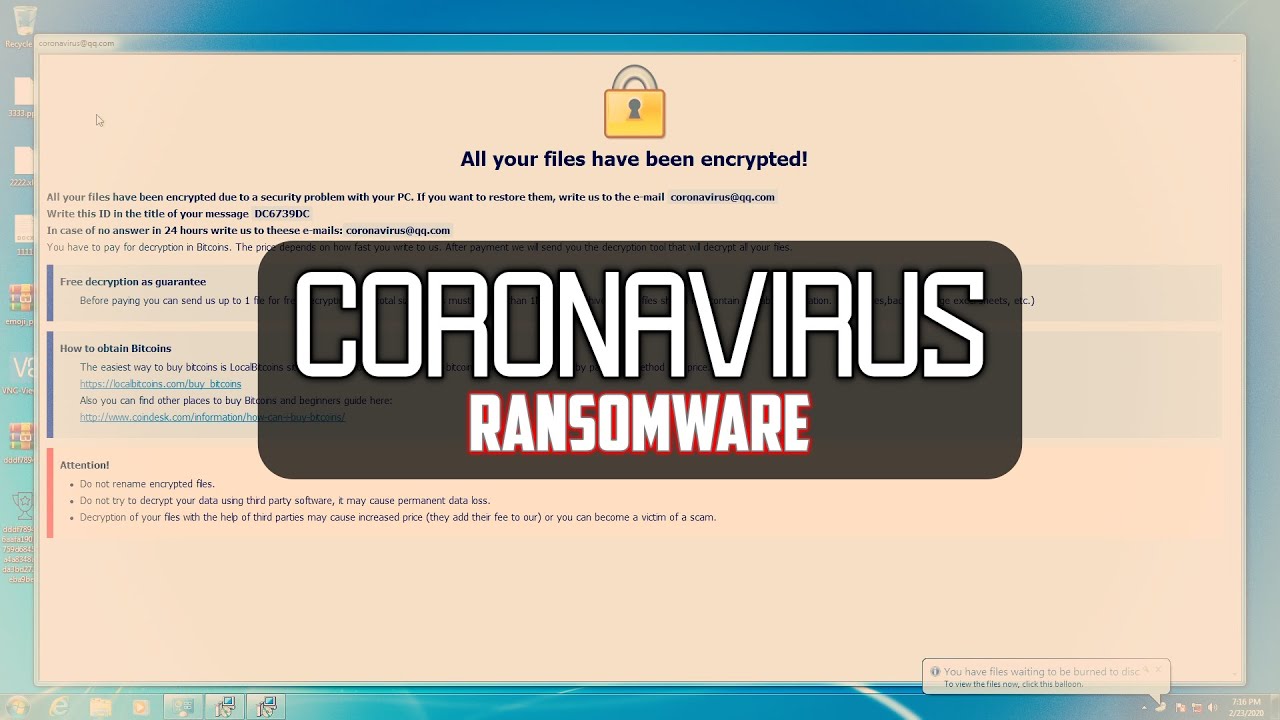
Coronavirus claims more lives with each passing day. The pandemic has affected more than 200 countries with thousands of cases appearing daily. While the world worries over health concerns, preventive and protective measures from Coronavirus, scammers and hackers have already begun to make their move in the form of phishing emails.
Every time something “global” happens, for instance the finale of a popular TV show or a natural disaster, scammers capitalize on it using socially engineered email attacks (phishing scams).
What are phishing emails and how are they related to Coronavirus?
As everyone is concerned about Coronavirus, scammers are using this as an opportunity to send emails that pose vital information about preventive measures. This email is tailor-made to strike nerves and get the recipient to download an attachment or click on a link.
The damage dealt by phishing emails vary. Clicking on a link in or downloading an attachment from a phishing email can lead to the following scenarios:
- Compromise login credentials of the server, workstation, and email account, etc.
- Successful ransomware attack – ransomware infection that compromises all systems and servers connected to the network
- Compromise Personally Identifiable Information (PII) such as social security information, account information, credit card information, etc.
Such type of phishing emails aren’t just related to the Coronavirus. As mentioned earlier, similar attacks have been witnessed in the past. In fact, phishing emails are one of the primary reasons of data breaches, malware or ransomware infection, and data loss.
Damage Dealt by Phishing Emails in the Past
Here are some phishing email statistics that are sure to raise some serious concerns:
- 70% nation-state or state-affiliated data braches involve phishing (Source)
- 66% of successful malware infections are caused via email attachments (Source)
- 64% organizations have experienced phishing attacks in the past year (Source)
- 21% ransomware attacks involved phishing scams (Source)
You can find information about how to protect yourself from coronavirus from authentic sources such as the World Health Organization (WHO) and stay safe.
