In this blog we will talk about why is it extremely important to have a disaster recovery plan and how DR365-backup and disaster recovery appliance is the ultimate disaster recovery solution. We will also discuss how it ensures that organizations achieve business continuity and what are the million reasons to consider DR365 in your disaster recovery plan.
What is Disaster Recovery Planning?
Disaster recovery planning is a technology-based process that ensures client solutions will return to normal performance as soon as possible after a major event. It is a strategy to keep vital data safe and accessible even in the worst of situations.
Disaster recovery planning ensures that applications stay online continuously to prevent loss of business and ensures the continuity of service for your clients so your good reputation remains intact.
Who Should Consider a Disaster Recovery Plan?
In reality, disaster recovery planning should be important to all businesses who rely on digital data. It is vital for mission-critical applications and crucial for those businesses that store their client’s data.
Nowadays, almost every business is digital and any business that relies on data and has servers, in other words mission-critical appliances should consider adopting a disaster recovery plan.
What Should be in a Disaster Recovery Plan?
A good disaster recovery plan should include the following:
- Scheduled Backups: Scheduled backups are set at regular intervals so, in the case of disaster, files and applications can be quickly restored.
- Offsite Backups: For organizations storing vital and historical information, offsite backups can add a further level of resilience to the disaster recovery solution. Should disaster affect the primary location, your data is accessible and safe at all times via the second location.
- Disaster Recovery Solution: Disaster recovery solutions ensure that even in the most disruptive situation, your business remains up and running with minimum interruptions.
No Disaster Recovery Plan=Potential Cyber-Attack Target
An absence of a disaster recovery plan means total chaos. Studies indicate that 60% of small businesses have experienced cyber-attacks last year. The vast majority did not realize that they had been attacked. The report analyzed 1,069 enterprises and less than 299 employees for the study. Initially, only 13% acknowledged that they had been victims of an attack.
However, after explanation of the types of cyber-attacks ranging from phishing emails, Trojan horses to ransomware; the percentage increased to 58%. This incredible percentage is mostly due to the fact that small businesses either don’t dedicate a budget to or simply do not have a backup and disaster recovery plan.
Cyber-attacks aren’t just targeting industry leaders and large enterprises. Even though large enterprises are still at risk, they are well aware of the value of their data and that is why at least most of them, is not all, are focusing on disaster recovery planning to ensure their data is always recoverable. They have acquired means to keep copies of their data on different locations and means that would enable them to failover in case of a system failure.
In a study, it was found that without any disaster recovery plan, a staggering 57% of small enterprises did not have dedicated staff, solution or vendor monitoring for cyber-attacks in place while an astounding 76% did not have a disaster recovery plan at all. Meanwhile, 57% didn’t have a plan to protect employee data and 54% lacked a plan for protecting client data.
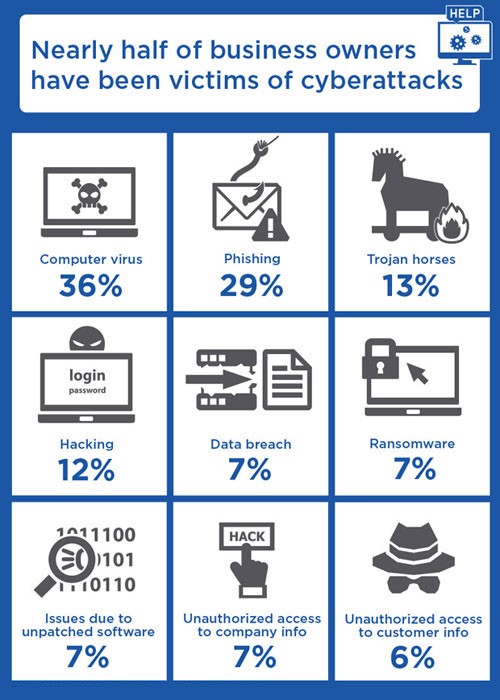
Even though, ransomware consistently makes headline news and is considered a global threat; the sample that was considered in this survey exhibited that only 7% had fallen victim to them. The major devastation was caused by computer viruses and phishing emails. With no disaster recovery plan, there are a number of ways that the two can wreak havoc. Computer viruses can infiltrate the system with tape storage or with the help of a phishing email. This states the importance of a disaster recovery plan.
