cloud?
In order to ensure data security, Azure has established an Information Security Program that provides documented management direction and support for implementing information security within the Azure environment. The design and implementation of applicable controls are defined based the type of Azure service and its architecture.
The objective of the Information Security Program is to maintain the Confidentiality, Integrity, and Availability (CIA) of information while complying with applicable legislative, regulatory, and contractual requirements.
The Information Security Program consists of the following components:
- Policy, Standards and Procedures
- Risk Assessment
- Training and Awareness
- Security Implementation
- Review and Compliance
- Management Reporting
- Access Control
- Anti-Malware
- Asset Management
- Baseline Configuration
- Business Continuity and Disaster Recovery
- Capacity Management
- Cryptographic Controls
- Datacenter Operations
- Document and Record Management
- Exception Process
- Hardware Change and Release Management
- Incident Management
- Legal and Regulatory Compliance
- Logging and Monitoring
- Penetration Testing
- Network Security
- Personnel Screening
- Privacy
- Risk Management
- Secure Development Lifecycle
- Security Assessment and Authorization
- Third Party Management
- Training and Awareness
- Vulnerability Scanning and Patch management
What is Microsoft’s Security Policy?
Microsoft Security Policy (MSP) outlines high level objectives related to information security, defines risk management requirements and information security roles and responsibilities. The Security Policy contains rules and requirements that are met by Azure and other online services staff in the delivery and operations of the Online Services environment. The security policy is derived from the ISO / IEC 27001:2013 standard and is augmented to address relevant regulatory and industry requirements for the Online Service environment.
The policy is renewed and updated, as necessary, at least annually, or more frequently, in case of a significant security event, or upon significant changes to the service or business model, legal requirements, organization or platform.
Each management-endorsed version of the MSP and all subsequent updates are distributed to all relevant stakeholders from the Microsoft intranet site.
StoneFly’s Azure Integrated Products and Services
StoneFly delivers enterprise level storage, backup and disaster recovery solutions. StoneFly’s scale-out NAS storage appliances deliver Cloud Connect to Microsoft Azure. Enterprises can leverage StoneFly’s storage solutions to extend their storage from on-premises to Microsoft Azure storage. The same applies to StoneFly’s SAN appliances, backup appliances and disaster recovery appliances.
Other than StoneFly’s physical appliances, StoneFly also offers an innovative Software Defined Storage solution: SCVM™ – Storage Concentrator Virtual Machine. The software solution enables legacy infrastructures to connect to Microsoft Azure storage by acting as a gateway appliance. The software also facilitates efficient management, monitoring and deployment of storage resources.
To explore StoneFly’s innovative products, schedule a demo.
Or you could give us a call; we’d love to hear from you: (051) 265 1616. You can also send us an email at sales@staging.stonefly.com










