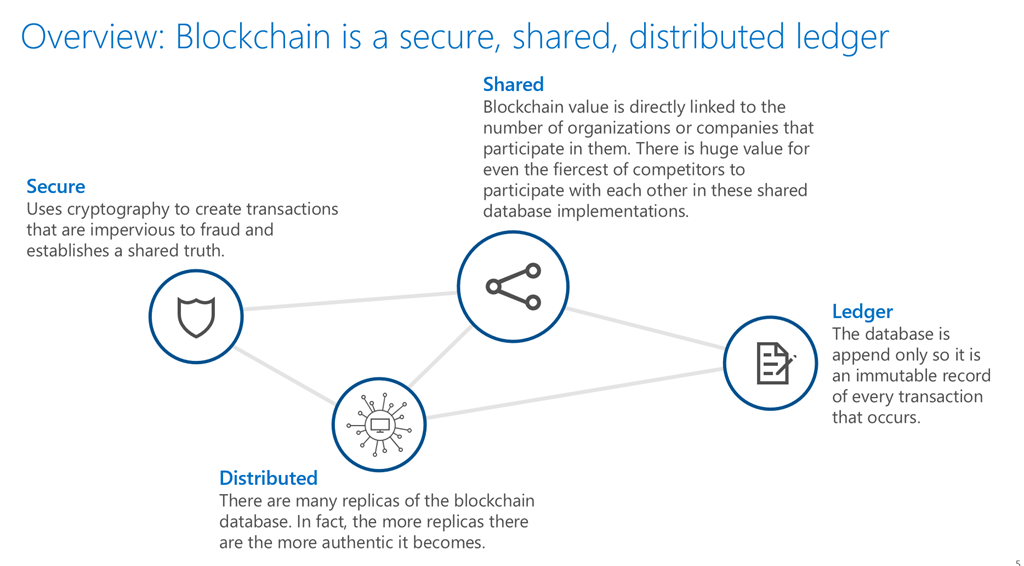
Distributed-there are lots of replicas of the same database that are shared, in fact the more replicas there are just like peer-to-peer the more authentic the Blockchain backup becomes. Ledger-so the databases is append only just like a ledger and it’s an immutable record of every transaction that occurs, so it is never erased, and it is never changed.
Even the most intelligent crypto folks don’t quite remember accounting from high school, so a ledger Blockchain uses a distributed ledger to track transaction. A ledger is a write only database most commonly used in accounting. The digital distributed ledger creates the same copy of the database across all the participating nodes.