*Note: Statistics mentioned in this article are extracted from: Nationwide® Third annual Survey of Business Owners
DR365: The Ultimate DR Solution for Your Disaster Recovery Plan
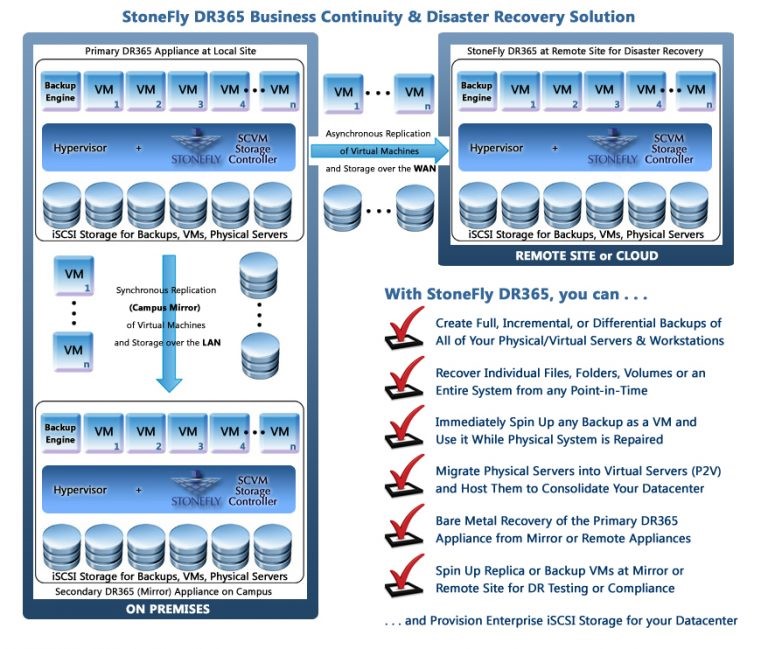
Our DR365 disaster recovery appliance ensures that your business has continuity no matter what happens. It’s a must have in any disaster recovery plan.
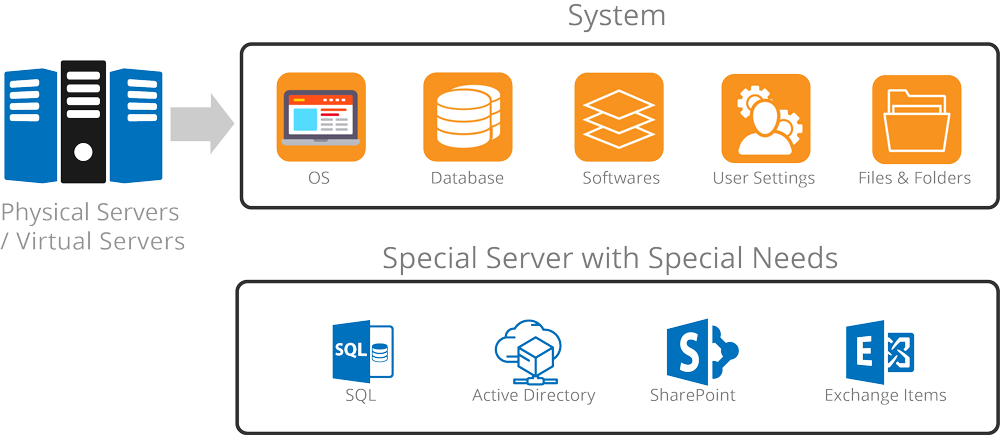
Our solution includes backup and failover of any virtual and physical server with automated-business continuity on-premises to any remote data center, public or private cloud. You can manage all your backup-operations for your datacenter with a single central management-console.
Your data is always 256-bit encrypted throughout the entire backup process for security. It would take a billion years to hack your encrypted data. This level of security meets federal mandates like HIPAA and SOX.
If you have local software or hardware problem, your systems can failover to the appliance and be up and running again in minutes. You then have all the time you need to address the original problem and can fail back to the original or replace the server whenever it is convenient for you.
