Day-to-Day Monitoring and Diagnostics with Azure Stack
If you are going to take on a large-system, you have to understand what’s going on. You have to be able to understand what’s happening, what do you need to react to? How do you put together in your existing-environment and how do you incorporate that into the stuff you do from day-to-day?
Azure Cloud Solutions for Business Continuity
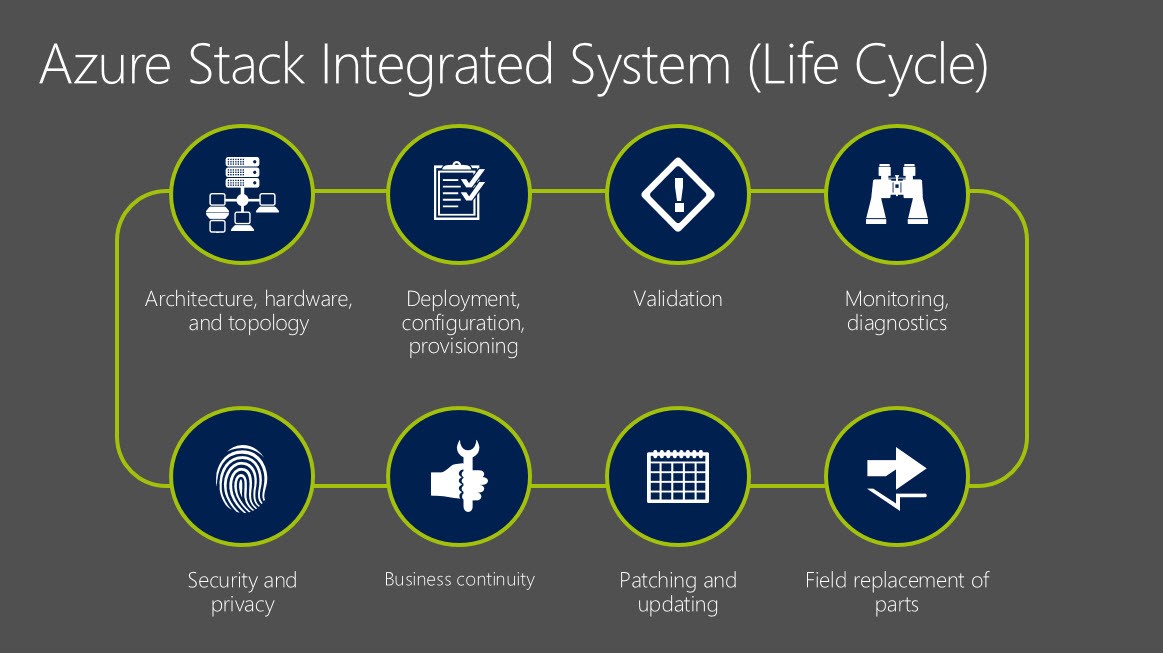
Things like how disaster recovery and backup are integrated to the solution. It’s another large piece of what Azure Cloud Storage services looks through from day-to-day.
Field Replacement of Parts
Field replacement parts for FRUs, obviously, things are going to fail. Both Hardware and software, and we want to be able to cater for that. As a partnership, Azure has certain idea and capability in its software stack. OEM partners have their own supply-chains and support infrastructure, bringing those together in a way that it can actually provide that and make sure that it fulfills the overall SLAs for the solution.
Patching and Updating
Azure delivers software on a regular cadence, so that they can keep up with delivering the consistency with providing services and security, security patches and firmware updates. Essentially, the whole set of things that we have to take advantage of and doing that in a way that’s non-disruptive to the workloads that are running on top of Azure stack.
Microsoft Spends $1 billion a Year on Security for its Products Including Microsoft’s Azure Cloud
And then finally, the security practices. How it does deploy? How it manages the security and privacy and bring it together for you and your environment and making sure it meets the requirements of the Enterprise, service-delivery-partners and a variety of other entities that have to be involved with insuring that we have a secure platform to work from.
This is the whole life cycle or the way we think of the life cycle structure for Azure Stack Integrated System.
Rest of the Azure stack integrated System’s life cycle elements are reviewed here.










