This article is one of two parts to facilitate a step by step explanation of how to setup Veeam Cloud Connect for the enterprise virtual machine in Microsoft azure portal.
This article will cover how you can find Veeam Cloud Connect services in the Azure portal, how you can create a Virtual Machine (VM), choose its size, configure it and then purchase it. The settings of the VM will be described in the second part of the article that will follow later.
Azure Portal & Veeam Cloud Connect Services
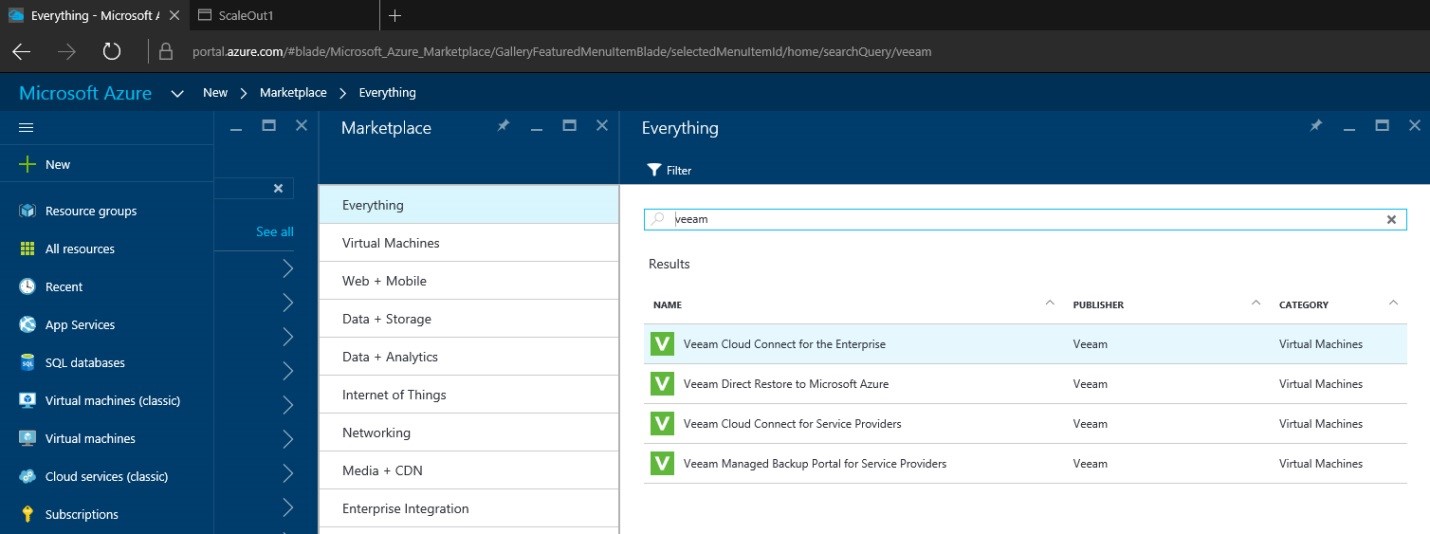
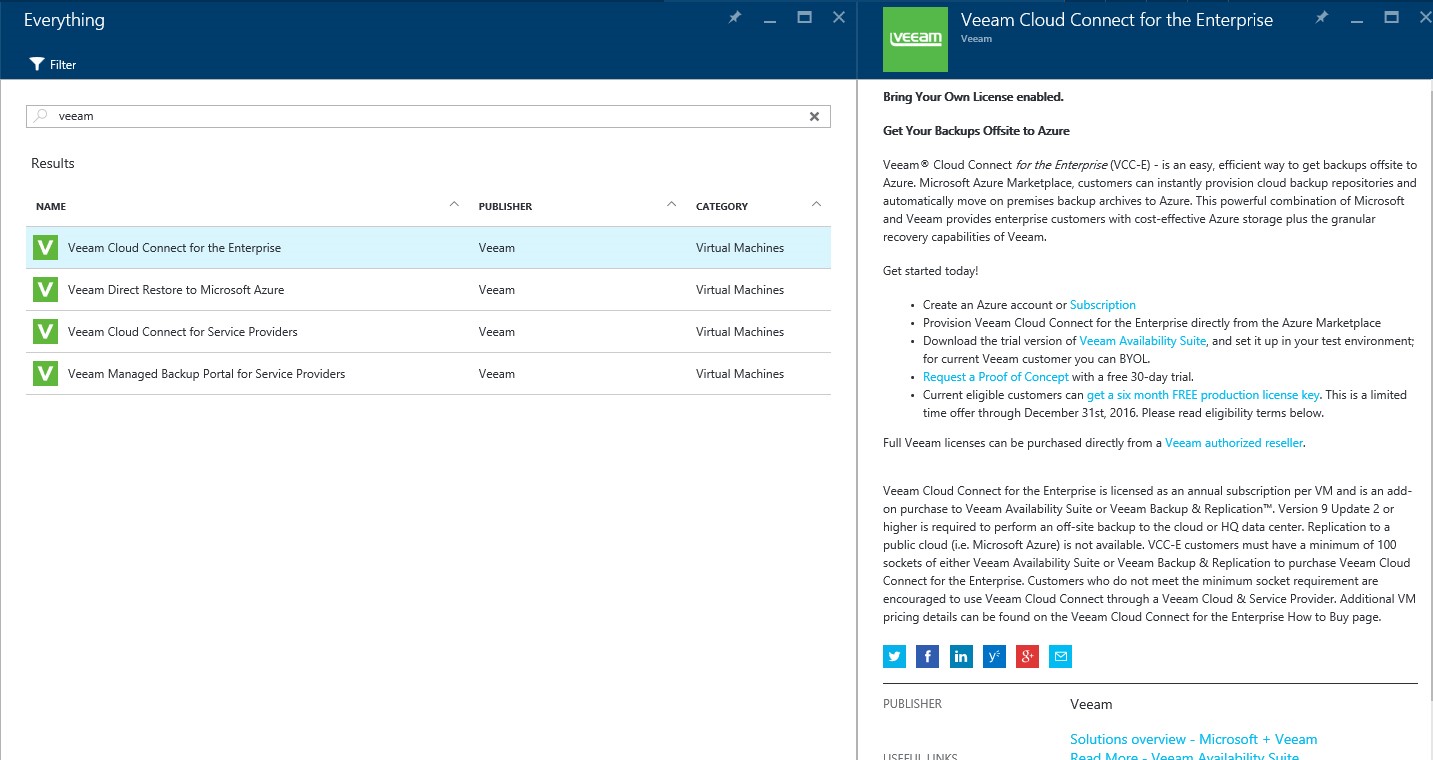
Log into the Microsoft Azure portal, using this link: https://portal.azure.com/. Click the “Marketplace” and search Veeam in the search bar.
To do so, just click the “Create” button.
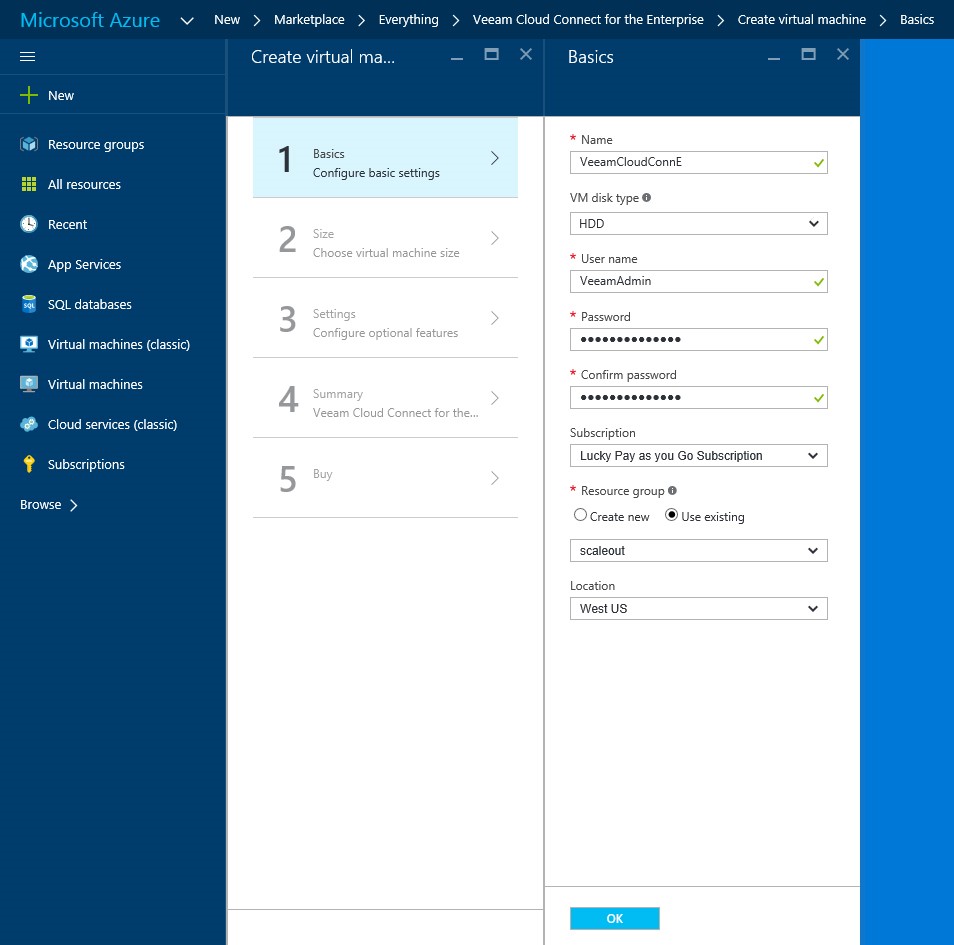
Step1: Creating your Virtual Machine
The creation process presents a form that inquires basic information, like the name of the Virtual machine and such.
