Ensuring data integrity and protection is crucial in a data-driven landscape. Organizations face an ever-growing threat of cyberattacks, data breaches, and unauthorized alterations that can compromise the accuracy and credibility of their data. Immutable File-Level WORM with FileLock offers a reliable defense mechanism against such risks by guaranteeing that once data is written, it cannot be altered, overwritten, or deleted, providing an added layer of security and safeguarding critical information from accidental or malicious changes.
This blog will guide you through the step-by-step process of implementing Immutable File-Level WORM with FileLock to fortify your data storage environment and maintain data integrity with ease.
What is Immutable File-Level WORM (FileLock)?
Immutable File-Level WORM, commonly known as Write Once Read Many with FileLock, is a data protection mechanism that ensures the integrity and security of critical information. In this approach, data files are written once and become read-only, preventing any further modifications or deletions for a set retention period.
This unique feature allows organizations to maintain a tamper-proof record of their valuable data, making it ideal for scenarios where data immutability is paramount, such as ransomware protection, regulatory compliance, data archiving, legal evidence, and secure backup repositories.
Benefits of Immutable File-Level WORM
Data Protection against Accidental or Malicious Alterations:
Immutable File-Level WORM provides a powerful safeguard against unauthorized changes to critical data. By allowing files to be written once and read many times, it ensures that once information is stored, it cannot be altered or deleted. This prevents accidental data modifications as well as malicious attempts to tamper with files, preserving data integrity and maintaining the authenticity of stored information.
Ensuring Regulatory Compliance and Data Retention Policies:
In today’s data-driven landscape, organizations face strict regulatory requirements and data retention policies. Immutable File-Level WORM is an invaluable tool for meeting such compliance standards. By guaranteeing that data remains unaltered and unmodifiable over time, businesses can confidently adhere to legal and industry-specific regulations, ensuring data integrity and authenticity for audits and reporting purposes.
Mitigating the Risk of Ransomware and Cyber-Attacks:
Cyber threats like ransomware attacks pose significant risks to organizations’ data and operations. Immutable File-Level WORM acts as a critical defense mechanism against such threats. As ransomware attempts to encrypt or delete data, this technology ensures that the targeted files are immutable, making them impervious to encryption or unauthorized alteration. By rendering data “write once, read many,” organizations can mitigate the impact of ransomware and protect their valuable information from malicious actors.
Implementing Immutable File-Level WORM empowers organizations with unparalleled data protection, regulatory compliance adherence, and resilience against cyber threats. By safeguarding data integrity and maintaining an unchangeable data state, businesses can confidently focus on their operations and innovation without fear of data compromise.
How to Enable Immutable File-Level WORM
Before you can setup immutable file-level WORM (FileLock), you will need the StoneFusion™ for Baremetal or Storage Concentrator Virtual Machine (SCVM™) installed on VMware, Hyper-V, KVM, Citrix (XenServer), or StoneFly Persepolis.
To setup immutable file-level WORM, you have two options:
- Enable File-Level WORM for an Existing Volume
- Create a new file-level volume and enable file-level WORM (FileLock)
To create a NAS volume, start by creating a NAS segment. Navigate to “NAS,” then “Volumes,” “Segments,” and click “Segment Create.”
