Data transportability is conventionally defined as the migration of data between applications, computing environments or cloud storage tiers. In the context of cloud technology, data transportability is basically the ability to move different types of data between Cloud Service Providers (CSPs) or between different storage tiers; for instance, migrating data from Amazon S3 to S3-IA. This is also referred to as cloud portability.
At StoneFly, we add more meaning to data transportability. It isn’t simply data migration. StoneFly’s application of data transportability makes it a very useful concept for data protection purposes.
Data Transportability with StoneFly’s Appliances
StoneFly’s innovative Virtual Storage Appliance SCVM™ enables you to dedicate disks that are used to maintain replicas of your mission critical data. SCVM™ delivers snapshot technology, replication technology and other options for the purpose of data redundancy. You can choose which data to be copied to these dedicated disks.
In case of a disaster, be it a natural disaster or an artificial disaster like power loss or hardware failure or ransomware attack, SCVM™ automatically disconnects these disks to prevent damage or corruption to the data stored within these dedicated drives/disks.
These dedicated disks can then be removed from the damaged or dysfunctional appliance and used with another appliance to restore all the data.
To understand this data transportability better, consider the example of StoneFly’s scale-out NAS appliance.
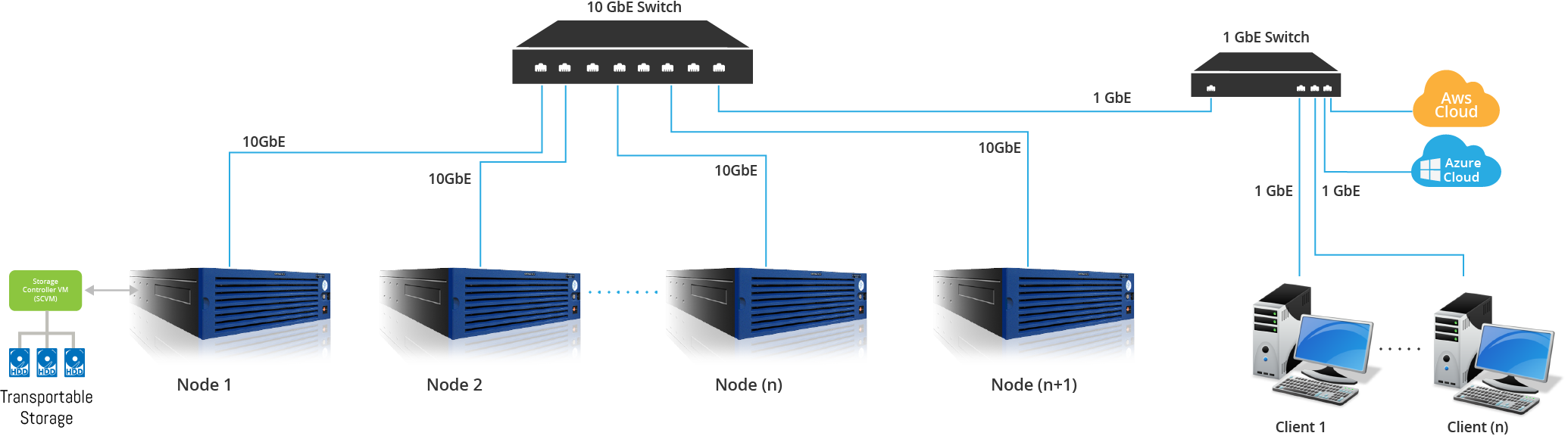
In a scale-out node setup with ‘n’ number of nodes, the transportable storage disks are connected to a single node. Pre-defined mission critical data is replicated to these disks in real time. In the event of a disaster, let’s say all of the nodes are compromised. In this instance, detecting the node failure, SCVM™ detaches the disks from the system. Despite the entire system being affected by a malware or a ransomware, these disks are no longer accessible and thus safe.
Once the disaster concludes, these devices are removed from the scale-out node and added to another similar appliance. Using these transportable storage disks, mission critical data is restored and operations are resumed.
As evident in this example, with StoneFly’s application of data transportability; the storage disks prevent data loss and enhance business continuity.
The necessity of Backup Technology – Despite Data Transportability
Verily, transportable storage disks do prevent data loss but that’s limited to the extent of the data replicated or copied in the disk. This is not a replacement for backup technology. It is strongly recommended to always setup backup services that can ensure data is recoverable and data loss is prevented.
Enterprises can opt to dedicate backup appliances for this purpose or they can setup cloud backup services. StoneFly also delivers software based backup that enables setting up data backups in Microsoft Azure or AWS using Veeam cloud connect.
StoneFly’s storage solutions deliver enhanced data storage and sharing capabilities while StoneFly’s enterprise level backup services efficiently secure enterprise data.
Data Transportability is just one of the enterprise level data services delivered by StoneFly’s appliances. To explore other innovative data services and solutions, contact us and schedule a demo with our experts.
We’d love to hear your data requirements because we can deliver the perfect customized solution for you.
![a7530513820951b61405bb14deeea9f3[1]](https://staging.stonefly.com/wp-content/uploads/2018/05/a7530513820951b61405bb14deeea9f31.png)