It is highly recommended to use a strong password. A password with at least 3 of the following is strongly advised: one lower case letter, one upper case letter, one number, one special character. Also remember to keep the login details (Username and Password) safe with you because you will need them to access the Veeam Cloud Connect VM in Azure.
The completion of this step will lead you to the next step: Choose VM size.
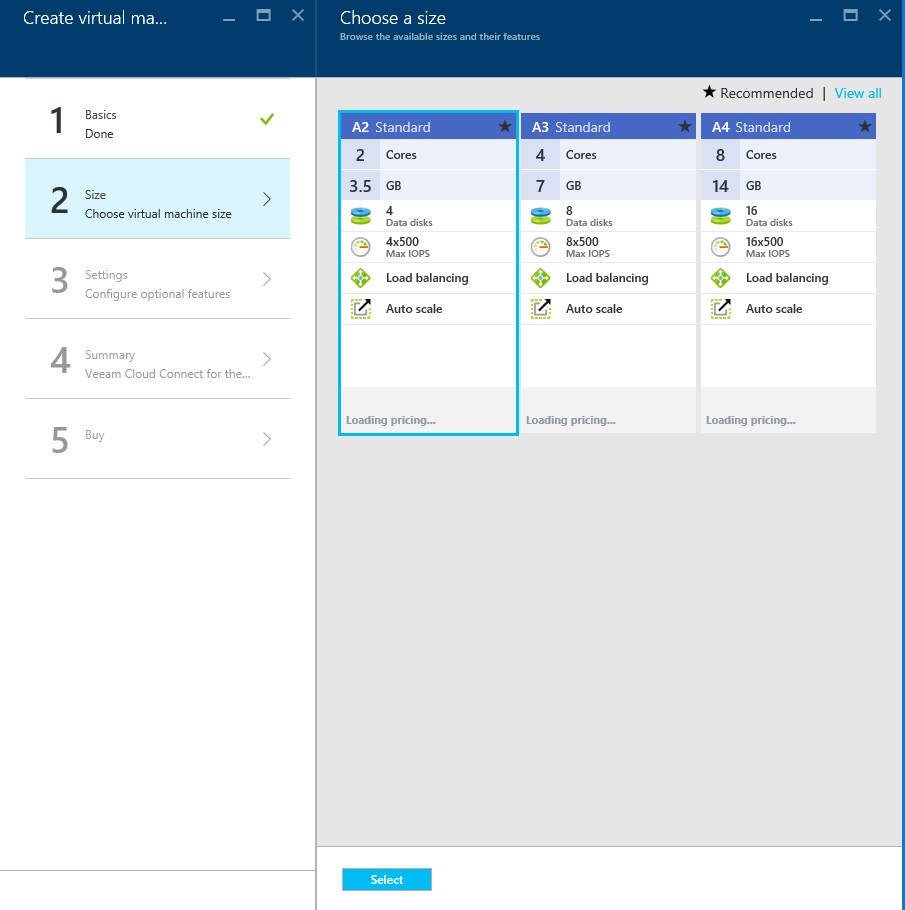
Step 2: Choose Virtual Machine Size
