Old school backup tools are failing to prevent major outages and data loss as they place high demands on the data administrators which in turn are not able to cope with ever increasing data. As the traditional tools become obsolete, IT needs an advanced and versatile solution that delivers high availability, simple replication and restoration and high visibility into diversified virtual environments.
Greater Business Continuity: Do not tolerate any Downtime
Companies have increased their reliance on complex, data-intensive applications to support business and mission critical operations. The growing use of big data, machine data and analytics applications have caused a data explosion. Companies are relying on server virtualization, modern storage applications and cloud-based services to support critical data and applications. To accomplish this, IT is modernizing data centers as well as expanding data storage and leveraging cloud repositories.

- Loss in Employee Productivity: Downtime results in loss of business continuity as the employees do not have work to do. There is massive loss in productivity which takes huge amounts of time to be recovered.
- Loss of Revenue: Any company would lose a great amount of revenue due to downtime. Company starts to face losses as time progresses; for instance, if the website is down, sales cannot be made resulting in massive losses.
- Loss of Consumer Loyalty and Reputation: Making reputation is one of the hardest tasks for any company. Downtime results in lack of access to the services of the company resulting in loss of business with customers. Without cloud backup, it will take too long to get the work environment up and running again, resulting in loss of valuable & loyal customers.
Benefits of Erasure Coding
The benefits of erasure coding are not just levied in the codes themselves. They are helping the world develop greater insight into technologically advanced methods of data protection and disaster recovery. Erasure coding creates mathematical function to describe a set of numbers so they can be checked for accuracy and recovered if one is lost. Referred to as polynomial interpolation or oversampling, this is the key concept behind erasure codes. In mathematical terms, the protection offered by erasure coding can be represented in simple form.
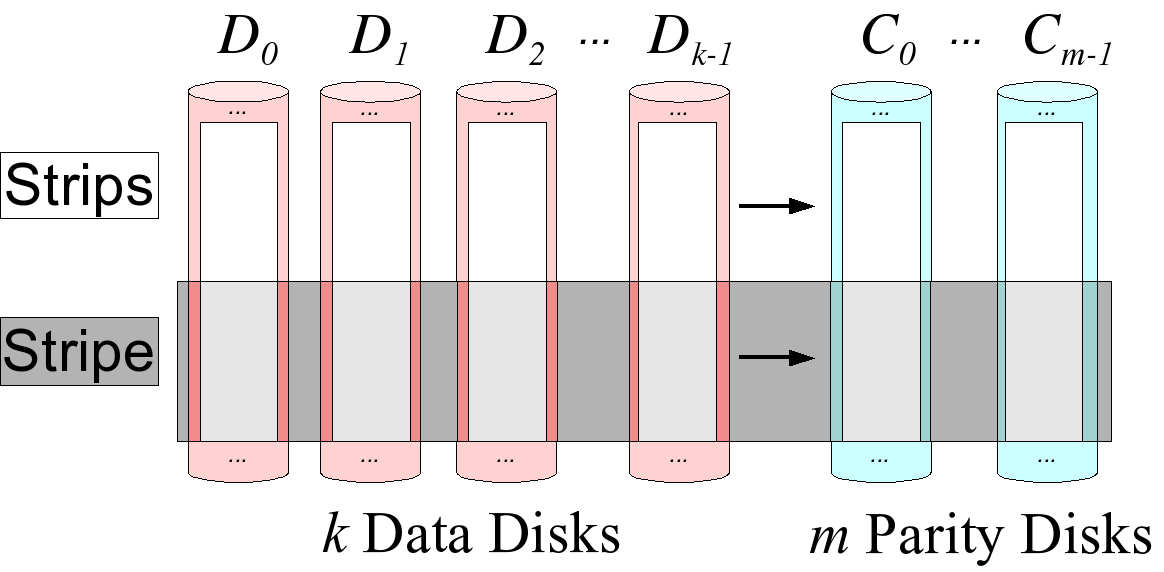
- Storage Space: Increase in the storage space resulting in space saving because of half times the original data required; with the same level of redundancy 3 copies provided. Up to 50% more space is saved using erasure coding.
- Greater Reliability: Data pieces are fragmented into independent fault dummies. This ensures there are no dependent or correlated failures.
- Suitability: Erasure coding can be used for any file size. Ranging from small block sizes of KiloBytes to large block sizes going up to PetaBytes.