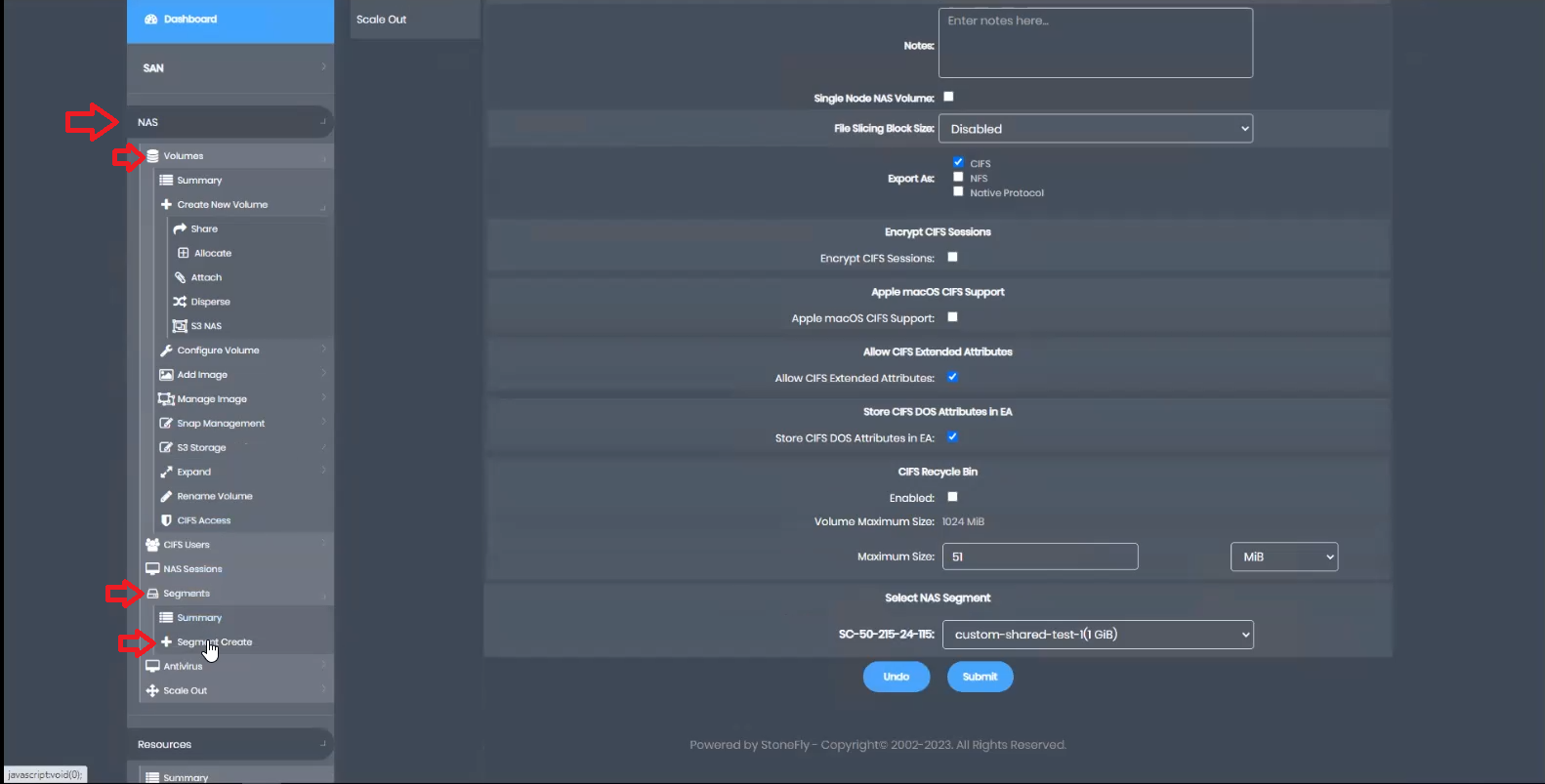
Input the name, choose encryption preferences, allocate the size, and submit to create the NAS segment.
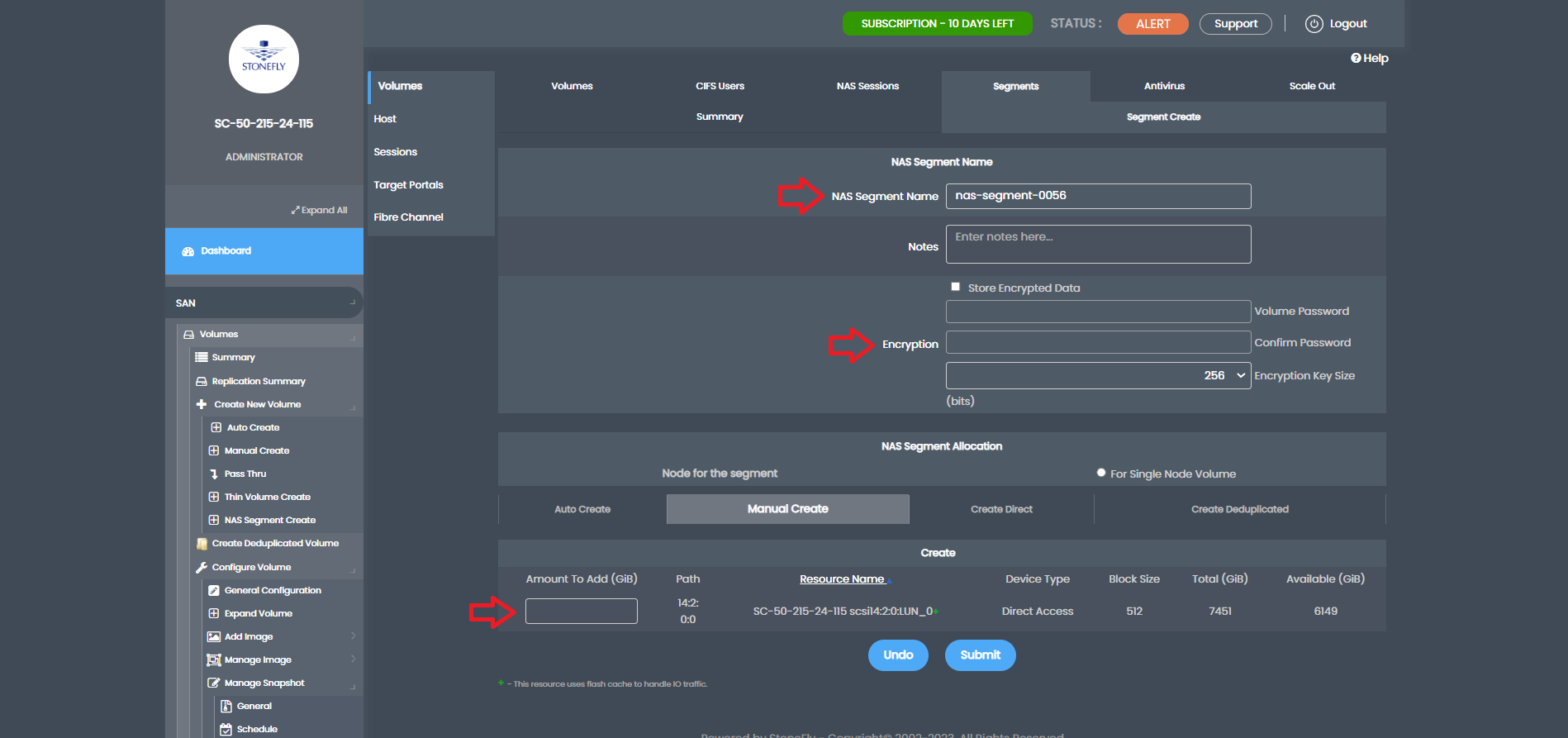