Recent COVID-19 Scam Attempts
Here’s a brief list of COVID-19 scam attempts experienced by businesses worldwide:
COVID-19 Scam Email that says “You Might be Infected”
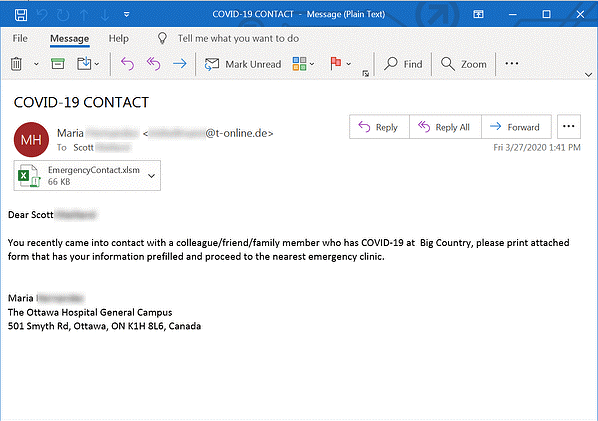
Screenshot of the COVID-19 Scam Email with Excel Attachment (Source: KnowBe4)
Email that says “you’re infected” with an excel sheet email attachment. When downloaded, the sheet prompts users to enable contact to see the sheet details. When allowed, the sheet infects the system with a virus using a Trojan downloader.
COVID-19 Scam Email Disguised as Official Correspondence from SBA
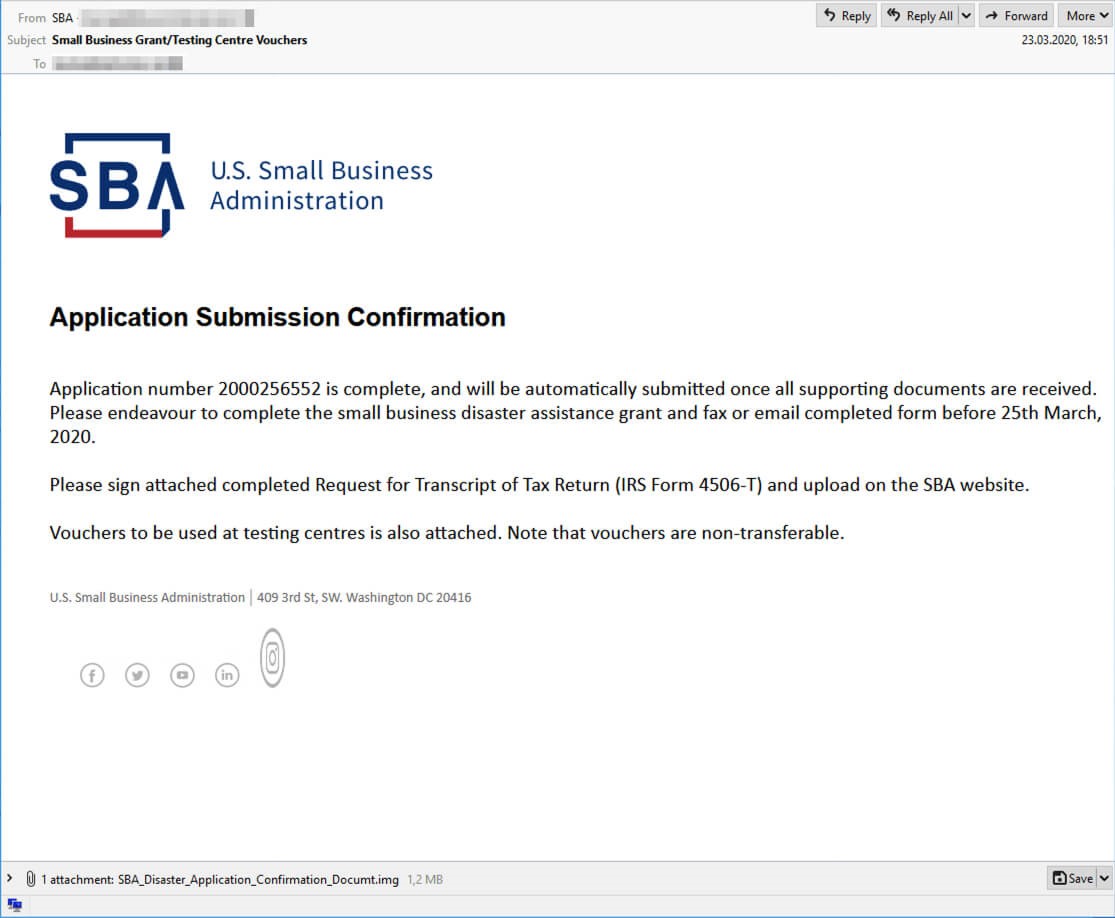
Screenshot of the COVID-19 Scam Email Disguised as Official Correspondence from SBA (Source: IBM X-Force)
Email disguised as official correspondence from the Small Business Association (SBA). This is a particularly socially engineered scam that follows the same procedure as the SBA. It claims to provide SMBs with application number with which they can apply for a “small business disaster assistance grant”. All they needed to proceed was sign an attached document. When complied however, the email downloads a sample of the Remcos remote access Trojan (RAT).
