Business continuity surpasses every other element; hence IT experts have to make smart choices with regards to their storage and backup needs. It is a dire need for businesses to be using the most advanced methods of disaster recovery to ensure they always reap maximum advantages from their business.
Traditional and Modern Data Protection and Disaster Recovery
Compared to the old storage methods used, experts are diving into better ways of storage. They are taking steps to ensure that a disaster is mitigated with ease and in the fastest ways to avoid any kinds of down times to the business. One of the up and coming methods of data protection which is used in NAS is “Erasure Coding”. This method ensures that data is saved in such a way that the storage is everlasting.
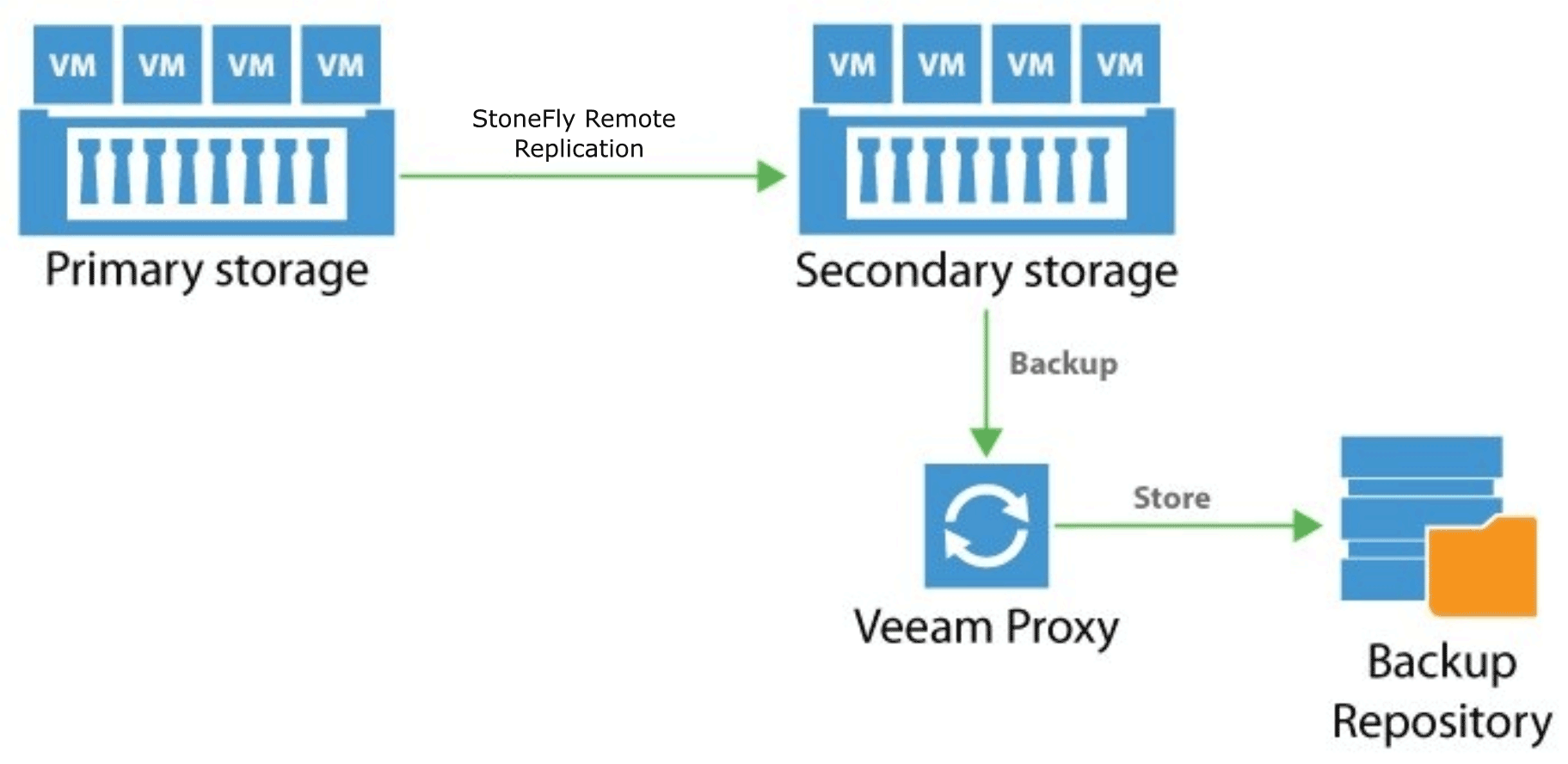
Primary storage must be able to provide you with the tools needed to monitor and control the processes of disaster recovery and data protection. It should give you the flexibility to choose from a variety of secondary storage targets. It must also provide you with the ability to recover and replicate from a backup repository.
Disaster recovery and data protection are key terms for an organization which is looking to reap maximum benefits; strategies are to be made around these two key terms to ensure great profits.
- Disaster Recovery: Disaster recovery is the process of restoring a failed service, application or the operations of an entire datacenter to full operational status following a disaster. This includes natural or human-caused disasters. Having a recovery setup in place is essential for ensuring business continuity.
- Data Protection: Data protection is also known as backup and restore and it is the process of protecting data from loss, corruption or accidental deletion.
What is Erasure Coding?
Erasure Coding is a method of data protection in which the data is broken down into fragments, expanded and encoded with redundant pieces. The data is then stored across a set of different locations inside the cloud or storage medium. Erasure Coding has been proven to be a massive success as it is used for common purpose items like DVDs and cell phones. Erasure codes, which are also known as, forward error correction (FEC) codes, were developed more than 50 years ago.
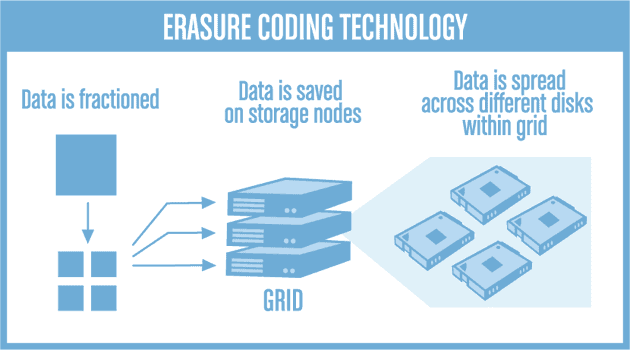
The possibilities of data recovery become unmatched as each brick or disk has redundancy information which can readily be used to reconstruct the data in case of failures; cloud backup solutions provide great ways for this reconstruction.
n = k+m
The configuration of Erasure Coding can be broken down as follows:
n: number of bricks
m: bricks which can go down
k: minimum number of bricks required to reconstruct the data
Erasure Coding allows for the reconstruction of data using redundant pieces of information in the cloud which are dispersed as per the configuration the user wants.