Next, create the NAS volume by going to “NAS,” “Volumes,” and click “Create New Volume.”
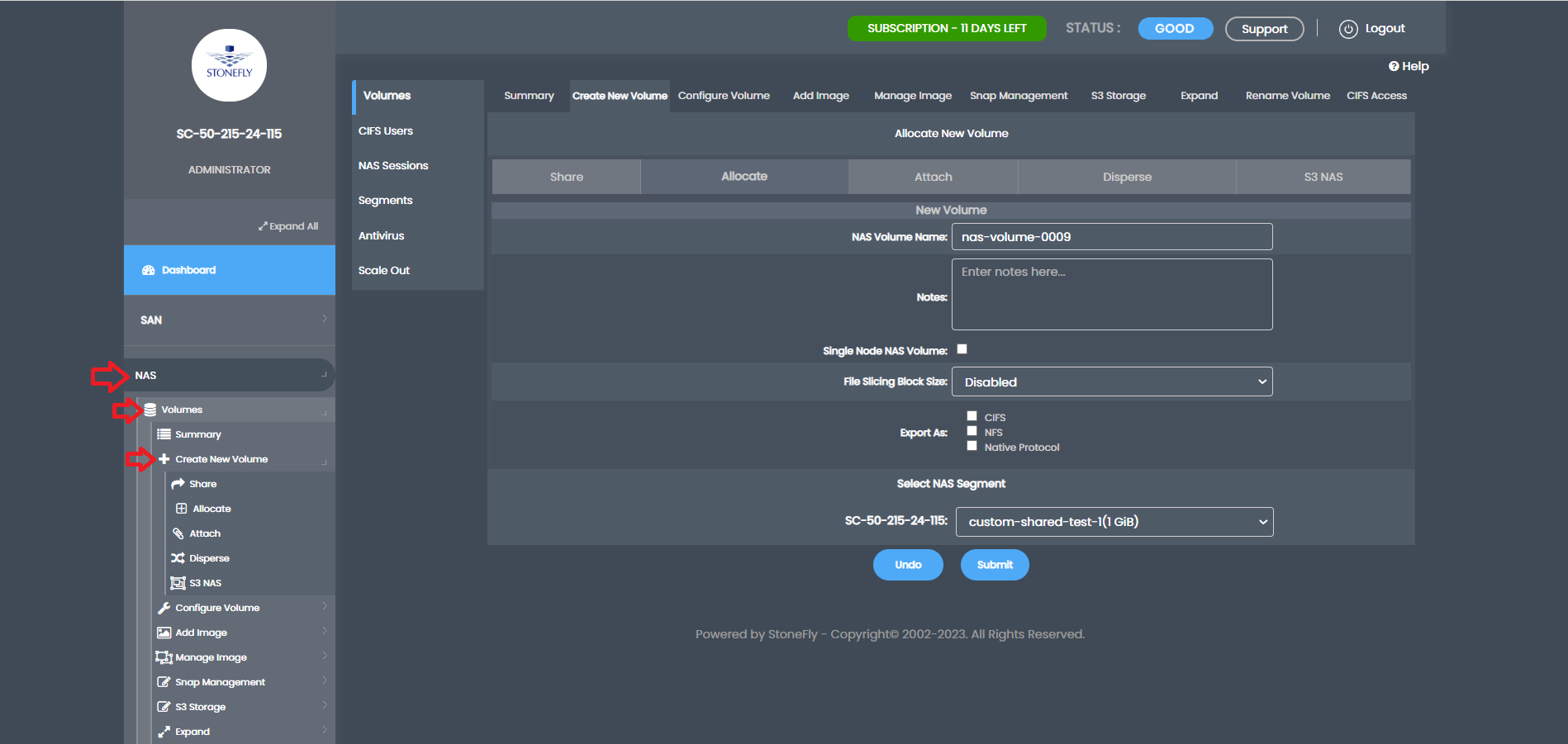
Name the NAS volume, choose CIFS/NFS export, select the newly created NAS segment, and submit to create the NAS volume.
