A new Ransomware sample called Bad Rabbit hit Russia, Turkey, Ukraine, Bulgaria, USA, Germany, and Japan on October 24, 2017. Among all of the countries, Russia and Ukraine were hit the most as the infection started through some hacked Russian news website. Russian Media agencies and Transportation organizations in Ukraine were among the first one to get infected.

Bad Rabbit is based on NonPetya or expert code, but it is densely reworked. It also contains parts of other Ransomware, for example, approaches used in HDDCryptor. They also signed the code with fake Symantec security certificate. Another feature of this malicious software is the ability to collect your passwords on the infected computers and download additional malicious modules.
Bad Rabbit relies on a really old malware approach of tricking users into installing a fake Adobe Flash update. This approach still works which indicates that cybersecurity awareness is still surprisingly low. Without proper security and data protection measures, the risk of falling victim to bad rabbit ransomware remains high.
Following are the facts about Bad Rabbit
- It uses pieces of code from Petya/NonPetya
The reason for this ransomware to look familiar is because it is almost identical to last June’s Petya ransomware outbreak. Besides the cosmetic similarities, Bad Rabbit shares behind-the-scene elements with Petya too.
An analysis shows that Bad Rabbit shares 67% of the same code with NotPetya’s DLL (Dynamic link library) which indicates that these two Ransomware softwares are very closely related.
- Distributed as fake Flash update requiring manual installation by a user
Bad Rabbit spreads by media transfer or by downloads on hacked websites. Visitors to compromised websites are told that they need to install a Flash update which of course is not a Flash update but a dropper of the malicious install.
- Spreads across local networks in a primitive way
Bad Rabbit comes with a potent trick up its sleeve. It contains an SMB component which allows Bad Rabbit to move across an infected network and grow itself without user interaction. After infecting the machine, Bad Rabbit attempts to spread over the local network using mimikatz tool which lets you extract windows credentials from Local Security Authority. Bad guys know that “12345” or “password” have been at the top of the password list for years and they continue to be effective.
- Uses system driver for encryption
The ability of the Bad Rabbit to spread is because of a list of simple username and password combinations, which it can exploit to force its way across a network. Weak password list consists of a number of the usual suspects for weak passwords such as simple number combinations.
Technical Details of Bad Rabbit
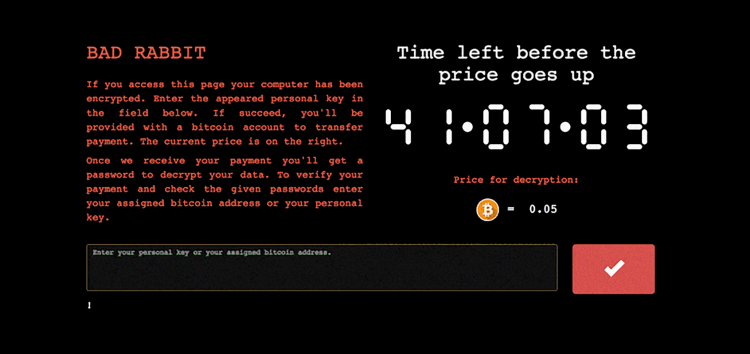
The Ransomware dropper is distributed from hxxp://1dnscontrol[.]com/flash_install.php. After that, the user downloads flash player.exe file, which needs administrative privileges in the system. If started, the dropper extracts a file-level encryption module infub.dat and a disk level encryption module dispci.exe.
Bad Rabbit uses two types of encryptions- file and disk level. It does not duplicate ckhdsk.exe like NonPetya did to hide encryption. Bad Rabbit launches file level encryption (infpub.dat via rundll32), if it finds enough files to encrypt. After starting encryption, it creates tasks in scheduler for launching dispci.exe to encrypt drives and then forces the system to restart. After the first restart, dispci.exe writes an extended loader on the disk which will get all the control via malicious MBR later. Finally, the whole disk is encrypted with a driver, MBR is written and the PC will restart again to display a ransom message demanding bitcoin.
Who is behind the attack?
Till now, it is still unknown who is distributing bad rabbit Ransomware, but the similarity to Petya has led the researchers to suggest that Bad Rabbit is made by the same crime group. One interesting thing about the hackers is they appear to be a fan of Game of Thrones. The code contains reference of Viserion, Drogon and Rhaegal, the dragons which feature in television series, although that doesn’t help identify the attackers, researchers are working on it.
StoneFly Customers will never pay a penny to recover from Ransomware, will you?
At this point, it is unknown if it is possible to decrypt files locked by Bad Rabbit without paying the Ransom. One of the most authentic ways of securing your data is Cloud Backup. By the time an organization is going to realize that there is an attack most of the systems by then will already be affected, so keeping a Cloud Backup can be very useful.
The Best protection against Ransomware Attack is a strong Backup. StoneFly DR365 is a complete Data center Backup solution appliance for all physical and virtual servers. StoneFly DR365 users do not worry if they are hit by a Ransomware attack, as their data is secured in multiple locations and Ransomware does not have access to the data. The StoneFly DR365 is the only data center backup appliance that comes with automated offsite Backup connection to Amazon AWS Cloud and Microsoft Azure Cloud.
The StoneFly DR365 uses Storage Concentrator Virtual machine (SCVM) to provide server and storage consolidation, data protection and disaster recovery into a single platform.
The user has the freedom to set the data access option from read only or read/write storage. The StoneFly SCVM provides Flexibility in Data Backup. The Snapshots created by the SCVM are Block based, which create a point in time backup delta from only blocks that have changed from the last snapshot. SCVM Snapshots can be set to read-only which helps in data protection against the Ransomware, as the data can not be reached or changed by hackers.