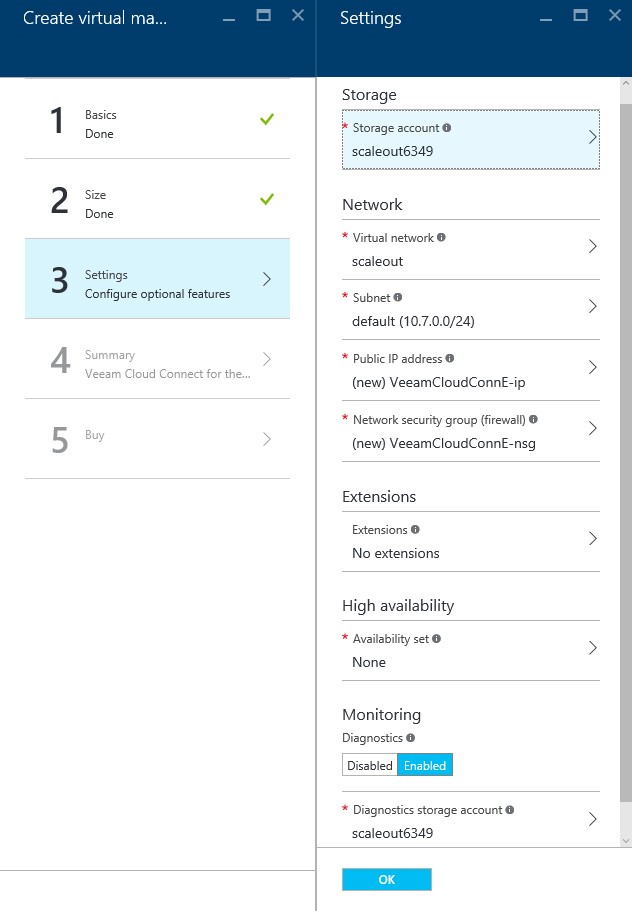
Step 3: Configuration of Optional Features
If you have technical expertise or wish to acquire optional features that you are aware of then you can do so at this step. If not, then go with the default settings and click “Ok”.
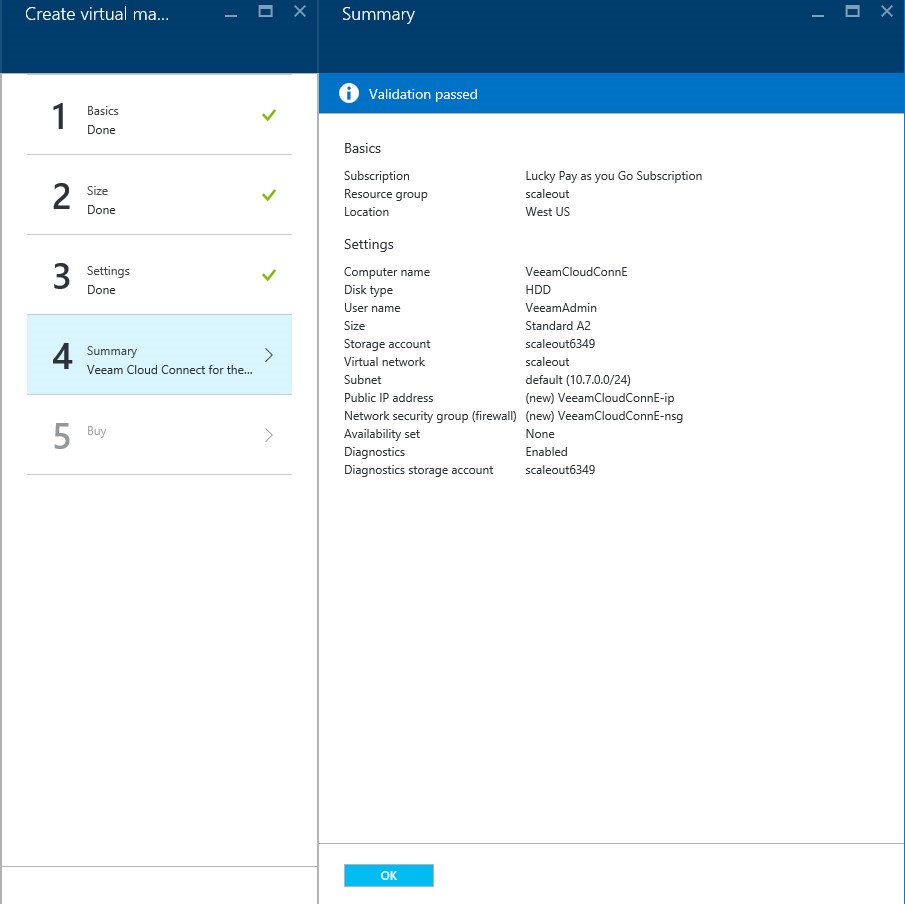
Step 4: Review
This step displays your settings for the VM. You can choose to go back and make changes. If everything is in accordance to your preferences, click “Ok” and proceed to the final step.