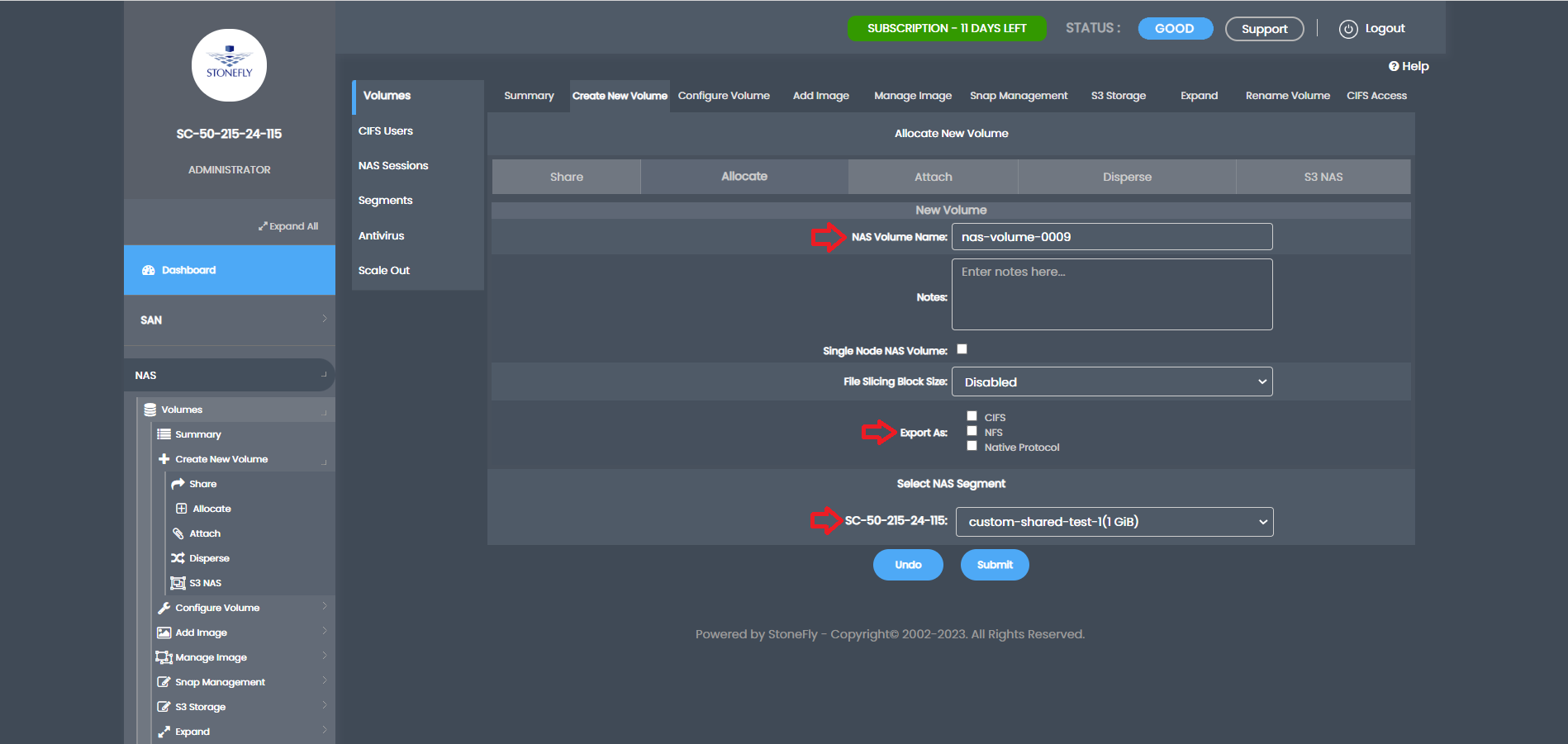
With the NAS volume set up, proceed to enable immutable file-level WORM (FileLock). Go to “NAS,” “Volumes,” and click “Summary” to see the list of NAS volumes.
