Data security is one of the prime reasons why enterprises and domestic users explore cloud backup services. Public cloud service providers such as Amazon and Microsoft provide multiple options to enable the creation of logical containers.
These containers can hold documents and data and each can have different level of permission, facilitating access control and management. However, despite the options most users (domestic, enterprise and even governments) don’t take security seriously.
A recent survey conducted in May 2017, stated that 60,000 US government files were in Amazon S3 with public access. Among this data, a total of 28 GegaBytes (GBs) contained unencrypted passwords owned by government contractors with Top Secret Facility Clearance.
The accessibility of sensitive data imposes the necessity of a management service that detects these holes in security protocols and appropriately respond to them.
Amazon Macie: Artificial Intelligence Security Service
Amazon Macie is a machine learning-powered security service. The artificial intelligence discovers, classifies and protects sensitive data in Amazon Web Services (AWS). Macie identifies sensitive data as Personally Identifiable Information (PII) or intellectual property. Macie provides you with a dashboard that offers visibility into how this data is being accessed or relocated. The service continuously monitors data access activity for irregularities and creates detailed alerts when a risk of unauthorized access or unintentional data leak is detected.
Macie develops an understanding, by monitoring your cloud backup, of where your sensitive information is located and how it’s usually accessed. This includes information about user authentication, locations and times of access. Initially, Macie creates a baseline and then it actively monitors for irregularities that indicate risk or distrustful behavior. Macie also provides you the ability to easily define and customize automated remediation actions.
How Amazon Macie works
Macie has an interesting way of arriving at the classification and security mechanism of data. It relies on three data sources:
Data: Macie reads the actual data and extracts keywords from it from file formats such as Microsoft Word, Excel, .txt files. Macie compares file extensions to evaluate the security level of data. For instance Macie will move a .pem file higher in risk level then a .txt file.
Metadata: Macie also considers the information associated to a file, S3 object, and buckets when classifying and determining the security level.
Access Information and Credentials: Macie also utilizes Amazon CloudTrail. CloudTrail is a service in AWS that logs approximately every Application Programming Interface (API) request made. Macie uses these logs to capture object-level API activity of S3 objects. Macie also acquires information related to users and roles from Identity and Access Management (IAM).
Benefits of Amazon Macie

Data Visibility
Macie is capable of identifying data with high business value including programming languages to detect source code, database backup formats, logging formats, API key formats and credentials.
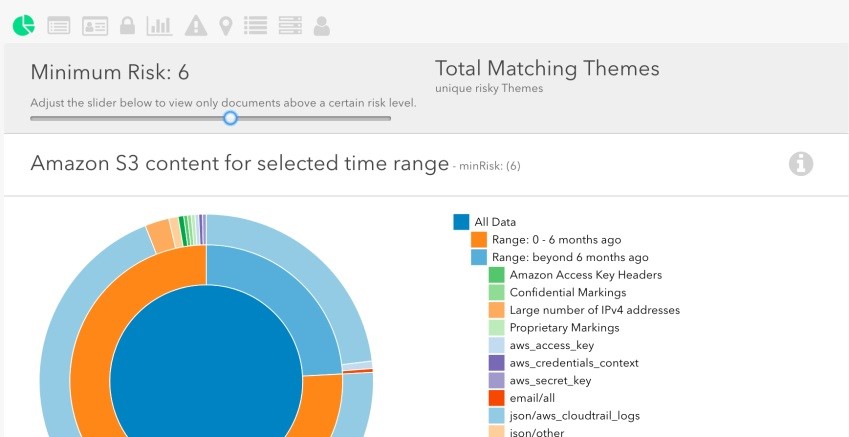
With machine learning, Macie classifies your Amazon S3 objects in a way that provides maximum visibility into your S3 environment. The classification also facilitates ease of access and the speed of operations.
User Behavior Analytics
Macie comes with a user behavior analytics engine. This engine helps identify risky or suspicious activity with AWS service API calls and access to high value content. This engine is also able to detect sudden impulses in high risk API activity. If there is a specific file or data that’s being accessed at irregular hours from various different locations; then the engine will detect this anomaly versus the user’s usual behavior.