COVID-19 Scam Email Targeted at Canadian Businesses
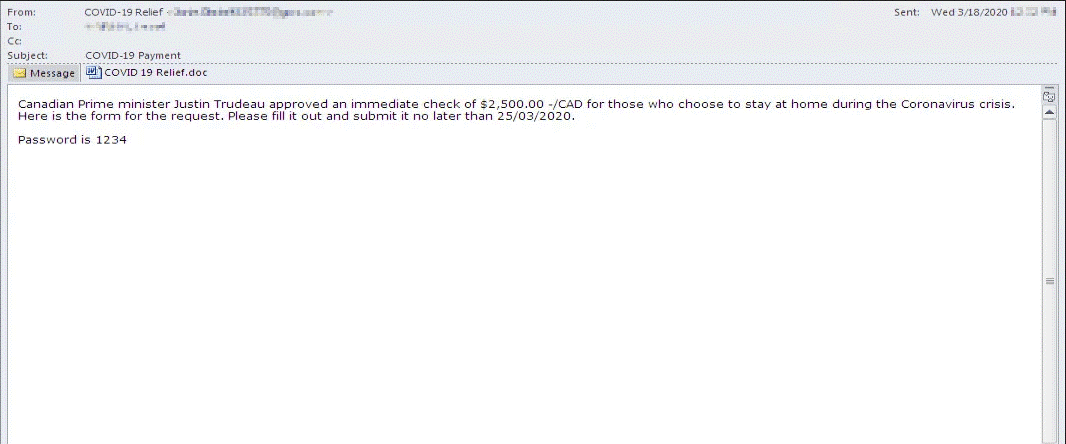
Screenshot of COVID-19 Scam Email Disguised as a Grant for Canadian Businesses (Source: IBM X-Force)
Scam email targeted at Canadian businesses. This COVID-19 scam disguised itself as a grant from Justin Trudeau for businesses who decided to stay at home during the Coronvairus crisis. The email prompts users to download an attachment that is to be submitted as a voucher to claim the grant. When downloaded however, the macro code in the document infects the system with Zeus Sphinx malware.
Coronavirus-themed Wiper
Screenshot of coronavirus.bat (Source: SonicWall)
While many nefarious individuals focused on phishing scams to collect personal information others simply made business data inaccessible for their victims. Such was the case with the coronavirus-themed wiper: “coronavirus.bat”. This particular coronavirus installer disabled access to the Windows Task Manager, User Access Control (UAC), and options for modifying the desktop. When installed and the system rebooted, the wiper loaded a binary responsible for overwriting the MBR.
But how can you, as a business owner or data owner, make sure that your data is safe from such phishing emails and ransomware attacks? StoneFly can help you with that.
How to protect data from Coronavirus phishing emails & ransomware attacks?
There are two major ways to protect your data from Coronavirus phishing emails and consequent ransomware attacks:
- Educate your staff
- Everyone should have basic knowledge of phishing emails and how to identify them.
- Write and share a “dos and donts” instruction manual that clearly defines what people need to do when they get a phishing email
- Hold regular webinars and training sessions updating everyone about the latest types of phishing attempts
- Back up your mission-critical data
- Use reliable enterprise backup software: Veeam, Acronis, etc.
- Store redundant backup copies on multiple locations and multiple storage media
- Set up disaster recovery for production environments
How StoneFly can Help
We offer purpose-built backup and Disaster Recovery (DR) solutions that include:
- High performance backup and DR appliances
- Backup Software + Cloud Storage Repositories for Backup Data Storage
- Veeam Cloud Connect to Azure (backup & direct VM spin up)
- Veeam Cloud Connect to AWS (backup & direct VM spin up)
- Veeam Cloud Connect to StoneFly Cloud (with real-time replication support)
As the leading innovator in the backup and disaster recovery industry, we take pride in our ability to build economical, high performance, and robust systems custom-built for enterprise workloads.
To learn about how StoneFly can help you with your data protection needs, contact us.
Conclusion – Don’t Let Coronavirus become the Reason for a Successful Ransomware Attack
Coronavirus is a real worldwide concern. Opportunistic scammers and hackers are using it to attack enterprise infrastructure using phishing emails and ransomware.
While this is the time to focus on your care and stay safe from Coronavirus; you cannot allow scammers to hold your data for ransom or compromise your business data in any other way.
So start taking pre-emptive measures right away! Educate your staff and back up critical information using StoneFly’s enterprise-grade backup and disaster recovery solutions.
Related Resources:
Listen to the StoneCast Session about COVID-19 Scams
Download Audio | Play in New Window