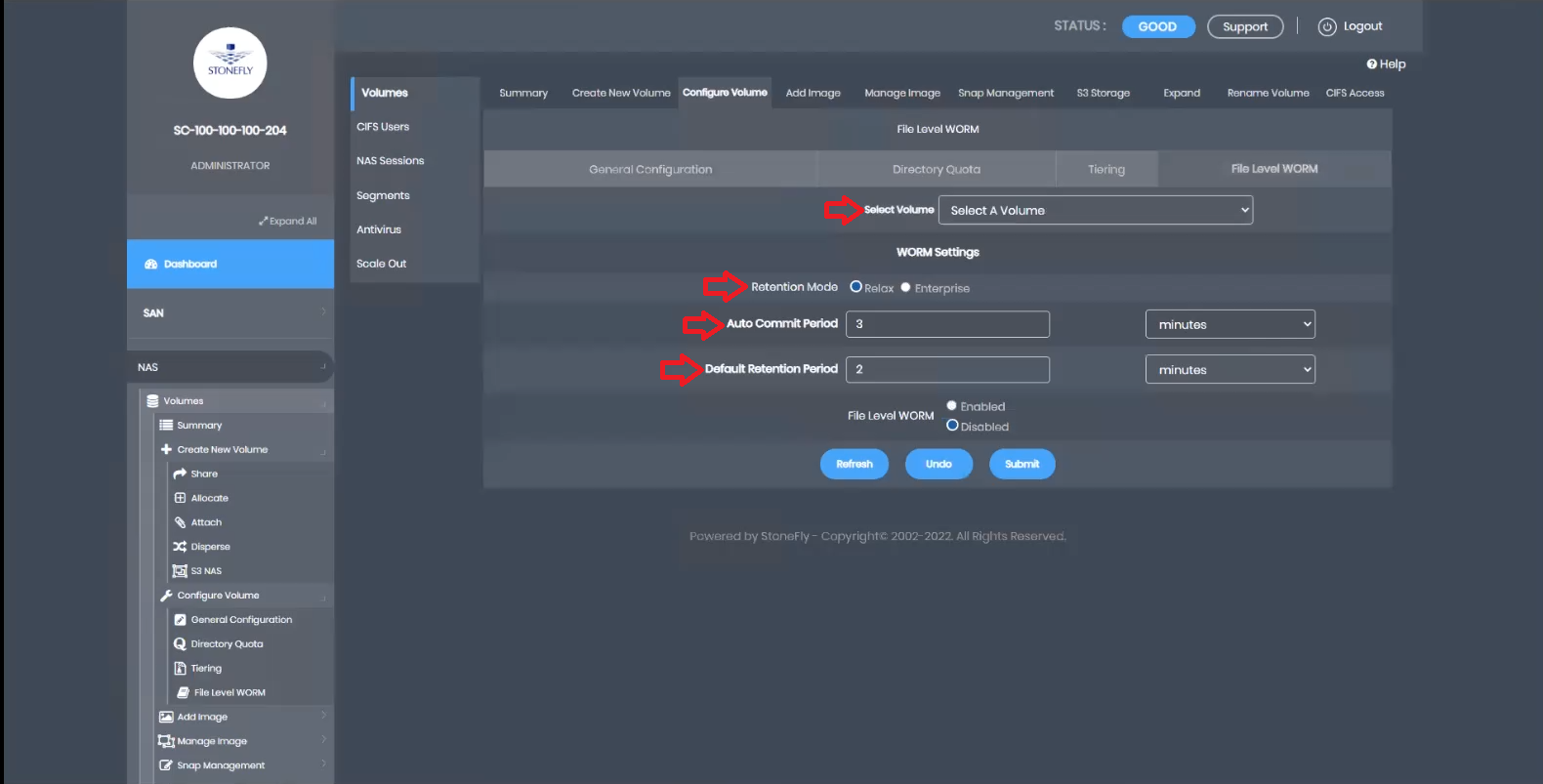
Select the newly created NAS volume from the drop-down menu.
