SAN clusters share storage resources and enhance efficiency and cost effectiveness. Clustering SAN appliances also improves data availability. By clustering SAN appliances, a number of challenges are easily overcome. StoneFly’s SCVM™ software facilitates SAN clustering via target portals.
Target Portals are an iSCSI term for a communications portal between two iSCSI devices. This article is meant to guide you through the setup process of target portals in order to configure a SAN cluster between two SAN appliances.
Target Portals
The StoneFusion operating system features an iSCSI initiator that enables the Storage Concentrator to communicate with other iSCSI devices. Currently, the only iSCSI device supported using a target portal is another Storage Concentrator. To set up a target portal, use the steps that follow:
- Navigate to SAN >Target Portals> Summary. The Target Portal screen appears.
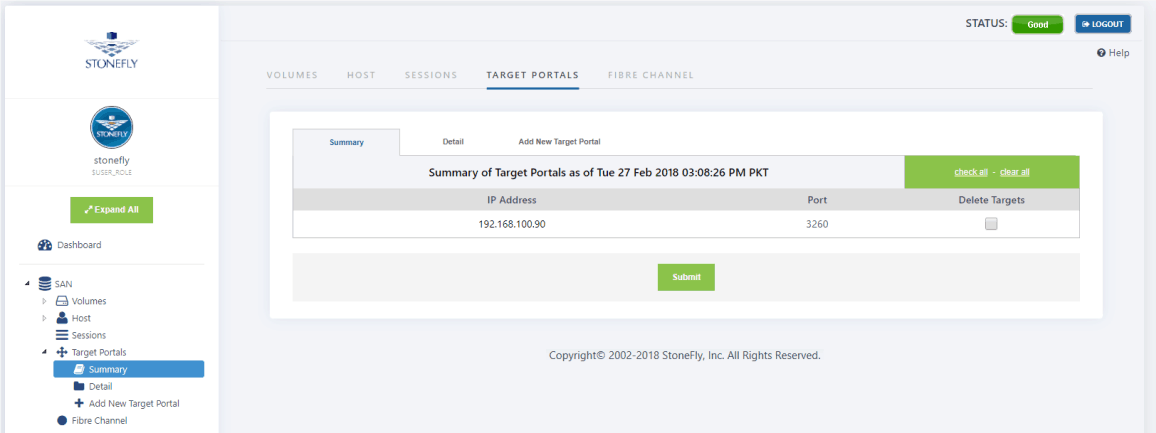
- Select Add New Target Portal. The Add New Target Portal screen appears.
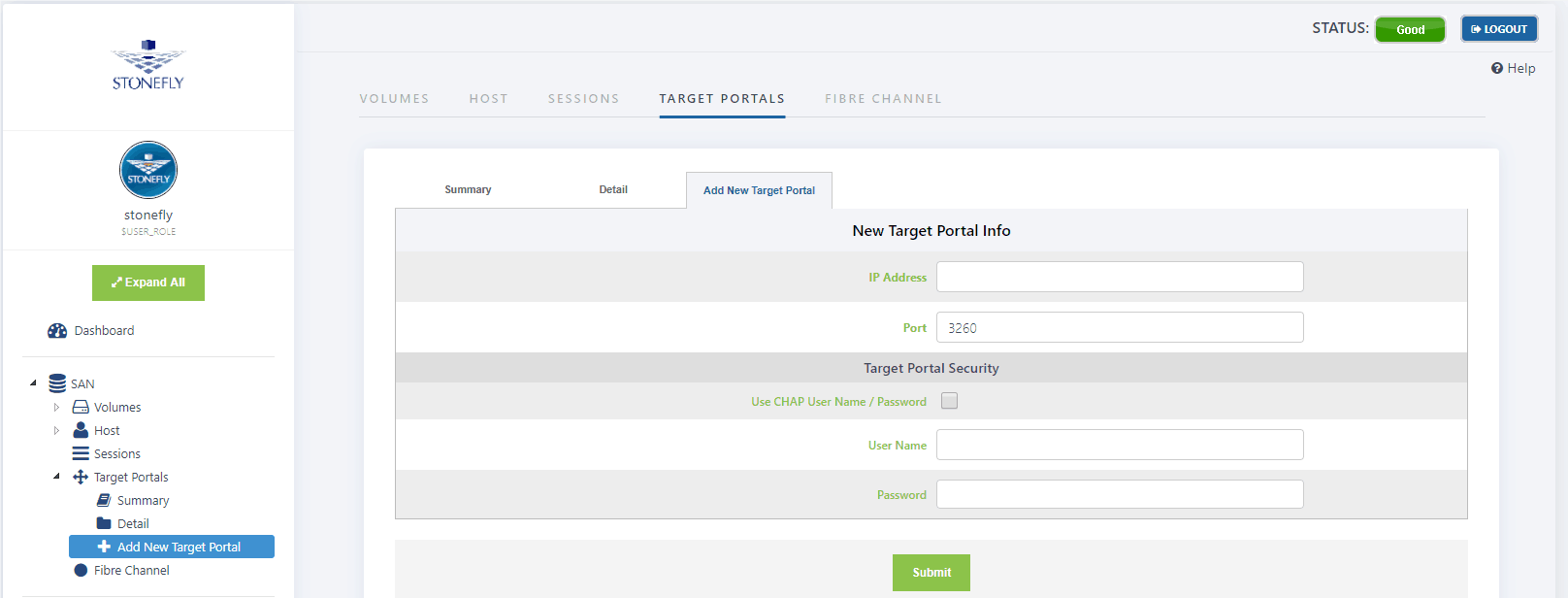
- Enter the IP Address of the Storage Concentrator to be used as a Secondary Storage Concentrator.