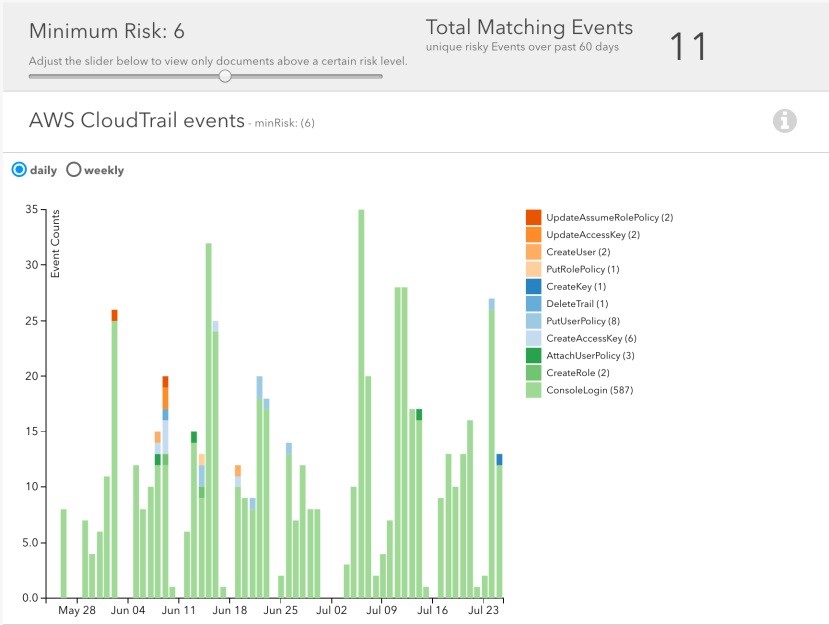
As Macie is also aware of sensitive and important information, increase in access to this content may indicate possible data loss; it is also able to detect this pattern.
Automated Workflows
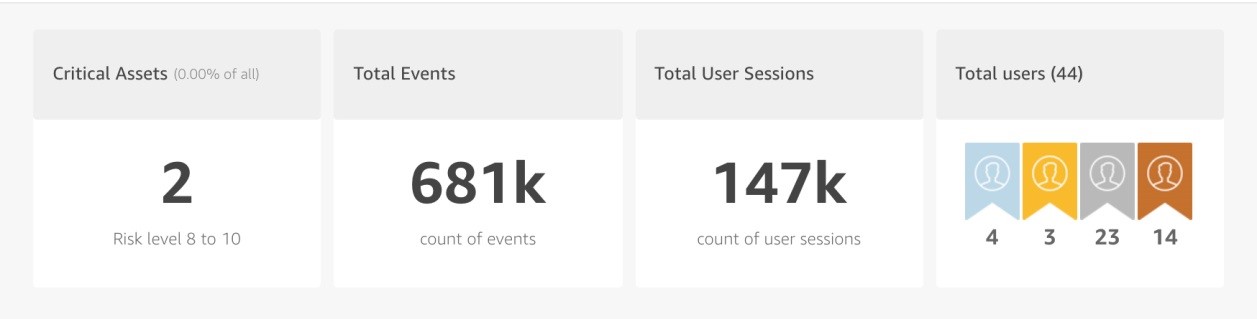
Amazon Macie facilitates integration with Security Information and Event Management (SIEM) services and Managed Security Service Provider (MSSP) solutions. These services and solutions support security and compliance use cases such as: compliance rule-set creation and modification, alert handling, reporting and configurations for objects in S3, and application and login events.
Automatic Alert Categories
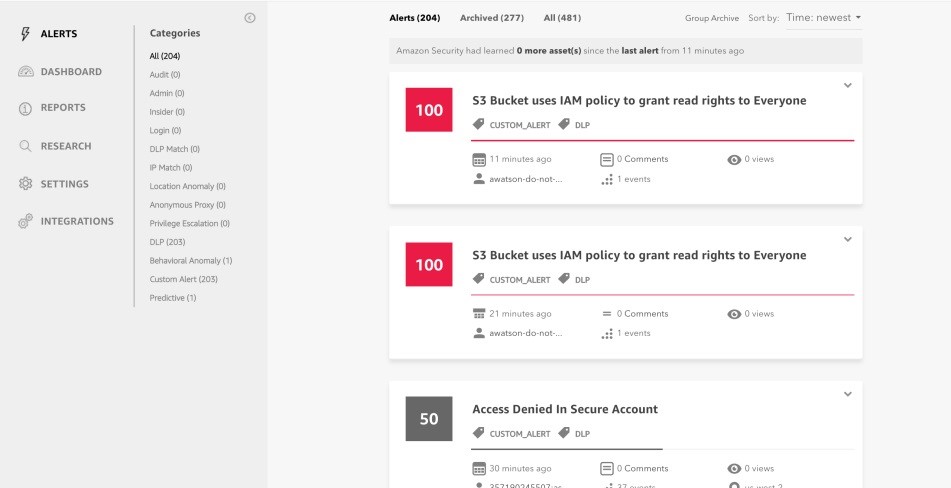
Macie provides 20 alert categories, these categories help offer early warning on security and compliance use cases such as high risk data events, unencrypted backups containing credentials, API keys and credentials being stored within source code, and early stages of an attack including behaviors indicating lateral movement, back-door accounts, persistence mechanisms, and enumeration of role privileges.
Conclusion
Amazon Macie is the immediate solution to the security issues observed by the survey (mentioned above). Enterprises and Governments can employ Macie to classify their data and secure it, preventing data leaks. StoneFly’s backup appliances provide cloud gateways into Amazon’s cloud and services. Besides gaining unlimited, secure and reliable on-premise storage with StoneFly; you can also extend to the cloud and evolve into a hybrid cloud solution which is capable of properly sorting and protecting your data using Macie.










