Governments are protecting the interests of organizations in various industries by providing protection from cyber-attacks. Moreover, governments also have to protect their own national infrastructure such as the national power-grid. Cyber-attacks have become an occasional occurrence in the world of big data. Organizations which do not have proper plans and strategies for disaster recovery and business continuity face the most financial losses.
Unanimous decision has been made globally that there is a need to improve cyber security; it has become vital in today’s dynamic world which is filled with threats. Governments around the world are taking the responsibility to solve the issues related to cyber-attacks. Experts think the same that government has to step in today, but cloud based solutions of the private sector do solve issues related to cyber security efficiently and effectively.
Three Stages of Cyber Security
A question arises, how can a certain organization come to know of the problem that needs to be solved in the corporate environment? Cloud security can be done in three stages for the identification of the problem in the corporate environment:
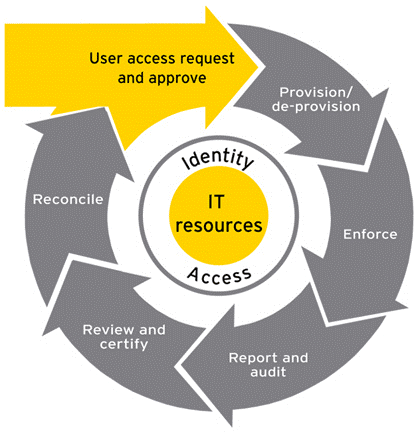
- Monitoring Data: There are AI algorithms in the corporate environment which keep track of the normal system behavior. Any deviation from this normal system behavior creates an alarm which is then monitored by the cloud experts or the cloud security experts. After establishing a threat or problem in the corporate environment, cloud security experts’ move on to the next step.
- Gaining Visibility: Cloud security experts’ need to understand what or who caused the problem in the corporate environment. So, certain tools are needed which give them the ability to look into the data to find the event which caused the problem.
- Managing Access: After establishing what the problem in the corporate environment is, tools have to be used to pin point the person who caused the problem. The managing access stage can be used to wipe out that user from the corporate environment.
Amazon AWS Tools for Greater Cyber Security
With disaster recovery in the cloud, the global world is working overtime to provide greater data security. Veeam Cloud Connect to Amazon AWS provides faster data transfer and uses encryption keys for data security. AWS provides cloud backup services with in depth cloud security.
- Monitoring Data: AWS provides a service called “CloudWatch”. It is a cloud monitoring tool which allows the user to monitor AWS resources (EC2 instances and the likes) in many ways like network in, network out and also monitor the traffic which comes on to the instances. CloudWatch gives the users the added ability of creating alarms. The alarms allow the user to instantly track the deviations from normal system behavior by escalating the event and alerting the user of the deviation. Experts can easily roam around the cloud and detect the problem.
- Gaining Visibility: AWS allows tracking the activities happening in the entire environment and the users’ AWS account. A service known as “CloudTrail” is provided which is a logging service; it allows logging the history of API calls. There is ease in setting a timeframe to monitor the entire environment and know what has been going around the corporate environment. Say a hacker gets access to a system; the tool will help in easy identification of the place from where the system was accessed. It can easily help in the isolation of the problem and hence more clarity in pin pointing the person who caused the problem with the log maintained. Say there are spam messages originating from a particular attacker, it can be identified who it is and hence easily wipe out the guy from the system.
- Managing Access: The last step is to remove the irregularity from the environment; removing the person from the corporate environment. First of all, the experts got to know where the spam originated from and now they start wiping it from the system. Then comes the step of prevention, where the cloud security experts have to make sure that a user doesn’t do it again. The user is identified from the source and using managing access the cloud security expert will be able to remove the threat once and for all. AWS “IAM (Identity and Access Management)” is the service which allows the users to do so and totally eliminate the threat from the corporate environment. AWS IAM authenticates that particular service. Authorized personnel will be the root user and be able to do anything. But all the employees will not have entire access; one specific employee might be capable of tracking down the problem and ending it, but how will you provide that employee granular access? Well, AWS IAM allows for granular permissions to be given to employees and gives a private file to secure the access to AWS instances.