- The default setting for Port is 3260, the iSCSI listening port.
- Enter the security settings for the Target Portal, including specifying a CHAP secret.
- Click on Submit.
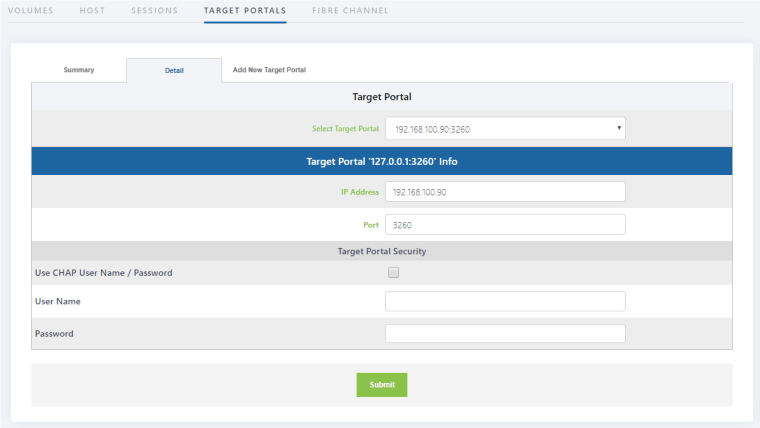
To Check the Status of a Target Portal, click on Detail. The Target Portal Detail screen appears.
- Navigate to SAN>Target Portal > Summary. The Target Portal summary screen appears:
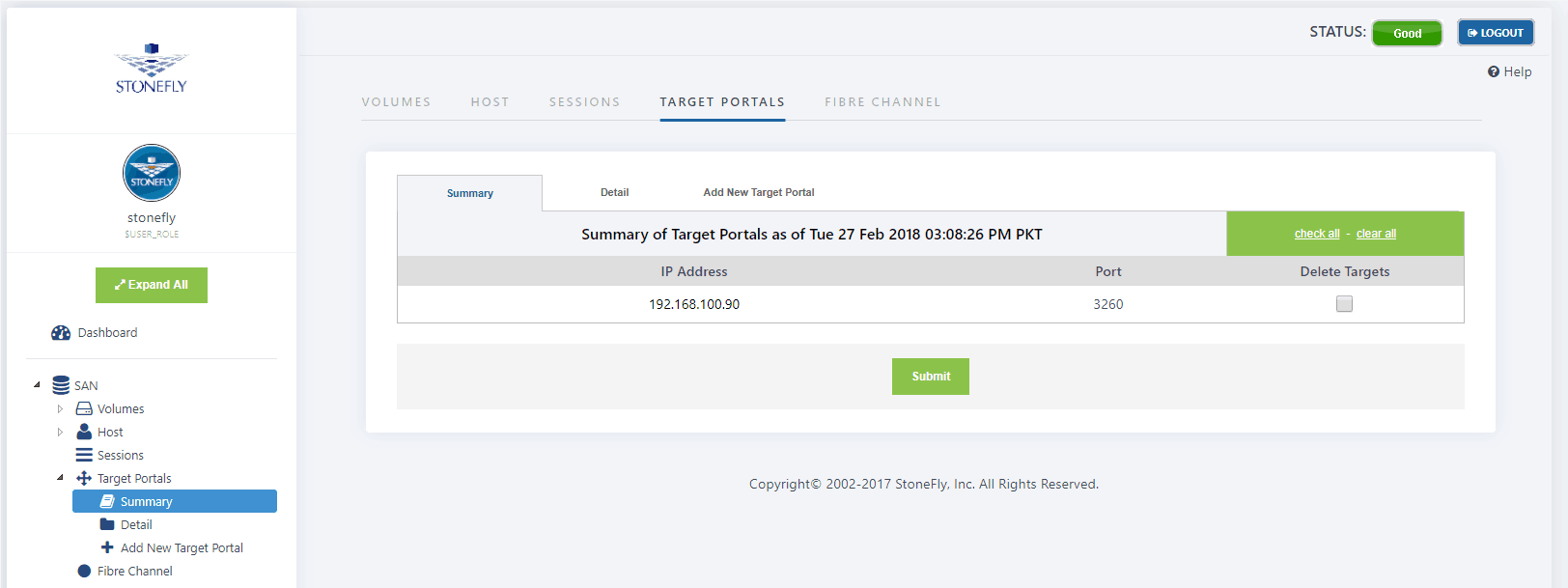
- Select the Target Portal you wish to delete under Delete Targets.
- Click Submit.
Learn more about StoneFly’s award winning software defined storage software SCVM™.