Choose a retention mode: Relaxed or Enterprise. Relaxed allows flexible retention span adjustments, while Enterprise only allows extension of retention span. Set the auto-commit interval to determine the frequency of verifying and committing changes. Specify the retention period for data immutability.
After entering these values, click “Enabled” for File-Level WORM and then “Submit.” This action applies the settings, making the newly created NAS volume an immutable file-level WORM repository with FileLock.
Best Practices for Implementing Immutable File-Level WORM
Air-gapping for Enhanced Data Isolation
Air-gapping is a valuable practice to further enhance the security and isolation of data protected by Immutable File-Level WORM. By physically disconnecting the storage system containing immutable data from the network, you create an “air gap” that prevents any direct access to the protected data. This isolation adds an extra layer of defense against cyber threats like ransomware and unauthorized modifications. In case of a security breach or cyber-attack, the air-gapped storage ensures that the protected data remains untouchable, safeguarding critical information from malicious actors.
StoneFly is the only vendor in the market that offers immutable and air-gapped file, and S3 object repositories in storage, hyperconverged, backup and disaster recovery (DR) appliances, and cloud.
Leveraging Volume Deletion Protection for Additional Resilience
Combining Immutable File-Level WORM with volume deletion protection provides an additional level of resilience to data storage. Volume deletion protection, is a unique StoneFly feature, that prevents accidental or intentional deletions of critical data volumes, ensuring that the Immutable File-Level WORM repositories remain intact and unaltered.
By employing this protective measure, organizations can defend against data loss, unauthorized access, and potential security breaches. Volume deletion protection serves as a critical feature in data storage systems, fortifying data protection strategies and minimizing the risk of data tampering or deletion.
Data Classification and Identifying Suitable Data for Immutable File-Level WORM Protection
To ensure effective implementation of Immutable File-Level WORM (Write Once Read Many) protection, it is crucial to start with data classification. Understand the nature of your data and identify which datasets require stringent data integrity and tamper-proof attributes. Consider data that involves critical records, compliance-related information, financial data, legal documents, or any sensitive data that should remain unaltered and protected against unauthorized changes.
Regular Audits and Monitoring of Data Integrity
Immutable File-Level WORM relies on the concept of data immutability, where data once written cannot be modified or deleted. To maintain the integrity and security of the protected data, regular audits and monitoring are essential.
Periodically assess and review the data repositories protected by File-Level WORM. Ensure that all files remain immutable and verify that no unauthorized modifications or deletions have occurred. Implement a robust monitoring system to promptly detect any suspicious activities and take immediate action in case of potential security threats.
Data Replication and Disaster Recovery Considerations
While Immutable File-Level WORM provides a reliable data protection mechanism, it is essential to consider data replication and disaster recovery strategies. Redundancy and data backups are vital components of a comprehensive data protection plan. Implement data replication to safeguard against hardware failures or unexpected outages, ensuring data availability even in challenging scenarios. Additionally, incorporate disaster recovery mechanisms to swiftly recover data in case of catastrophic events, such as ransomware attacks or natural disasters. Combining Immutable File-Level WORM robust replication and disaster recovery strategies provides a resilient data protection framework for modern data storage environments.
By adhering to these best practices, organizations can maximize the benefits of Immutable File-Level WORM and establish a secure and tamper-proof data management infrastructure, safeguarding their critical data assets against threats and ensuring data integrity.
Conclusion
Incorporating Immutable File-Level WORM (FileLock) into your data storage strategy ensures unparalleled data integrity and protection. With the ability to safeguard against alterations, maintain regulatory compliance, and mitigate the risk of cyber-attacks, FileLock empowers organizations to secure their critical data.
Contact StoneFly today to implement FileLock and protect your unstructured data with enhanced resilience.