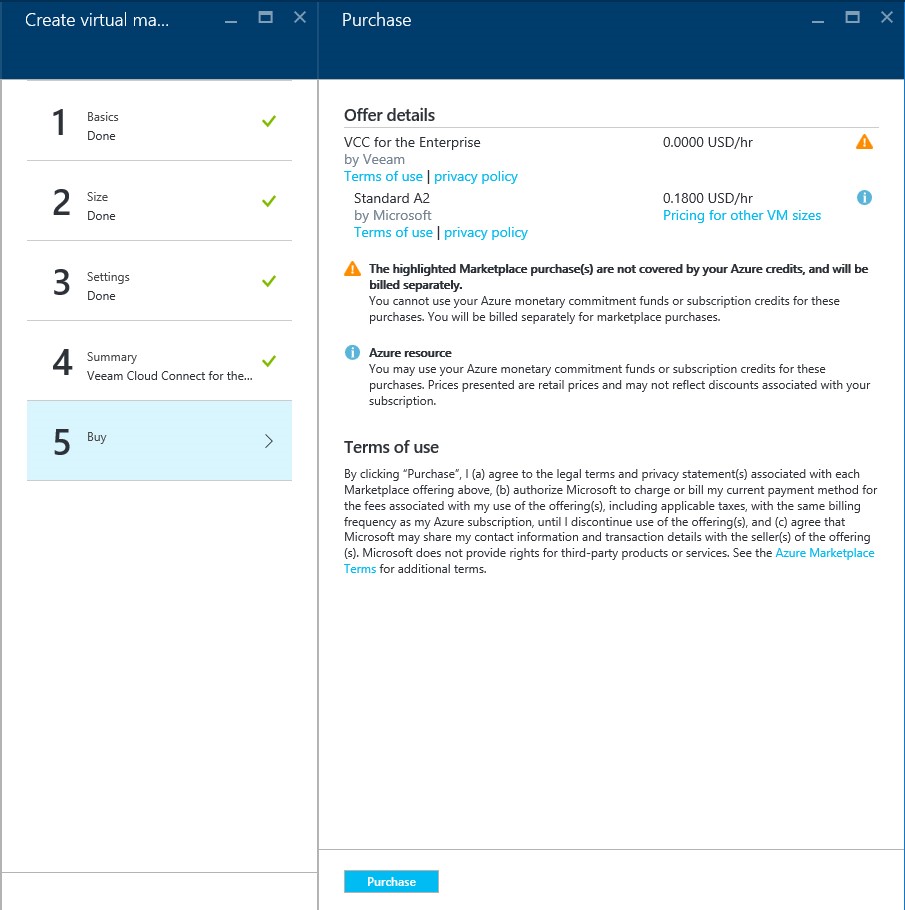
Step 5: Purchase your VM
This step will display the costs for the VM and will also display the terms of use. After reading through the terms of use, you can conclude the process by clicking the “Purchase” button.

To learn about how you can configure this VM, keep checking and another article will follow containing a similar guide to this one about the configuration process.
![Schoolwiselist[1]](https://staging.stonefly.com/wp-content/uploads/2017/09/Schoolwiselist1.jpg)