In the event of a disaster, you can be up and running and have your entire office in the cloud with minimal delay. When your facilities are available again you can failback to your own server at a time while suffering no downtime to your business.
What’s more? You can recover your folders, files, volumes or the entire system from any point in time.
With the StoneFly DR365 in your disaster recovery plan, you can migrate physical servers into virtual servers(P2V) and then host them to consolidate your datacenter. You can spin up replica or backup VMs at mirror or remote site for DR testing or compliance.
Data Backup Features
Encrypted Backups
Data is encrypted at rest with advanced AES 256-bit encryption and data at transit is secured with SSL-encryptions. This encryption makes sure that data is secure and is protected against all kinds of malicious and unwanted access.
Delta-Based Snapshots
Create backup images which can be used to recover to a certain system state and restore lost and corrupted data.
Built-in Ransomware Protection
Our appliance comes with built-in ransomware protection. The intelligent backup software checks for abnormal behavior and prevents attempts at encrypting data, thus making it ransomware attack resistant.
Air-Gaps
Air gaps makes your infrastructure even more secure. Air gaps creates a ‘gap’ between the accessibility of a particular software. So if there is an infection or a virus, there is somewhat automation in the storage resources like your backup files, replication files and others are completely safe from that infection or virus.
Write-Once-Read-Many (WORM)
Provision Write-Once-Read-Many storage repositories that secure your backup files efficiently from many cyber-threats like ransomware, malware, virus, etc. as these files cannot be edited or deleted until the defined period expires.
If you want to know more data backup features of DR365, click here.
Data Recovery Features
Instant VM Recovery with Direct Spin Up
Directly spin up VMs on the DR365 appliance for instant recovery. This helps reduce Recovery Time Objectives (RTOs) and Recovery Point Objectives (RPOs) to less than 15 minutes and hence reducing downtime.
Remote & Automated Recovery
Users can recover remote sites and systems by accessing bootable media and restoring bare metal server remotely over the Wide Area Network (WAN). Apart from this, users can also automate the recovery process.
If you want to know more data recovery features of DR365, click here.
Data Backup & Recovery Services
Block-Level Data Deduplication
Users can efficiently reduce copies of backup files. Deduplication keeps the original copy and replaces other copies with a hash that redirects towards the original data. This way, storage space is optimized and there is more space made available for backups.
Flash Cache
Enhance data accessibility, reduce backup time and recover mission-critical workloads faster with SSDs/flash drives as front-end cache.
Want to know more about the data protection features of StoneFly backup & DR
Best Price, Best Disaster Recovery Plan
An included Backup-Agent License used exclusively for the DR365 allows for agentless-backups of all Virtual Machines including SharePoint, Exchange, SQL, and Active Directory servers running directly on the DR365 appliance at no extra cost.
By reducing storage capacity, organizations will enjoy related cost-reductions in areas including storage management, storage licensing, power, cooling, and datacenter floor-space. Data deduplication makes it much more affordable to store, manage, analyze and house your data with the DR365.
StoneFly’s DR365 is the first business continuity and disaster recovery appliance that supports dual data deduplication engines on the market.
Each DR365 Node can provide anywhere from few Terabytes up-to several Petabytes of storage and backup capacity for your business.
With current deployments in the fields of construction and manufacturing, telecommunication, medical and others, StoneFly DR365 certainly applies to any industry within the market today and makes it a great addition in your disaster recovery plan.
Conclusion
Cyber-attacks are becoming more frequent and are focused on all type of organizations, big or small. Stats above show a staggering high number of cyber-attacks. So in order to protect mission critical data and files, consider DR365 in your disaster recovery plan as it is the ultimate disaster recovery solution.
Contact Us Today!
To schedule a demo or get a quote, contact sales.
Email: sales@staging.stonefly.com
Phone: +1 510 265 1616
Website: www.stonefly.com | www.iscsi.com
Connect with Us on Our Social Media
Twitter: @stoneflyinc
Facebook: facebook.com/stoneflyinc
Youtube: youtube.com/stoneflyinc
Linkedin: linkedin.com/company/stonefly-networks
![banner5[1]](https://staging.stonefly.com/wp-content/uploads/2018/01/banner51.png)









